There are many methods of encrypting and decrypting data but only one where even the verifying agent doesn’t know the decryption key, which is zero-knowledge encryption. In this short article, we will look at several symmetric and asymmetric encryption methods and find how encryption based on zero-knowledge proof compares with them.
In this article…
- The two most important characteristics of encryption
- The basics of encryption and some traditional methods of data encryption
- The problem with traditional encryption methods
- End-to-end encryption as a solution
- How does Zero-Knowledge Encryption compare with other methods of encryption?
- The cryptographic implications of zero-knowledge encryption
- Traditional encryption vs zero-knowledge encryption
- Benefits of using zero-knowledge encryption in different industries
- Wrapping up
The two most important characteristics of encryption
- How hard it is to decrypt the data without the decryption key
- How well the decryption key is hidden and secure
With the arrival of Advanced Encryption Standards with a 256-bit encryption key, it has become almost impossible for hackers to decrypt data without the key. It would take even the most advanced modern computers several years to break a 256-bit encryption.
The security challenge is related to the second aspect. The secrecy of the decryption key. Social engineering methods have been quite fruitful in coercing people into disclosing their passwords or private decryption keys. This is where zero-knowledge proof comes into play. If you want to know how exactly zero-knowledge proof works, here’s an in-depth guide to zero-knowledge encryption.
The basics of encryption and some traditional methods of data encryption
There are two primary methods of encryption – symmetric encryption and asymmetric encryption. These two ideas are manifested in many different sub-classes of data encryption. Some are old and falling out of use fast, some still have a lot of validity in modern times. However, all of them share one critical disadvantage – the possession of the decryption key by the server.
Symmetric encryption
Symmetric encryption uses a single secret key for both encryption and decryption of data. That means the sender and the recipient of certain information should have the same key to access the information. It is a fast and efficient method of encryption and hence used in encrypting bulk files or email attachments.
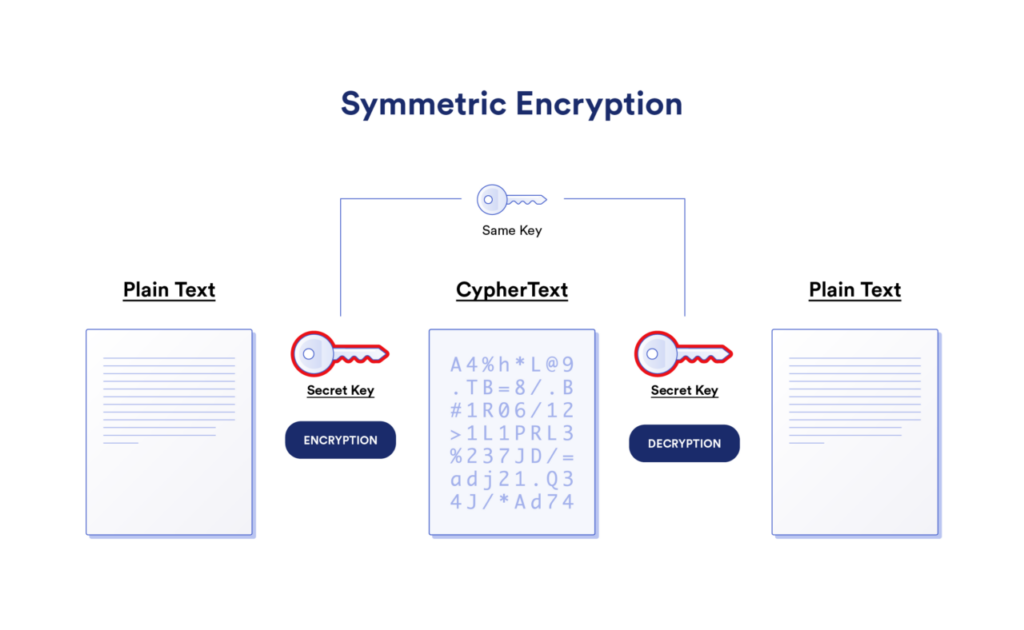
Modern symmetric encryption uses the Advanced Encryption Standard (AES) to encrypt data with a 256-bit key. It is almost impossible to break. It is widely used by businesses and governments to secure files and protect systems.
Data Encryption Standard (DES) is an older symmetric encryption algorithm that is no longer considered to be as secure as AES. However, it is still widely used in legacy systems.
3DES is a variant of DES that uses three DES keys to encrypt data. It is more secure than DES, but it is also slower.
These aside there are other symmetric encryption methods such as Blowfish and Twofish. However, AES is the prevalent encryption in all major industries.
Asymmetric encryption
Asymmetric encryption uses two keys: a public key and a private key. Anyone with the public key can encrypt data, but only the person with the corresponding private key can decrypt it.
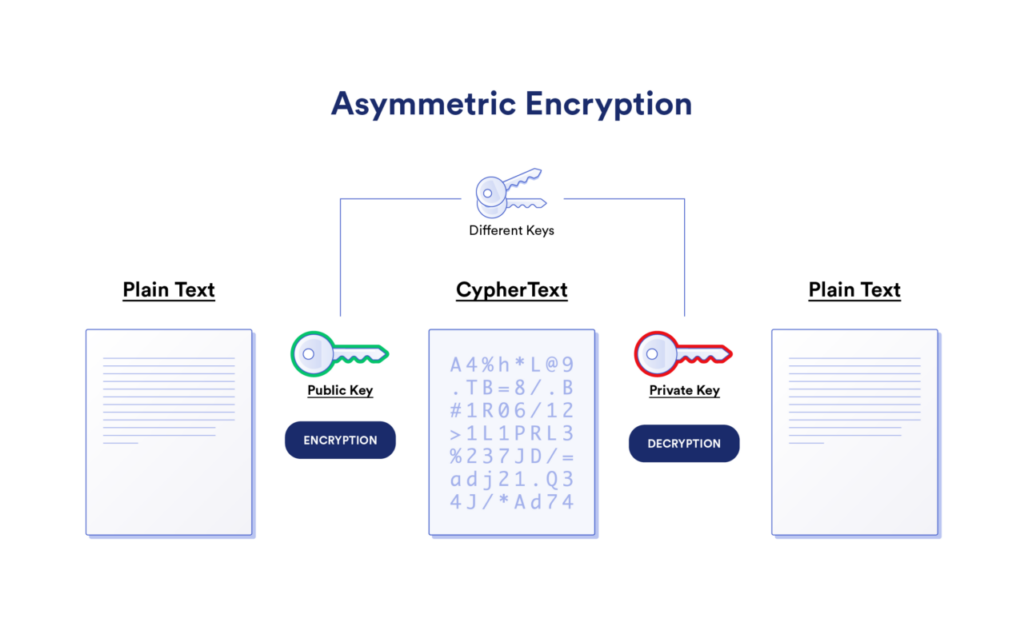
Asymmetric encryption is slower when compared with symmetric encryption but it is more secure.
Some widely used algorithms for asymmetric encryption include
Rivest-Shamir-Adleman (RSA): One of the oldest and most well-known asymmetric encryption algorithms based on the mathematical properties of large prime numbers.
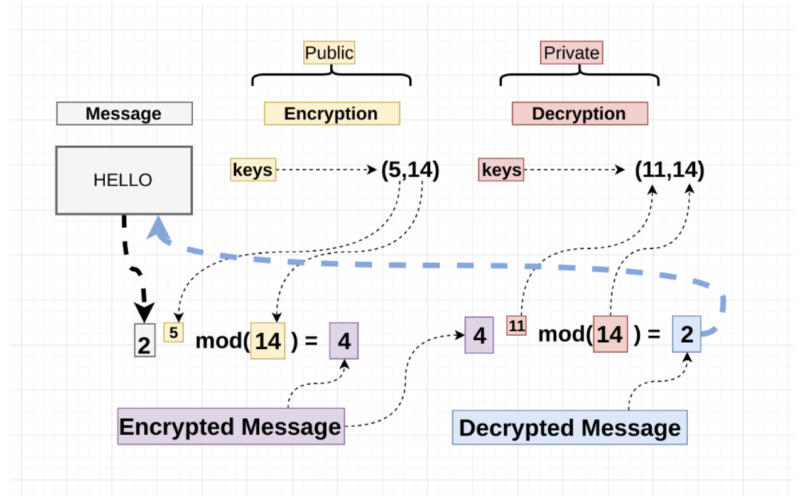
Diffie-Hellman: Another asymmetric encryption algorithm based on the properties of modular arithmetic.
Elliptic-Curve Cryptography (ECC): A newer asymmetric encryption algorithm based on the properties of elliptic curves.
Hashing and salting
Hashing is a one-way cryptographic function that takes an input of arbitrary length and produces a fixed-size output or a hash value.
When you create a password for a specific account, the plain-text password is transformed into a hash with the help of a hashing algorithm and stored. It is an irreversible process.
When you try logging into the account the following time, your input undergoes the same hashing process, creating a hash value. If the hash value of your input matches the hash value of the password you created, access is granted.
The issue with this is that if two people use identical passwords, the corresponding hash values will be identical too. This is where salting comes in.
Salt is an arbitrary string of characters added to the passwords created by each individual before hashing it. The salt is different for each person, therefore it doesn’t matter if two people have the same password, the hash value is always different for them.
💡In this guide, we share insights on how password encryption functions and explain the various terminologies associated with it.
Key encapsulation
Key encapsulation is used for transmitting a symmetric key over a public network. It applies an asymmetric encryption to encrypt the symmetric key thus encapsulating the key. It ensures that while the key is in the public domain, only specific people can access it.
The problem with traditional encryption methods
The older encryption standards like DES and Triple DES have been outsmarted by hackers and while some of the older methods are still in use, AES is currently the most trusted form of encryption. However, with most forms of encryption, there is one fatal weakness. The service provider has access to the decryption key.
An example will help us understand why this is an issue.
Let’s suppose A is a password manager that offers a password vault. Every password within the vault is encrypted and the decryption key is a master password created by user B. Now, when B tries to access his passwords, A must verify B’s identity. So, B enters the password and A looks for a match inside its database.
There are three problems here
- While the master password is stored by the service provider in encrypted form it can still be stolen. Although the password is not immediately accessible due to the encryption, even the hash value has a price on the dark web. Humans have a propensity to reuse passwords or set easy passwords and even hashed passwords often reflect such patterns.
- If a server is hacked and the hackers gain access to the password directory, they can delete the stored passwords, rendering all accounts inaccessible to legitimate users.
- Phishing websites can be used to steal the master password in plaintext. Imagine a phishing site that resembles the site of the password manager you use. You enter the master password to log into your account and it goes straight to the hacker in plaintext.
End-to-end encryption as a solution
End-to-end encryption (E2EE) is a cryptographic method that ensures that only the sender and the intended recipient can read encrypted messages. This means that even the service provider that transmits the messages cannot access the plaintext.
How does E2EE work?
End-to-end encryption uses a combination of symmetric and asymmetric encryption to ensure that the content of communication between two parties is not readable or traceable even by the service providers. The Signal protocol is a popular example of E2EE; it is used by WhatsApp to encrypt messages and calls.
When you start a conversation on WhatsApp, it encrypts the messages with the help of symmetric encryption. The key is encapsulated with asymmetric encryption and shared with the parties but never stored by the WhatsApp server. It’s the devices that work as decryption keys.
Why E2EE is not applicable for securing cloud storage
As the name suggests, end-to-end encryption requires two ends – two communicating parties – to work. So, if you want to secure data in a cloud storage system with encryption, E2EE will not cut it. And this is exactly where Zero knowledge comes in.
How does Zero-Knowledge Encryption compare with other methods of encryption?
Zero-knowledge encryption or ZKE uses the concept of ZKP or zero-knowledge proof to enable a kind of encryption where the service provider isn’t required to store the decryption key. It is an elegant use of statistics and probability to establish the truth of a statement without disclosing the statement – therefore it can be used to establish that an individual owns a decryption key without actually knowing what the key is.
The cryptographic implications of zero-knowledge encryption
- The service provider doesn’t have access to the decryption key
- In the event of a breach, the hacker never gets their hands on the password, not even in hashed form
- Since the prover isn’t required to enter the key to access their accounts or prove their identity, any request to do the same violates the zero-knowledge protocol and therefore gives away a phishing attack to any smart user.
- It can be used to encrypt data in cloud storage
Traditional encryption vs zero-knowledge encryption
| Traditional encryption methods | Zero-knowledge encryption |
| The server stores the password or key in plaintext or hashed forms. | The servers that use zero-knowledge encryption never store the password or key. |
| Absolute proof is used for verifying the identity of a user which means the user-inserted password has to match the stored password for the authentication. | The verifier uses probabilistic proof to determine the authenticity of a user. |
| Users are susceptible to phishing attacks. | Phishing attacks are taken out of the question. |
| Passwords can be stolen or deleted in case of server hacks | Passwords aren’t stored on the servers hence, cannot be stolen or deleted. |
Benefits of using zero-knowledge encryption in different industries
Zero-knowledge encryption uses complex mathematical algorithms for authentication and is very hard to break even with quantum computers. This encryption process is extremely strong, secure, and versatile. Hence, there are many use cases spread across industries even though the commercial adoption of the zero-knowledge protocol is quite novel.
Zero-knowledge in finance
- It can be used to authenticate users without revealing their passwords
- The legitimacy of transactions can be determined without revealing the details of the transaction
- ZKP can be used to prove that a financial institute complies with regulations without accessing customer data.
Zero-knowledge in healthcare
- It can be used to share drug-recovery data with collaborators without disclosing proprietary data
- It can allow researchers to analyze genomic data without compromising privacy
Zero-knowledge in the public sector
- It can enhance the privacy and anonymity factor of the voting process
- It can be used to prove a citizen’s tax compliance without revealing tax-related data
Wrapping up
It is safe to say that Zero-knowledge encryption is a new horizon in the world of cryptography and security in general. In terms of industrial adoption, ZKE is still in a nascent stage while some forward-thinking organizations have been proactive in enlisting its power. For instance, Uniqkey uses zero-knowledge architecture to authenticate the identity of its clients to create a foolproof identity and password management solution. It’s a big and decisive step towards the future of security.


