Password reuse is a major security risk for businesses. When employees use the same password across multiple accounts, it creates an easy entry point for attackers to access sensitive systems. A strong password policy can help prevent this by enforcing unique, secure credentials for every account.
Here’s what you need to know:
- Longer passwords are better than overly complex ones. Aim for at least 15 characters.
- Block weak and compromised passwords. Use tools to screen against breach databases.
- Require unique passwords for every account. Avoid predictable patterns or slight variations.
- Use password managers and single sign-on (SSO). These tools simplify secure password practices.
- Train employees on password security. Show them why and how to follow the rules.
- Regularly monitor compliance and update policies. Cyber threats evolve, so your policy should too.
Table of contents
Key Elements of an Anti-Reuse Password Policy
Creating a strong password policy is essential to reduce the risks associated with password reuse. A well-designed policy incorporates clear, enforceable measures that strike a balance between robust security and ease of use. The goal is to ensure employees can follow the guidelines without compromising protection.
Password Length and Strength Requirements
When it comes to defending against attackers, longer passwords are far more effective than overly complex ones. Modern cybersecurity standards now prioritize length over requiring specific combinations of characters.
The UK’s NCSC Cyber Essentials requires a minimum password length of 12 characters, while Germany’s BSI recommends at least 20 characters for maximum security. Similarly, France’s ANSSI advocates for passwords achieving 80 bits of entropy, typically requiring 12-16 characters.
Long passwords significantly increase the number of possible combinations, making them harder to crack. For example, a 15-character password made up of simple, memorable words can be much stronger than an 8-character password filled with random symbols.
Outdated rules about character composition, such as requiring uppercase letters or special symbols, are no longer recommended. The UK NCSC explicitly states that “enforcing password complexity requirements is not recommended” and actively promotes their “three random words” approach, like “apple3nemo#biro”.
Overly strict complexity rules can lead to predictable patterns, like turning “password” into “P@ssw0rd1”, which attackers can easily guess. Instead, policies should allow users to create passwords using any printable ASCII and Unicode characters, enabling secure yet memorable choices.
Blocking Weak and Compromised Passwords
Even with strong length requirements, employees may still choose passwords that are weak, commonly used, or previously compromised. A good policy includes proactive measures to block these risky choices.
Systems should automatically screen passwords against databases of breached credentials. If a password matches a known compromised entry, the user should be prompted to select a new one.
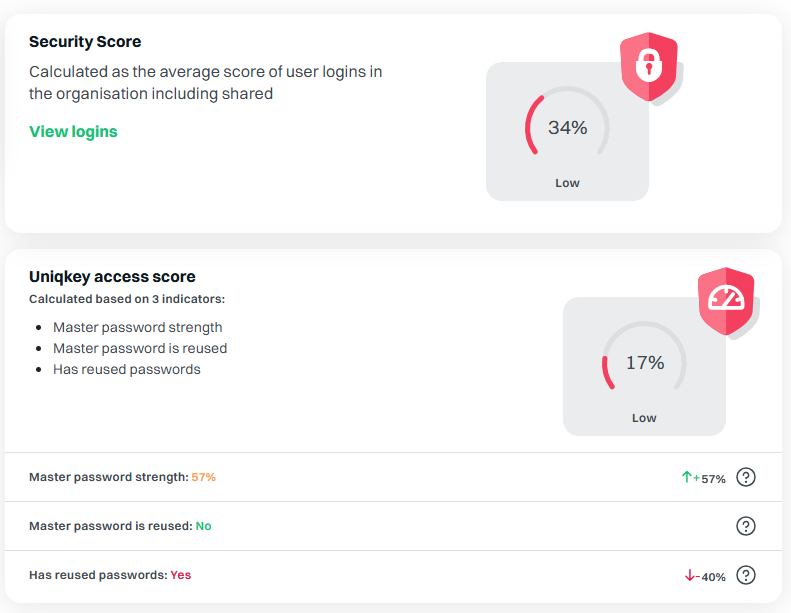
Additionally, policies should block common passwords like “password123” or simple patterns such as “qwerty.” Document the criteria for strong passwords clearly in your policy to ensure consistency.
Requiring Different Passwords for Each Account
To prevent password reuse, ensure that every system requiring credentials – such as email, cloud apps, administrative tools, VPNs, and third-party platforms – has unique passwords.
Avoid variations of the same password across accounts. For instance, changing “MyPassword1” to “MyPassword2” offers little extra security since attackers can easily guess these patterns.
Technical solutions can help enforce uniqueness. Password managers are particularly useful, as they generate and store unique passwords for each account, reducing the burden on users. Similarly, single sign-on (SSO) systems can limit the number of passwords users need to remember while maintaining proper separation between critical systems.
Consider implementing password history checks to prevent users from reusing their last 12–24 passwords. For legacy systems that require exceptions, document these cases carefully, obtain security team approval, and plan for eventual updates.
These steps form the groundwork for the technical and training strategies covered in the next sections. By addressing these key elements, your organization can significantly reduce the risks associated with password reuse.
6 Steps to Create and Deploy Your Password Policy
Creating a strong password policy requires a clear plan that addresses both technical safeguards and human behavior. These six steps can help you design and implement a policy that reduces password reuse and strengthens your organization’s security.
Step 1: Review Current Password Habits
Start by analyzing how passwords are currently managed in your organization. Conduct an assessment to identify where password reuse happens and pinpoint security vulnerabilities. Use anonymous surveys to gather employee feedback on their password habits.
Examine all systems requiring passwords – email accounts, cloud platforms, VPNs, administrative tools, and third-party services. Check the existing password rules for complexity and security. Review security logs for signs of trouble, such as repeated failed login attempts or logins from unusual locations. Also, evaluate your IT policies to ensure they don’t unintentionally encourage weak practices, like forcing overly frequent password changes or setting unrealistic complexity requirements.
This step sets the stage for creating specific and actionable guidelines.
Step 2: Write Your Password Policy
Draft a clear policy that requires unique passwords for every system and prohibits reuse. Outline password requirements, such as length and complexity, and specify which accounts are covered – work emails, cloud services, VPNs, and any critical systems. Clarify whether personal accounts on company devices fall under the policy.
Include consequences for non-compliance, such as additional training, temporary account restrictions, or escalated actions for repeated violations. Provide guidance on secure password storage, recommending approved password managers instead of insecure methods like sticky notes or unprotected files.
Step 3: Add Technical Controls
Bolster your policy with technical measures. Use password history controls to stop users from reusing a set number of previous passwords. Leverage tools like Uniqkey or external APIs to check new passwords against known breach databases, ensuring they haven’t been compromised.
Block weak passwords by maintaining an updated list of commonly used options (e.g., “password123” or variations of your company name). Configure systems to enforce minimum length and complexity rules automatically. Additionally, implement account lockout policies after multiple failed login attempts to prevent brute-force attacks.
These controls work hand-in-hand with employee tools to enhance security.
Step 4: Provide Password Management Tools
Equip your team with password managers to generate and store unique credentials securely. Select a business-grade solution that integrates seamlessly with your systems and can create strong passwords automatically. Deploy it across the organization to ensure consistency in training and support.
Password managers have been shown to significantly reduce reuse when fully implemented. Make sure the tool aligns with your policy and provide clear instructions for migrating existing credentials. For shared accounts, create team vaults to streamline access.
Step 5: Train Your Employees
Even the best tools and policies can fall short without proper employee training. Host hands-on sessions to teach employees how to use the password manager, create unique passwords, and securely store their credentials. Use real-world examples to show how weak passwords can lead to breaches, operational downtime, or financial losses, emphasizing the importance of strong practices.
Address concerns like complexity or getting locked out by explaining backup procedures and offering quick reference guides. Plan follow-up training sessions shortly after rollout and periodically afterward to reinforce key concepts and address any challenges.
Training ensures that technical measures are backed by informed and engaged employees.
Step 6: Track and Enforce Policy Compliance
Monitor compliance with automated tools to detect password reuse. Regularly audit systems to identify weak or repeated passwords. Initially, audits might be conducted quarterly, with the frequency adjusted as compliance improves.
Track metrics such as password manager adoption rates, the variety of passwords used, and the number of password-related security incidents. The table below highlights the differences between manual and automated enforcement:
| Enforcement Approach | Manual Process | Automated Process |
|---|---|---|
| Detection Speed | Days to weeks | Real-time to hours |
| Coverage | Limited sample audits | All accounts monitored |
| Resource Requirements | High staff time | Lower ongoing maintenance |
| Consistency | Varies by reviewer | Uniform rule application |
| Cost | High labor costs | Higher setup, lower ongoing costs |
| Accuracy | Prone to human error | Consistent and reliable |
Establish an escalation process for violations: automated warnings for minor issues, managerial alerts for repeat offenses, and HR involvement for serious breaches. Document compliance activities to refine your strategy over time and demonstrate due diligence. To encourage adherence, consider recognizing teams or departments that consistently follow strong password practices, fostering a culture of security across the organization.
Technology Solutions and Best Practices
Modern technology tools can simplify secure password practices while strengthening overall security. When combined with strong policies and training, these solutions reduce the hassle of managing passwords and help eliminate common vulnerabilities.
How Password Managers Prevent Reuse
Password managers eliminate the need to remember multiple complex passwords. They generate and securely store unique credentials, all protected by a single master password.
These tools automatically fill login forms and can create passwords tailored to specific requirements for different systems. By removing the temptation to reuse simple passwords across accounts, password managers significantly improve security.
For businesses, enterprise-grade password managers offer additional features to enforce security policies. They can:
- Require minimum password lengths
- Block the use of previously compromised passwords
- Provide administrative oversight of employee password practices
Many also include secure sharing options for team accounts and integrate with existing business systems. When deployed across an organization and paired with proper training, password managers make it easier for employees to follow security policies, turning them into a helpful tool rather than a roadblock.
The Role of Single Sign-On (SSO) and Two-Factor Authentication (2FA)
Single Sign-On (SSO) reduces password fatigue by allowing employees to access multiple applications with a single set of credentials. Instead of juggling separate passwords for tools like email, cloud storage, and project management systems, users authenticate once and gain access to all authorized applications.
SSO is particularly effective for cloud-based tools, where weak or repeated passwords are common. By centralizing authentication, SSO reduces the number of passwords employees need while maintaining strong security.
Two-Factor Authentication (2FA) adds another critical layer of protection. Even if a password is compromised, MFA requires additional verification – like a code from a phone app, a text message, or a hardware token – making it much harder for attackers to gain access.
The best approach combines SSO, Password manager and 2FA at the identity provider level. Employees authenticate once using 2FA, then seamlessly access all their applications. For systems that don’t support SSO, password managers step in, providing unique, secure credentials with MFA protection. Together, these tools create a strong, layered defense against password reuse and breaches.
Using Breach Databases to Check Passwords
Regularly checking passwords against breach databases helps identify compromised credentials quickly. Services like HaveIBeenPwned maintain vast databases of passwords exposed in breaches, allowing organizations to verify whether their employees’ passwords have been compromised.
Automated password screening can be integrated into security systems. When employees create or update passwords, the system checks them against breach databases in real time. If a password is flagged as compromised, it’s rejected, and the user is prompted to choose a new one.

These checks use hashed comparisons to maintain privacy while ensuring unsafe passwords are blocked. Many password managers and identity management platforms now include breach database checks as a built-in feature, making it easier to monitor for vulnerabilities without additional tools or manual effort. Regular scans can also catch existing passwords that are compromised in new breaches, enabling proactive updates.
Keeping Your Password Policy Current and Effective
As cybersecurity threats grow and regulations shift, keeping your password policy up to date is a must. Regular updates ensure your policy remains a strong line of defense, working hand in hand with technical safeguards and employee training.
Regular Policy Reviews and Updates
Frequent reviews help measure how well your password rules hold up against emerging threats, new technologies, and regulatory changes. Analyze recent security breaches, advancements in technology, and updates to compliance requirements. Make sure to document any adjustments and clearly communicate these changes to your team, so everyone stays informed and aligned.
Conclusion: Creating Strong Password Security
Establishing a password policy that effectively prevents reuse is critical for safeguarding your business. Password reuse remains one of the most common yet avoidable security risks organizations face today. The strategies discussed earlier – both technical and behavioral – are key to addressing this challenge.
Main Points for Business Leaders
To combat password reuse, you need a combination of technical controls, employee training, and ongoing policy evaluations. Start by setting clear, enforceable standards for password creation across all accounts. Tools like password managers, two-factor authentication (2FA), and breach monitoring systems are essential for ensuring compliance.
Training employees is just as important as implementing technical measures. It’s not enough for them to know the rules – they need to understand why those rules exist and how to follow them effectively. This knowledge significantly reduces the risk of breaches caused by human error.
A layered security approach offers the best protection. Relying solely on single sign-on (SSO) or a single tool leaves your system vulnerable. Combine SSO with password managers, enforce 2FA, and regularly check passwords against breach databases. These overlapping defenses ensure that even if one layer is compromised, others remain intact.
Policies must also evolve to keep up with new threats. What worked last year might not be enough to counter today’s cybercriminal tactics. Schedule quarterly reviews to assess your policy’s performance and make updates as needed, especially to address new compliance requirements like the NIS2 Directive.
How Leadership Drives Policy Success
Leadership plays a pivotal role in the success of any password security strategy. When executives prioritize cybersecurity and allocate the necessary resources, it sets the tone for the entire organization. This includes budgeting for tools, dedicating time for training, and enforcing policies consistently across all levels.
Leading by example is equally important. Use the same password managers and 2FA protocols you expect employees to adopt. When leadership follows the rules, it builds trust and encourages company-wide compliance.
Clear communication is another critical factor. Don’t just issue mandates – explain the why behind password policies. Help employees understand how password reuse can lead to data breaches, financial losses, and reputational damage. Framing security measures as protective rather than restrictive fosters a sense of shared responsibility.
Finally, track your progress. Monitor metrics like password manager adoption rates, training completion, and instances of policy violations. These insights help pinpoint areas needing improvement and demonstrate the effectiveness of your security investments to stakeholders.
Password security isn’t a one-and-done task – it’s an ongoing effort. As cyber threats evolve and your business grows, your policies must adapt. The time and resources you invest today in building robust password security will protect your organization’s most valuable assets in the long run.
Frequently Asked Questions
To help employees maintain unique passwords for all their accounts, businesses should establish a clear and effective password policy. This policy should require passwords to be at least 12 characters long, combining uppercase and lowercase letters, numbers, and special characters to enhance security.
An enterprise password manager can make this easier by securely generating and storing unique passwords for employees. These tools not only save time but also reduce the risk of weak or reused passwords. Alongside this, businesses should encourage regular password updates and provide ongoing training to highlight the importance of good password practices.
For extra protection, using two-factor authentication (2FA) is a must. 2FA adds an additional security step, ensuring that even if a password is compromised, unauthorized access is still blocked. This combination of strong passwords and 2FA significantly strengthens overall security.
Password managers play a key role in combating password reuse by securely storing strong, unique passwords for each of your accounts. With these tools, you don’t have to memorize dozens of passwords, which significantly lowers the chances of using the same password across multiple platforms – a practice that can leave accounts exposed to cyberattacks.
Single sign-on (SSO) systems take things a step further by letting users access multiple applications with just one set of credentials. This not only simplifies life for users but also reduces the temptation to reuse passwords. For businesses, it streamlines access control and makes managing user accounts more efficient.
By combining password managers and SSO systems, organizations can boost security, simplify access management, and enforce better password practices, all of which are crucial for safeguarding sensitive business data.
Keeping password policies up to date is a smart move for any business, especially after a risk assessment or when new cybersecurity threats arise.
To better protect your business, focus on adopting strong password practices. This includes discouraging password reuse, requiring multi-factor authentication (2FA), and training employees on security best practices. Regularly reviewing your policy ensures it stays effective and aligned with current industry recommendations.