Brute force attacks used to be very time-consuming and resource-intensive, so malicious actors had to be more selective when choosing their targets. With the advancement of technology and the availability of powerful computing resources, though, attackers can now perform brute force attacks more efficiently. What this means is that any organisation can now be vulnerable to this type of hacking method.
More than 80% of hacking breaches, in fact, use brute force or stolen credentials. Yet, even though a password that only uses lowercase letters can be cracked immediately, many people (about 83% of Americans, for instance) still use weak and easy-to-guess passwords — and share the same password or login credentials across many services and accounts!
If a brute force attack is successful, it can lead to unauthorised access to sensitive information, systems, or accounts. In this guide, we will explain in detail how they work and, more importantly, go through the measures you can implement to detect brute-force attacks and prevent them.
In this article…
What is a Brute Force Attack?
A brute force attack is a method used by hackers and other malicious actors to gain unauthorised access to a system or an account. The way they do this is by systematically trying all possible combinations of encryption keys or passwords until they can find the correct one.
Brute force attacks are often used to perpetrate data breaches. Once attackers gain access to systems or accounts, they can exfiltrate sensitive data, such as personal information, financial records, or intellectual property.
How Brute Force Attacks Work
Simply put, brute force attacks rely on the sheer volume of attempts to bypass authentication mechanisms and gain access to protected resources. As we mentioned above, they can be time-consuming and resource-intensive — but can also pose a significant threat if successful.
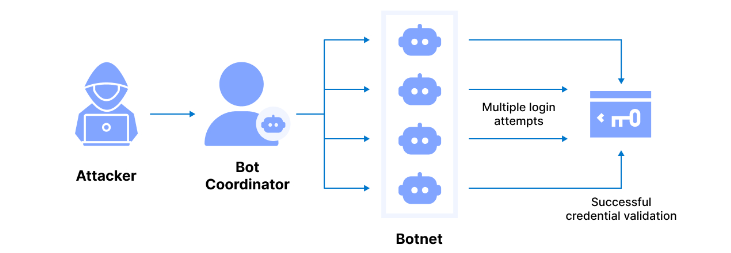
Here’s how a brute force attack works:
- Target identification: The first step is for the attacker to identify the target system or resource they want to gain access to. This could be a user account, a website login page, an encrypted file, or any other protected resource.
- Username enumeration: If the attacker doesn’t already have the username, they may then attempt to enumerate valid usernames through various means, such as scraping public profiles, guessing common usernames, or exploiting vulnerabilities that leak user information.
- Password guessing: With the target username (if available), the attacker starts guessing passwords. Brute force attacks often start with simple passwords (think 123456 or “password”) and then move on to more complex ones. The use of password dictionaries is quite common, too, as they contain popular combinations of words or random strings of characters.
Using Automated Tools for Brute Force Attacks
To speed up the process, attackers often use automated tools or scripts that can systematically try different combinations of usernames and passwords. These tools may have features like password dictionaries, character substitutions, or brute force algorithms optimised for efficiency.
Ultimately, the goal of this type of attack is to continuously make login attempts using different combinations of usernames and passwords until they either gain access or exhaust all possibilities. This process can take a significant amount of time, especially for complex passwords or encryption keys.
If the attacker successfully guesses the correct combination of username and password, they gain unauthorised access to the target system or resource. However, if their attempts fail, they may either give up or try alternative attack vectors, such as phishing or social engineering.
Types of Brute Force Attacks
Brute force attacks come in various forms, each tailored to exploit specific vulnerabilities or target different types of authentication mechanisms. For example, they might focus on weaknesses in password policies, user behaviour, or system configurations.
Let’s see some common types of brute-force attacks.
Simple Brute Force Attack
In a simple brute force attack, the attacker systematically tries all possible combinations of characters, starting from the simplest and progressing to more complex ones. This method is typically used to crack passwords or keys by iterating through all possible combinations of letters, numbers, etc.
Dictionary Attacks
Unlike simple brute force attacks, dictionary attacks use predefined lists of commonly used passwords or words from dictionaries. Instead of trying every possible combination, the attacker tries a set of known passwords, which may include variations, common phrases, or leaked password databases. Dictionary attacks are often more efficient than simple brute force attacks, especially when users choose weak or easily guessable passwords.
Hybrid Attacks
Hybrid attacks combine elements of both brute force and dictionary attacks. They start with a dictionary of common passwords but then modify them using rules or patterns to generate variations. For example, attackers may append numbers or special characters to dictionary words or use common substitutions (e.g., “leet speak”) to create password variants.
Credential Stuffing
Credential stuffing attacks involve using lists of known username and password pairs obtained from previous data breaches or leaks. Attackers automate the testing of these credentials across multiple online services or websites, looking specifically for users who reuse passwords. Credential stuffing attacks are often automated and can result in account takeover or unauthorised access to sensitive information.
Credential Cracking
Credential cracking attacks focus on cracking hashed passwords obtained from compromised databases or stolen password files. Attackers use specialised software or tools to generate hashes for common passwords and compare them against the hashed passwords in the database. If a match is found, the attacker has successfully cracked the password and can use it to gain access to the corresponding account.
Password Spraying
Password spraying attacks involve hackers attempting to access multiple accounts using a small list of common passwords (like “123456” or “password”). They try these common passwords across many accounts, aiming to exploit the widespread weaknesses of password reuse and simple passwords. By trying only a few passwords per account, they avoid triggering typical account lockout defences.
Reverse Brute Force Attacks
In a reverse brute force attack, the attacker starts with a single password or a small set of passwords and systematically tries them against a large number of usernames. This approach is effective when targeting systems with weak password policies or default credentials, allowing attackers to gain access by trying a limited number of commonly used passwords against multiple accounts.
How to Prevent Brute Force Attacks
Data breaches can have severe consequences, including financial losses, reputational damage, and legal liabilities. So, to defend against these types of attacks and mitigate their potential impact, it’s crucial to implement robust security measures.
Here are some effective strategies to prevent brute force attacks:
- Use strong passwords: The first line of defence against brute force attacks is to encourage users to create strong, complex passwords that are difficult to guess. Passwords should include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using common words, phrases, or predictable patterns. Did you know, for example, that adding uppercase, numbers, and special characters can increase the cracking time to 63,000 years?
- Implement account lockout policies: Lockout policies can automatically lock users if they detect a certain number of login attempts that have failed. This prevents attackers from repeatedly guessing passwords until they find the correct one. However, be cautious with lockout thresholds to avoid the risk of denial-of-service attacks.
- Rate limit login attempts: Use rate limiting to constrain the number of login attempts from a single IP address within a specific time frame. This helps prevent automated brute force attacks by slowing down the rate at which attackers can guess passwords.
- Monitor and analyse login attempts: Continuously monitor and analyse login attempts for unusual patterns or suspicious activity. Implement logging and alerting mechanisms to notify administrators of multiple failed login attempts, especially from unfamiliar locations or IP addresses.
- Educate users: Educate users about the importance of password security and encourage them to use unique passwords for each account. Provide guidance on creating strong passwords and avoiding common pitfalls, such as using easily guessable information or reusing passwords across multiple accounts.
- Update and patch systems: Keep systems and software up to date with the latest security patches and updates. Vulnerabilities in authentication mechanisms or software components can be exploited by attackers to launch brute-force attacks.
- Deploy Web Application Firewalls (WAF): Deploy WAFs to filter and block malicious traffic, including brute force attacks, before they reach web applications or login pages. WAFs can detect and mitigate various types of suspicious activity, helping to protect against unauthorised access.
Uniqkey is a comprehensive cybersecurity solution that offers advanced protection against various threats, including brute-force attacks. We simply eliminate the need for traditional passwords by offering everything your organisation needs to streamline how your employees share and manage passwords, including automatic logins, 2FA autofill, and built-in password generators. Plus, all of this information is encrypted and stored in each users’ device, maximising security.
Uniqkey also employs behavioural analysis and machine learning algorithms to analyse user behaviour patterns and detect anomalies indicative of brute force attacks.
And, unlike other services, Uniqkey leverages real-time threat intelligence feeds and security updates to identify and block known malicious IP addresses, botnets, and other threat actors involved in brute force attacks. Get started with Uniqkey to know how you can effectively mitigate risks and enhance the overall security posture of your organisation.


