The pandemic has changed the world of commerce almost irreversibly. 16% of companies across the world are operating without an office. Teams scattered across continents collaborate efficiently to get work done.
In fact, the COVID-19 pandemic has created new opportunities for cybercriminals, and businesses need to be vigilant. A survey conducted by the World Economic Forum found that cyberattacks and data fraud rank third among the Top 10 worrisome risks for companies.
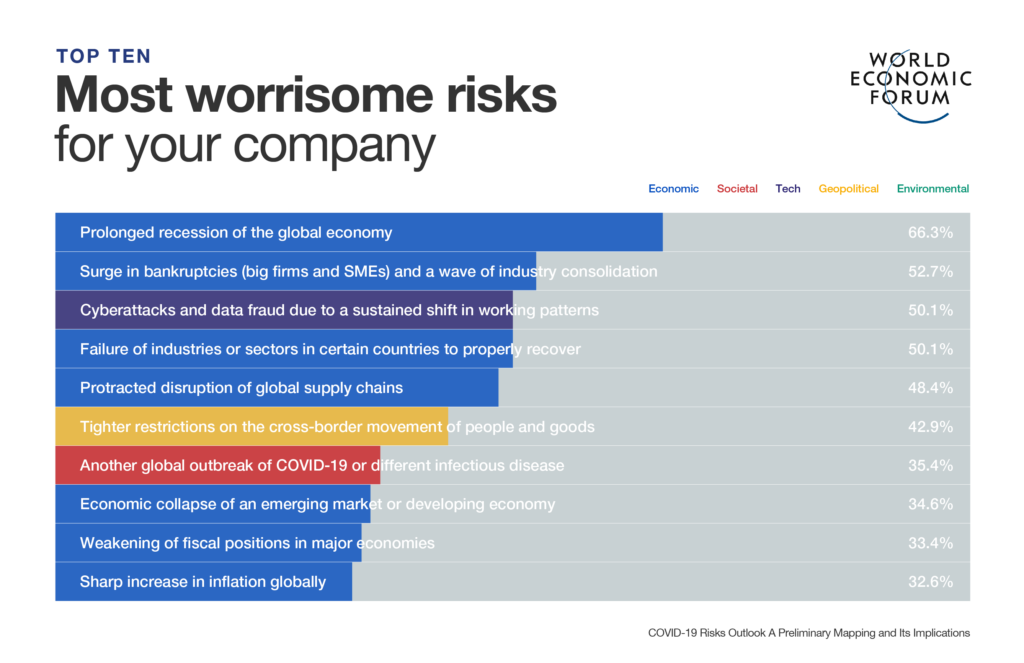
Consequently, opportunistic cybercrime had a 33% uptick in 2021. The number of ransomware attacks doubled between 2020 (304.64 million) and 2021 (623.25 million). Leaders have responded well with a downpour of investment in cybersecurity. Globally, cybersecurity funding is supposed to increase by 13% year-over-year in 2023.
Where do Startups stand in the general upward trajectory of cybersecurity funding?
It is hard for CISOs to secure adequate funding for cybersecurity, especially in a startup that is already grappling with less-than-ideal funding from venture capitalists. This post will discuss strategies to secure cybersecurity funding for a startup.
5 Crucial Practices to Secure Budget for Cybersecurity in Your Organization
36% of small business owners are not concerned about cybersecurity at all, while 51% of small businesses do not have even the basic security measures in place.
Part of the reason for this is the lack of clear communication between IT and business management teams. An information officer has to present cybersecurity as what it is: an integral part of business processes.
Connect security with business objectives
In an internet-facing business, every action and its outcome has a security aspect. Be it the user-response fields on a website or landing page that takes email IDs from people to share downloadable content, a payment gateway where users provide their banking details, or email communication between internal staff that contains customer information in plaintext, every operation can introduce vulnerabilities unless they are secure.
The security risks associated with business processes must be clarified and documented in a manner that is easy to grasp for the leadership. More importantly, security threats must be connected with the most relevant business objectives at a certain time.
For instance, if a business is pushing for better ranking on the Google search engine results page through rigorous search engine optimization, the IT department can highlight the risk of SEO spamming hacks and how it can jeopardize all the efforts and investments poured into building a strong search presence.
Quantify risk
Ascertaining risk is not enough. It is hard for CFOs to relate to a threat unless it has a number attached to it. Therefore, the IT department needs to evaluate cybersecurity risks in terms of potential losses to justify the requisition for funds.
Business leaders need a clear and concise comparison between the funds necessary to stabilize an organization’s security posture and the monetary losses the organization can potentially suffer by not implementing necessary security measures.
For instance, a password management suite Uniqkey, with features like shadow IT monitoring, automated employee authentication, and military-grade encryption, costs $4.95 per month per user. This tool helps you streamline access management, prevent social engineering, and minimize human error.
On the other side of the equation, 81% of data breaches are caused by access management failures. The average data breach cost for small businesses ranges from $120,000 to $1.24 million. 60% of the small businesses that suffer a breach run out of business within six months.
Key factors to consider while evaluating risk
- Penalties levied by regulatory bodies like the GDPR, and the ICO
- The cost of business downtime
- The cost of investigating and remediating a security failure
- Increased premiums for security insurance post-incident
- Loss of business due to compromised reputation
Prioritize high-risk areas
Funding security for high-risk, mission-critical business functions is more accessible than for low-risk areas with less commercial importance. It is responsibility of a CISO to identify the assets and resources that attract maximum threat.
You can use an attack surface monitoring software on a trial basis or even just a password manager that offers risk metrics to identify the risk-prone areas. Then, you can prioritize the risky functions – applications, cloud storage, productivity tools – based on their contributions to business outcomes and use risk metrics for those to convince leaders.
Security benchmarking
Security benchmarking is the process of measuring the baseline security performance of an organization and monitoring its progress over time compared to industry peers.
This requires continuous monitoring of tangible indicators of an organisation’s security performance. Thanks to the presence of inexpensive security rating software in the market, it is not so hard to do.
Benchmarking clarifies an organization’s position in the industry in terms of security. Startup owners know that internal security measures are often advertised to attract customers. Benchmarking tells them if their business is trailing far behind industry standards. Hence, it is one of the most effective strategies to secure funding.
Establish cybersecurity as a cross-departmental function
The cybersecurity budget in small businesses is usually a tenth of the total IT budget. While cybersecurity is indeed a part of IT, it affects every business touch-point. It is crucial to take security out of the IT closet and establish it as a business function that involves all employees, vendors, contractors, clients, and users.
When business leaders look at cybersecurity as a tool that facilitates the smooth operation of the business as a whole and not a sub-category of IT that concerns the protection of hardware and software, it becomes easier for them to assign adequate value to it.
If you are just starting up your cybersecurity efforts, here’s A Step-by-Step Guide for Setting Up Cybersecurity for Startups
Making the best use of your cybersecurity budget
Perform a risk assessment:
Conducting a risk assessment makes it easier to allocate resources effectively by prioritizing high-risk areas.
Security awareness training:
Phishing and social engineering attacks comprise a large gamut of all cyber threats. Startups can reduce the risk of employees falling victim to these attacks by investing in a security awareness training program.
Patch Management:
Most startups fall prey to mass attacks targeted at businesses running applications with known vulnerabilities. In most cases, the patches for these vulnerabilities are already available through free software updates. Running a patch management process ensures all software is up-to-date.
Use Open Source and Free Tools where applicable:
Some open-source tools can help you with free vulnerability scanning, network monitoring, and intrusion detection. It’s a good idea to use these tools to free up the budget a bit.
Employee Access Control:
This is one area that demands attention, especially with more than 70% of cyber attacks exploiting the human element – that is access related security failures. Invest in a managed tool that can encrypt and secure all credentials, provide role-based access to employees, and automate the authentication process to some extent.
Two-Factor Authentication (2FA):
Enable 2FA and MFA for critical systems and remote access. If you can find a zero-knowledge access management tool that can automate 2FA authentication for a small price, go for it.
Network Segmentation:
Control the lateral movement of security threats by moving critical network assets into a different zone. It allows for dynamic security controls based on the sensitivity of a network zone.
Incident Response Plan:
Invest in an incident response plan. Involve security experts, legal advisors, and internal IT staff in the process. This will help you minimize the damages in the event of a security breach.
Learn how to create a data breach response plan to protect your business and customers.
Cloud Security:
The shared responsibility model of cloud security dictates that cloud users encrypt data that moves in and out of the cloud and configure their cloud infrastructure properly. It’s an excellent idea to Invest in a cloud configuration review.
Security Monitoring and Logs:
Use centralized logging, security information, and event management systems to monitor, detect, and respond to anomalous activities. You can find open-source tools for this.
Regular Backups:
Invest in a data backup mechanism to help you avoid paying ransoms and compromising business operability in case of a breach.
Learn how to choose cybersecurity tools that fit your startup’s size, budget, and needs.
Wrapping up
Deloitte Global surveyed 1000 cyber leaders across 20 countries to determine where cyber security stood in the scheme of commercial success. 86% of the respondents said, their focus on cybersecurity made significant positive contributions to business.
82% of senior business managers in the UK rated cybersecurity as “very high” or “fairly high” in 2022, marking a 5-point increment from 77% in 2021 (source: Office of National Statistics).
At the same time, the number of victims of data breaches increased by 128 million from 2021 to reach 422 million in 2022.
The data indicate that effectively utilising a security budget is more crucial than securing it. It’s essential to focus on connecting the funding request with actual business outcomes and then adhere to that same track while using it.


