Attackers do not need to break your password if they can simply log in. Two trends make this painfully effective. First, leaked credentials are available in vast volumes from stealer logs and historic breaches. Second, people reuse the same or slightly altered passwords across multiple services.
SpyCloud’s 2025 report found that seventy percent of users exposed in breaches reused previously exposed passwords across other accounts, and that 3.1 billion exposed passwords were recaptured in 2024. That scale makes automated credential stuffing trivial and cheap.

Stolen logins dominate real incidents
Verizon’s 2025 Data Breach Investigations Report shows that attacks against basic web applications overwhelmingly rely on stolen credentials. The figure cited is about 88% within that attack pattern. In practice, this means the adversary appears as a normal user, complicating detection and response.
Single-factor access is still common
The UK’s National Cyber Security Center has repeatedly warned that credential stuffing succeeds because of password reuse and single-factor authentication. When multiple factors are missing or inconsistently applied, a reused password can compromise core systems.
Recent breaches that illustrate the risk
Snowflake customer data theft campaign in 2024
Multiple Snowflake customer tenants were accessed after criminals used credentials harvested by infostealer malware and other breach dumps, particularly in cases where only a password was required.
Victims named in public reporting include Ticketmaster and Santander. Investigators pointed to a targeted campaign against accounts using single-factor authentication and old infostealer data. This is a textbook example of leaked, reused passwords enabling large-scale data theft.
23andMe credential stuffing in 2023
Attackers tried username and password pairs from other breached sites until some worked on 23andMe. Initial access to around fourteen thousand accounts led to the exposure of data from millions of profiles because many users had enabled data sharing and reused passwords.
The case is widely cited as a modern credential stuffing attack fuelled by password reuse.
Change Healthcare ransomware in 2024
UnitedHealth’s tech unit Change Healthcare suffered one of the most disruptive healthcare attacks on record.
The company’s CEO told the US Senate the attackers used compromised credentials to reach a remote access portal where multi-factor authentication was not enabled.
The incident affected claims and payments across the system, ultimately impacting data on a massive scale.
What these incidents have in common
- Credentials were already in criminals’ hands through stealer malware logs or prior breaches. Attackers did not need an exploit at the start.
- Password reuse or single-factor access turned small leaks into big compromises. Once in, adversaries moved laterally or exfiltrated data at tenant scale.
- Detection was delayed because the activity looked legitimate. Stolen logins originate from real locations, devices, and browsers, which is why the DBIR consistently highlights credentials as the dominant tactic for web application attacks.

Practical implications for European organisations
- Assume your users’ non-work accounts are breached somewhere. That is why password screening against known leaked sets and enforced uniqueness matters. The NCSC explicitly frames credential stuffing as a consequence of reuse across services.
- Reduce single-factor exposure wherever it still exists. The Change Healthcare case shows the business risk when a critical remote access path lacks multi-factor authentication.
- Continuously monitor for leaked credentials. The Snowflake campaign demonstrates that old stealer logs still enable fresh intrusions. This is a moving target that requires continuous visibility.
- Treat credentials as a board-level risk. Verizon’s 2025 data and the scale of recent incidents underline that this is not a niche technical problem.
How leaked credentials impact your compliance
If you operate essential services, leaked passwords and unknown SaaS are not just a security gap. They are a compliance issue.
NIS2 requires proportionate risk management with strong logical access controls and the use of multi-factor authentication where appropriate. You also need a reliable view of systems in use so access can be governed.
How ISO 27001 maps this
Annex A assigns clear responsibilities for identity and access.
The relevant controls are:
A.5.16 Identity management.
A.5.17 Authentication information
A.5.15 Access control
A.5.18 Access rights.
These expect managed identities, protected authentication data, and regular right reviews.

What to evidence simply
- A current inventory of SaaS and accounts, including tools outside SSO, linked to owners and purpose.
This supports NIS2 Article 21 and ISO 27001 A.5.16.
- Continuous screening for leaked credentials with timestamped alerts and remediation records.
This supports the NIS2 risk management duty and ISO 27001 A.5.17. - Multi-factor on every externally reachable system, with documented exceptions and plans to remove single-factor access.
This aligns with NIS2 Article 21 and ENISA guidance.
The risks above explain why visibility and leak monitoring are now table stakes for operators within critical infrastructure.
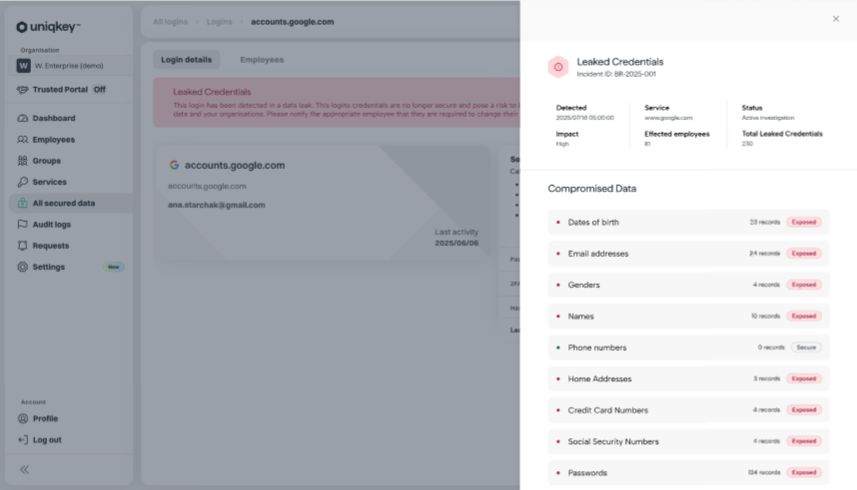
Put this into practice with Uniqkey
In Q4, we are adding Leaked Credential to Uniqkey. The service automatically monitors trusted breach corpuses and stealer log datasets and then flags exposures directly in your Uniqkey dashboard the moment they are detected.
Security teams see exactly which users and which services are affected and can trigger immediate remediation, such as forced rotation and fresh multi-factor checks.
This is designed to close the gap created by password reuse and single-factor access, and it aligns with European expectations on sovereignty and data protection.