Social engineering manipulates and influences people’s behaviour and decisions by exploiting human tendencies and biases.
What is a Social Engineering Attack?
In the context of cyber security, social engineering attacks involve psychological manipulation to compromise digital assets like credentials, personally identifiable information, and financial information. It is also used to deliver a malware payload or to hack into a user account with privileged access.
90% of cyber-attacks have a social engineering element as humans are the weakest link in an organization’s security posture. The human element was partially responsible for 82% of all data breaches in 2022 and at least 70% of these attacks started with social engineering.
Spreading awareness about various forms of social engineering, their impact, and ways to prevent them is paramount. It is the essence of building a culture of security in an organization. This post will highlight different forms of social engineering and how employees from every business section can act against and prevent these malicious attempts.
Types of Social Engineering Attacks
Social engineering can take many forms in different circumstances and contexts. It might seem a little daunting to understand and remember all its manifestations. Nevertheless, most of these attacks have one thing in common: they try to exploit human emotions and tendencies. These attacks are rooted in how we humans feel in different situations, and controlling that one common factor makes it possible to prevent them.
Phishing
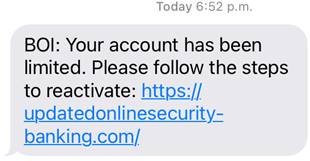
Phishing is the most common form of social engineering. The term is a play on the word fishing, hinting at how attackers send fraudulent communication impersonating a reliable entity to make unsuspecting internet users divulge confidential information. Most of these attacks are conducted through email.

Different phishing techniques
Spear phishing: It refers to targeted phishing attacks on specific individuals or organizations instead of generic phishing emails. Hackers gather information about individuals – their names, job roles, and names of colleagues- and craft the fraudulent message in a way that would seem to have arrived from a trusted source, someone the victim knows, maybe someone from the company.
Whaling: Whaling is a form of spear phishing that targets high-profile individuals like CEOs and CTOs to coerce them into sharing sensitive information or performing a task that may compromise the organization.
Clone phishing: In this method, the attackers replicate a legitimate email or website and send it to the targets. These cloned emails or websites are hard to distinguish from legitimate communications and thus, they often fool users into typing in sensitive information or downloading malware.
Vishing: It stands for voice phishing. Scammers call potential victims and impersonate legitimate entities like a bank. They try to make the victims share information or perform certain actions.
Smishing: Attackers use SMS, text messages or other types of messaging channels to send fraudulent communication.
Pretexting
Pretexting is a form of social engineering attack that involves fabricating a scenario and manipulating targets into performing certain actions.
The usual steps in pretexting are:
- Setting up the scenario: The attacker may impersonate a technician, a colleague, or a customer support executive.
- Credibility building: The attacker provides the targeted individual with specific details about their computer system or shares a technical issue that needs to be fixed. This part always has some accurate information to gain the target’s trust.
- Requesting information: At this point, the impersonator requests certain details that they supposedly need to perform a remote update. The requested data is usually a mix of harmless and compromising information. They might ask for the date of birth of the target, their social security number, and login credentials to a specific site.
- Feigning urgency: The scammer will try to manipulate the target by creating a sense of urgency – as if they’ll incur a great loss unless they make a quick decision.
The hacker wins if the target succumbs to the pressure and shares information, clicks on a malicious link, or tries to log into an account using a link provided during the fraudulent communication.
Baiting
Baiting is the process of offering an enticing reward in exchange for performing a specific task. For instance, a user can be baited with a free software download to download malware. Similarly, physical baits like USB drives and CDs can be used to bait people as well. A malicious actor may leave a USB drive labelled “employee salary information” in the office cafeteria. If an employee is curious enough to plug it into their computer, malware will infect the system.
Tailgating
Tailgating is a common social engineering attack technique that takes advantage of the human tendency to hold doors open for others and not challenge people who seem to belong. An attacker who fits right into place can often gain physical access to restricted areas simply by following someone with access closely.
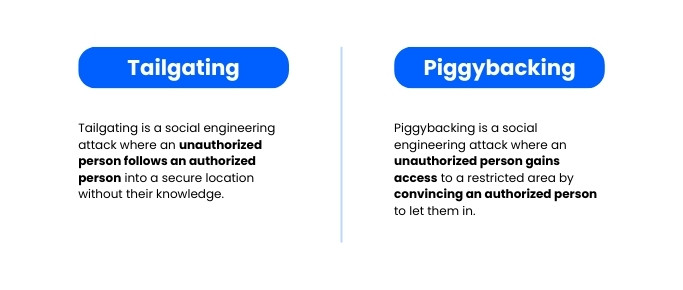
Tailgating is also known as piggybacking. And it can cause serious physical and reputational harm to an organization.
Quid Pro Quo
Quid Pro Quo attacks combine elements of pretexting and baiting to steal sensitive information. In this method, attackers impersonate a technical professional who promises a valuable service in exchange for some information. This type of attack may also involve cloned sites where an unsuspecting internet user may end up disclosing payment information, date of birth, etc.
Water hole attack
A water hole attack is a perfect example of how social engineering and technical exploitation work in tandem to compromise individuals and organizations. Just like predators in a jungle often choose a water source to wait for their prey, in a water hole attack, the attacker identifies a relatively insecure website frequented by the employees of a target organization.
The malicious actor then creates a clone site and directs the traffic to it or infects the legitimate site with malware. Either of the methods can be used to infect the employees with malware. This malware scans the employees’ systems for security vulnerabilities. Once a security gap is found, the hackers can prepare an escalated attack.
Reverse social engineering
This is a simple yet effective attack technique employed by bad actors. First, they target a specific individual and gather all the available information about them. Then, the attacker creates an IT-related problem for the target. After the individual reaches a certain level of frustration, the bad actor impersonates an IT support person and offers help.
The target’s problem gets solved and inspires them to trust the solution provider. Slowly but surely the hacker strengthens the trust. Finally, the target is manipulated into disclosing compromising information or performing a task that is detrimental to the organization’s cybersecurity posture.
AI-Powered social engineering
With Deep Fake and generative AI at their disposal, attackers can now
- Create more convincing fraudulent messages with speed and accuracy.
- Data scraping and making sense of unstructured data is easier than ever. That means hackers can gather publicly available information and find useful bits much faster.
- Technologies like AI voice and deep fake have made impersonation much easier.
- Hackers must never worry about a grammatically inaccurate message or a tonal miscue.
Psychological manipulation in social engineering
Social engineering takes advantage of various psychological patterns – common tendencies, biases, fears, and other emotions – to manipulate the actions of its targets. It is important to recognize various methods of social influencing to implement effective countermeasures.
Persuasion
Persuasion is at the core of social engineering. It is the act of influencing or convincing someone to act in a certain way or to believe something. The process of persuasion in the context of social engineering involves the manipulation of certain human traits such as
- reciprocation
- commitment and consistency
- social proof
- authority
- liking
- scarcity
Attitude and behaviour
An individual’s attitude may differ in various circumstances based on the behaviour they want to project. For instance, a person who takes care not to share her personal information on social media may quite easily agree to share the same to fill up a survey. This contradictory behaviour is often taken advantage of in social engineering attacks.
Trust and deception
Building trust and applying deception are two pillars of SE attacks. The bad actor may build trust by lying, rewarding, persuading, or appealing to other human emotions. Research shows that human beings are prone to being vulnerable in front of people they trust.
Deception counts on the fact that all human beings assume they can detect deception, but most cannot. Deception is performed through carefully enacted plans.
Language
There are similarities between how humans and computers process language. Every input has an impact on the output. Seasoned perpetrators of social engineering manipulate language to trigger different cognitive biases to achieve their goals.
How to prevent social engineering attacks?
Social engineering threats exploit one of the easiest vulnerabilities in an organization – its people. Hence, the preventive act has to start with educating and training the people regardless of departments or capacities within the company.
Build awareness
Every individual in an organization should be trained to identify suspicious communication. Employees across the board need phishing-prevention training so that they are equipped with the strategies for distinguishing legitimate communications and phishing attempts.
The training for employees has to be an ongoing process to keep them ahead of the ever-evolving social engineering threat landscape.
The policy around intra-organizational and inter-organization communication has to be strong and transparent.
Strong authentication and password policies
An organisation’s security should not depend on the ability of human beings to keep their passwords safe and secret. Every professional account should be protected by 2-factor authentication. Ensuring that employees are using strong passwords and not using the same password for different accounts are basic responsibilities.
In an ideal scenario, the employees should not have to handle credentials at all. Passwords should be created, encrypted, and stored in a digital vault and filled in by a password manager. Mandating the use of password managers can help organizations prevent social engineering to a great extent.
Proper access control
Applying the principle of least privilege while granting access to digital assets and resources can save companies from cybersecurity threats. Employees should have access to only what they need when they need it. Credentials should be encrypted with role-based access.
A powerful password management tool like Uniqkey can practically take the danger of password theft through social engineering out of the equation. It encrypts all passwords using military-grade AES-256 encryption using zero-knowledge technology.
With features like automated employee login and auto-fetching of 2FA information, Uniqkey eliminates human involvement in the login process, thus significantly reducing the risk of social engineering attacks.
Secure social media practices
Organizations need clear policies for sharing sensitive information on social media. Social engineering schemes attack people who overshare on social media more frequently.
Also, social media works as a great platform to gather an individual’s personal information like his date of birth as well as the names of his colleagues, company, and his job role.
- Limit the amount of personal information shared on social media
- Apply strict privacy settings and review them frequently
- Avoid sharing daily activities or travel plans
- Avoid clicking on links to download files even if it’s from a seemingly legitimate source
Use of firewall and regular malware cleanups
It’s easy to fall prey to social engineering attacks. Clicking on a link is all it takes to install malware on a system. Frequent clean-ups can ensure that critical systems do not retain malware for too long.
Anti-malware and anti-virus software are essential to secure devices. On top of these, periodic vulnerability assessments can ensure there are no backdoors in an organization’s network.
Machine learning algorithms trained to identify suspicious patterns in email communications used to be a great countermeasure for social engineering, but with the advent of generative AI, such measures are becoming obsolete in many cases.
To conclude
Human awareness is the first line of defense against social engineering attacks. By educating employees about the risks and how to identify and avoid them, organizations can significantly reduce their chances of being successful. However, human awareness is not enough. Organizations also need to implement robust access management controls to prevent attackers from gaining unauthorized access to systems and data.
Uniqkey’s advanced access and password management solutions can help organizations achieve both goals. Uniqkey’s eliminates the need for employees to remember multiple passwords, making it more difficult for attackers to exploit weak passwords. Uniqkey’s two-factor authentication (2FA) solution adds an extra layer of security by requiring users to provide something they know (password) and something they have (token) to authenticate. Uniqkey’s risk-based access control (RBAC) solution allows organizations to dynamically control access to resources based on the user’s role, location, and other factors.
To learn more about how Uniqkey can help you prevent social engineering attacks, please visit our website or schedule a demo today.


