You are probably reading this page because you are wondering something about Active Directory (AD aka Microsoft Entra ID). What exactly is it, and why does it appear so important within the spheres of network management and user authentication?
Active Directory is a technology by Microsoft, one of the leading tech companies. It was introduced to streamline network management and user authentication as well as to simplify resource allocation in a centralized environment. Think of it as a virtual yellow page where you can put in all your users and computers for security and easier management of the network.
Active Directory is an important component in companies and big networks. It serves as a gatekeeper for a world where cyber security is more significant than anything else. It ensures that the right persons get the right access to information and organizational assets for safeguarding the integrity and protection of organizational data and resources.
This blog will take you through exactly what Active Directory is and how it works behind the scenes to ensure networks run smoothly and remain protected, whether you are an IT specialist needing to refresh your skills or want to know the fundamentals of network management.
Understanding Active Directory
Let’s skip right to defining what Active Directory actually is. Put simply, Active Directory is a telephone directory of a network. It is a service that stores information on objects on a network and makes it easy for administrators as well as users to locate and use it.
Information is organized and accessed through domain control in Active Directory, which serves as a place for network administrators to manage resources extensively.
Now, to make sense of how Active Directory is structured, it’s essential to get acquainted with some key components. Let’s break these down one by one.
Domains: A domain can be considered a kingdom under the active directory. It is a space where all network entities exist, including users, groups, and devices such as computers and printers. The objects are accessible via a unique name known as a domain.
Trees: The branches connecting kingdoms, or, more exactly, domains, are like trees. Domains can be related hierarchically to each other, share a continuous namespace, and cooperate well.
Forests: The forest is akin to the universe that encompasses many trees as kingdoms. A high concept that is shared by one or more trees having identical scheme and configuration which gives the organization boundaries.
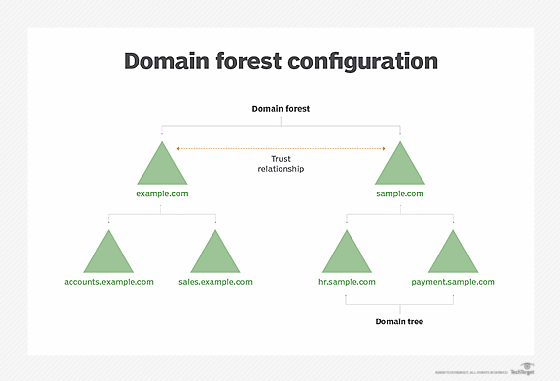
Organizational Units (OUs): OUs can be said to act as departments under a domain. They assist in the logical order and management of resources. It is as if each department has different duties and resources.
Schema: The schema is the blueprint. This refers to an outline of the type of objects and data that are allowed to be stored in Active Directory, thus guiding what data is stored as well as how.
Core Functions and Services of Active Directory
Active Directory serves a lot of functions for networking. Each of those hats is important as it ensures that the network is not only secure but also effective. Let’s explore some of the fundamental functions and services Active Directory provides:
User Authentication: Basically, Active Directory is the core of an entry. It ensures that a person is what they appear to be. Upon successful authentication of the username and password, Active Directory grants the user entry into the organization. This is an important part of ensuring one’s network environment is safe.
User Authorization: What happens after users log in, and what can they do? This is handled by Active Directory which allocates roles and permissions to users. It makes sure that users only gain access to the desired segments of the network and only the levels of authority necessary to accomplish tasks, but not anything extra.
DNS Services: DNS is a directory of internet addresses, and Active Directory smoothly supports this function. The integration makes it possible for domain names to be resolved to network addresses, thus ensuring accessibility of the network resources and allowing proper communication among devices.
Centralized Resource Management: It involves visualizing that there will be a command centre for the management of various network tools. Active Directory offers this, acting as an entry point where the management of users, computers, printers, etc. can be done in an orderly manner instead of a chaotic one.
Directory Services: Essentially, Active Directory is a directory service, an electronic “phonebook” containing information on network objects so that users and administrators can locate and use the information easily. This feature ensures the ease of network traversing and resources utilization.
Active Directory Objects
Objects are the basic units in the Active Directory domain. Without these, they are the basic units that form the network’s structure for its organization and connection. Let’s briefly go through each object type:
Users: Users are human elements with access to the network. Each of them is given personal credentials that they can use to log in, access resources, and complete tasks relevant to their roles and permissions in the company.
Groups: Groups streamline access management. Groups of user that have a similar role are bundled so they can easily manage and provide access to user that is needed.
Computers: In Active Directory, computers are not mere lifeless machines. They are seen as objects that can be centrally controlled to conform to the regulations and corporate safeguards.
Shared Resources (Printers, Folders, etc.): Active Directory oversees shared resources such as printers and folders, allowing individuals only with their permissions. It promotes the efficient use of resources, thus maintaining order and availability.
Trusts: Trusts constitute secure conduits for message exchange and resource sharing between domains or forests and secure the network’s openness through controlled access and collaboration channels.
Working with Active Directory
Practical management is what Active Directory isn’t all about. Different tools facilitate the physical work with Active Directory, and each has something invaluable to contribute. Let’s dive into some of these essential tools:
Microsoft Management Console (MMC): It is a centralized environment by which different Active Directory management snap-ins are integrated into a single platform, allowing the network components and other resources to be managed effectively.
Active Directory Users and Computers (ADUC): ADUC is one of the essential weapons in the Active Directory kit and simplifies the management of user and computer objects. This is one of the most crucial places in Active Directory as objects are created, modified, and deleted here every day.
Active Directory Administrative Center (ADAC): ADAC provides a modern management experience through utilizing a task-based management approach, and an updated interface for managing Active Directory objects and configurations.
This process also entails things like creating new user accounts, setting permissions, grouping objects into OUs, and even removing objects in some instances. These fundamental operations ensure that the directory is updated, secure, and true to the organization’s current structure and access-control requirements.
Active Directory Security
Active Directory is much more than just managing users and resources but is a major pillar of network security. This is crucial in defending the organisation’s digital backbone.
In particular, authentication and authorization of a user can be achieved through Active Directory. It ensures the security of the network by verifying user identities and accessing the required resources by controlling the same.
Security practices in Active Directory are complex. For example, password policies ensure the creation of complex passwords as a protective measure against unauthorized access. Account lockout policies provide an additional security measure that stops an unauthorized person from trying to enter using multiple incorrect login details.
In addition to this, Active Directory also supports the use of Group Policies which provide organizational consistency in terms of security configurations, hence ensuring systems follow organizational security standards and practices.
Conclusion
Active Directory is of importance in protecting the security posture of an organization by providing for authentication of users authorizing them, among other functions that protect its information technology infrastructure.
Uniqkey provides better solutions to organizations looking for enhanced security. Uniqkey is an effective password manager that ensures the security of your data in accordance with strict European data protection regulations and storage standards, with all data centres located in Denmark.
In the case of Uniqkey, the solution goes even further beyond. It allows for a smooth connection with Active Directory using SCIM integration, thus providing for better employee direct sync, password and access management than ever before. It is easier to control user access and protect sensitive data via SCIM integration.
Uniqkey provides more than just secure password management: it is also compatible with Active Directory to ensure the safest and most effective handling of your company data. An improvement in using Active Directory via Uniqkey makes a more secure and economical IT environment.
Determine how Uniqkey interacts with Active Directory to improve the network’s security and optimize it.


