It costs $0 for a threat actor to access over 2.3 billion credentials to launch a cyber attack. In total, an attacker needs less than $200 to target 100,000 users with an account takeover attack. This is the state of credential stuffing today, which has emerged as a top enterprise attack.
The point here is that credential stuffing attacks have become so cheap and easy that attacks have soared so greatly over the years. Yet, there is something about the nature of credential stuffing that makes it evade normal threat detection and resist sophisticated prevention methods.
This article is a comprehensive outlook of credential stuffing: what it is, how it works, attack trends, and defense mechanisms. Here, you’ll learn all about credential stuffing and understand how to make it not a problem for your organization.
In this article…
What is a Credential Stuffing Attack?
At the most basic level, credential stuffing is the process of fraudulently attempting to gain access to a service by using hordes of stolen credentials. Usually, an attacker obtains compromised credentials – usernames, email addresses, and passwords – from one online service and injects them into the login pages of other services.
Why does this work?
If an attacker gets a list of 1 million pairs of usernames and passwords from a data breach at Website A, they can deploy bots and write automated scripts to systematically test those stolen credentials on Websites B, C, and D to gain illegitimate access.
Accounts that match the stolen credentials will be compromised even without breaching the other websites. Just one breached website is enough to scale and spread the damage across multiple platforms.
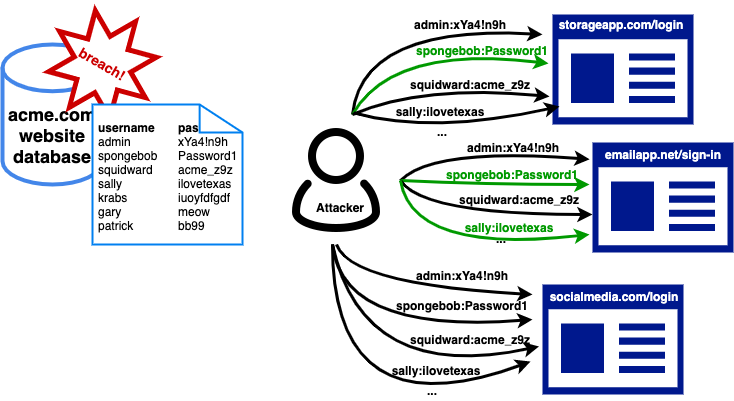
In short, credential stuffing is done in the hopes that some people will have reused the same credentials across multiple services. And people actually do. So, credential stuffing has grown to be a popular form of attack with much higher success rates than traditional brute force attacks and the like.
➡️Relead Post: Password Spraying Explained (And How to Stay Safe)
Nature of Credential Stuffing Attacks
Credential stuffing attacks are difficult for organizations to detect because, in real terms, no breach is involved besides the initial breach of the company from which the credentials were stolen.
For subsequent websites whole login forms are injected with stolen credentials, attacks usually bypass notice because the login attempts involve real usernames and passwords that work. From the backend, it looks exactly like legitimate users are logging in.
Yet, so much damage is being done at the same time. This is why credential stuffing is such a dangerous cyber threat for both businesses and users alike. An efficient enterprise approach to solving the problem will require a centralized solution for access management and monitoring, which Uniqkey provides, enabling you to achieve adequate and full visibility over your systems.
Difference Between Credential Stuffing vs Brute Force Attacks
OWASP and other platforms often define credential stuffing as a kind of brute-force attack. However, going by strict definitions, they are technically not the same. Brute force attacks mean trying to crack login credentials by blindly guessing all possible combinations of passwords.
This means it relies on luck and mostly cycles through common or predictable password options such as “123456” or “password” and combines them with known usernames or email addresses from a target site.
The likelihood of success with brute force attacks depends almost entirely on the complexity and unpredictability of the passwords users have set up. So, a user with excellent password hygiene is virtually immune to such attacks.
Brute force attacks remain a problem, though, because (1) they are cheap to run at a large scale, (2) they require no sophistication on the part of the attackers, and (3) many users, unfortunately, still use guessable password patterns.
With modern security measures, brute force attacks have been largely rendered unlikely. However, using a strong password doesn’t make anyone immune against credential stuffing if they use that password on another service and that service gets breached.
| Feature | Credential Stuffing | Brute Force Attacks |
|---|---|---|
| Definition | Uses lists of previously compromised usernames and passwords from data breaches to try to access other websites. | Attempts to guess login credentials (usernames and passwords) by trying numerous combinations of characters, symbols, and common passwords. |
| Attack Strategy | Leverages the fact that people often reuse credentials across multiple services. | Relies on trying multiple password possibilities against one or a few accounts. |
| Source of Data | Employs leaked or breached username/password combinations. | Does not require prior knowledge of leaked credentials. |
| Success Rate | Often has higher success rates due to password reuse. | Typically has lower success rates unless weak passwords are used. |
| Speed | Can be extremely fast with automated scripts and tools. | Can be slower, especially when targeting accounts with strong passwords and lockout mechanisms. |
How Credential Stuffing Works
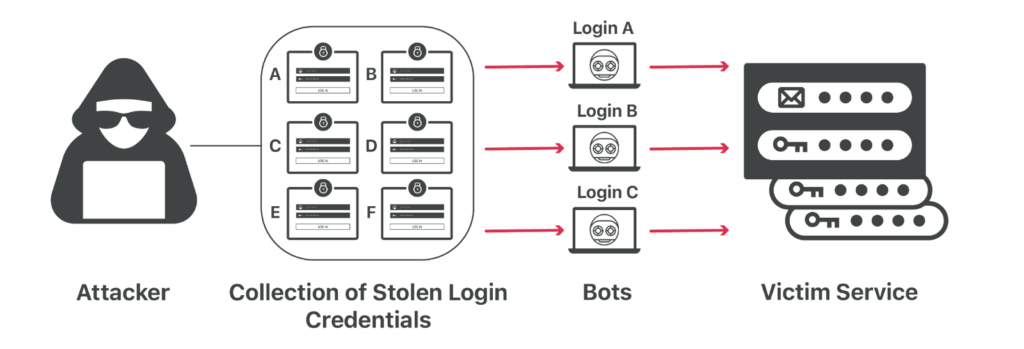
On a basic level, credential stuffing involves a few simple steps. The attacker:
- Obtains stolen credentials either by facilitating a data breach by themself or purchasing them on a dark web marketplace.
- Deploys automated tools, bots, and malicious scripts to test the stolen credentials against many websites, hoping to find matches.
- Gains unauthorized but undetectable access to the user account on that platform.
- Goes ahead to use the account for various malicious purposes, such as stealing information, making transactions, sending spam, or even selling the credentials and other sensitive information to other attackers.
Success Rates of Credential Stuffing
Statistically, credential attacks don’t have a high rate of success: typically 0.1%. This doesn’t look like much, but when one considers the scale at which these attacks are launched, much damage is being done.
For instance, with that success rate, an attacker with 1,000,000 sets of credentials should get a match at least 100,000 times, which is a lot. Imagine gaining access to the bank accounts of a hundred thousand people through such nefarious means.
More so, credential stuffing, if successful, offers cybercriminals several opportunities to act out their fraudulent motives.
For example, accessing someone’s email inbox provides troves of personal data for phishing schemes. E-commerce accounts with stored payment data can be used to steal funds or fraudulently purchase goods. At scale, the potential payout keeps these attacks alive despite their statistical improbability, much to the disadvantage of users caught in the crossfire.
Credential Stuffing and Technological Sophistication
Over the years, several innovations have been deployed to mitigate credential-stuffing attacks. They all revolve around trying to catch when there is an unusually high number of login attempts within a duration of time especially through a single device, particularly by noting suspicious IP addresses.
However, attackers raised their game by using bots to circumvent such protection methods, to make the login attempts indistinguishable from regular login traffic.
The bots can simulate human web browsing behavior, rolling through combinations of stolen usernames and passwords while generating intentionally random delays between tries to avoid rate limits, if any.
A more sophisticated approach is to create a distributed network of machines across different locations to power the attack. By doing so, login attempts from each machine are very few and hardly raise any suspicion.
These bots could also spoof and rotate different IP addresses with each login attempt, preventing the attackers’ efforts from being easily traced back or blocked at the source while obscuring the full scope of the attack.
The technological sophistication effectively hides the credential stuffing underway in plain sight. Usually, methods deployed by organizations to prevent and detect credential stuffing attempts risk impeding the ability of legitimate users to log in to the service.
For instance, blocking user logins from a wide range of IP addresses or displaying more CAPTCHAs would likely ensnare both attackers and legitimate customers alike. Moreover, the compromised devices powering the botnet attack make blocking based on IP ranges ineffective anyway. All these factors make it so difficult to mitigate the persistent challenge of credential stuffing.
Credential Stuffing Trends and Impacts
This section compiles the major credential stuffing incidents over the past couple of years to study the trends that characterize this form of attack.
- 23andMe
In October 2023, DNA genetic testing company, 23andme suffered a data breach that turned out to be a credential stuffing attack after further investigations. About 7 million people were affected and the perpetrators claimed to have released their records on the dark web.
Investigations confirmed that the attackers were able to access these accounts because their owners had used the same credentials on other websites from which they were stolen.
In short, the hackers didn’t even need to actually breach 23andme’s own systems, which is why there was initially no evidence that a data security incident had occurred.
According to the investigation report, the attackers only needed to actually access 14,000 accounts, from which they gained further access to the millions of profiles that were compromised.
- Hot Topic
In the first half of 2023, the retail chain Hot Topic suffered five different waves of cyber attacks over 5 months. These turned out to be automated credential stuffing attacks that affected the company’s websites and mobile applications.
Hot Topic only notified customers of the attacks in August, which means that the attacks were not detected in real-time. This underscores the dangerous subtlety with which credential stuffing attacks operate.
Even worse, the company couldn’t right away tell the number of users that were affected or the precise types of personal information that the unknown threat actors may have accessed. Further information was not provided for what may have been one of the biggest cyber attacks in the retail industry for the year.
- PayPal
Late in 2022, PayPal was similarly breached, with tens of thousands of accounts affected in a series of credential stuffing attacks conducted over two days. Information accessed included transaction histories, credit and debit card details, and account holders’ personal information including names, dates of birth, social security numbers, etc.
- Australian brands
It might be early in 2024, but cyber attackers couldn’t care less. Days into the new year, there was an escalating trend of credential stuffing attacks against well-known Australian brands such as The Iconic, Guzman Y Gomez, Dan Murphy’s, TVSN, and more.
The businesses affected so far range across various industries including fast food, fashion, and entertainment and public advisories have gone out encouraging people to be extra wary of suspicious activities, take precautions, and check if their information has been stolen.
The extent to which all these attacks are coordinated remains unknown. Yet, given the nature of credential stuffing attacks, it is not far-fetched to imagine that the same set of threat actors facilitated all the various attacks.
- DraftKings
Back in 2022, DraftKings suffered a credential stuffing attack that led to losses of up to $600,000. These attacks were not detected until customers started reporting issues with their accounts and the company had to investigate.
Once the accounts were accessed, the attackers tried to withdraw as much as possible from bank accounts linked to the victims’ profiles. Latter investigations showed that more than 67,000 customers were affected. The hacker, who turned out to be a teenager was arrested a few months later and was recently sentenced to 18 months in prison.
- New York State
A New York State investigation in 2022 revealed how over 1.1 million accounts were compromised in several credential stuffing attacks launched against 17 different well-known companies. At the time, the state attorney general said over 15 billion stolen credentials were being circulated across the internet.
How to Detect Credential Stuffing
As discussed already, due to the nature of credential stuffing attacks, detecting them is not a straightforward affair. In fact, from the examples given, most of the companies attacked were completely oblivious to what had happened since their defenses were not actually breached in the process of launching the attacks.
Does that mean that organizations should fold their hands and let threat actors have their way? Certainly not. Here are simple steps you can take to increase your chances:
- Monitor Changes in Site Traffic
Security Information and Event Management (SIEM) systems are great for this as they collect and analyze data from various sources including login attempts, failed logins, IP addresses, user locations, device type, and so on.
Typically, you want to look out for sudden spikes in login attempts, geographic anomalies, and so on. What matters is that there is a reliable method for continually monitoring site traffic to ensure that the organization does not miss indicators of suspicious activity.
- Proactive Threat Hunting
‘Proactive’, because, you are not simply waiting to detect suspicious activity; instead, it involves actively searching for potential threats. This could be achieved by analyzing login attempts for specific patterns, using threat intelligence feeds, or monitoring dark web forums and marketplaces for leaked credentials linked to profiles related to your website or similar services.
- Review and Analyze Security Logs
You should always review and analyze security logs periodically, with a focus on detecting suspicious and questionable patterns, especially login attempts from, say, blacklisted IP addresses. This also includes changes to user accounts, as this is one of the first steps attackers usually make once they gain access to an account.
Defending Against Credential Stuffing
Defending against credential stuffing is not the responsibility of one party; both the individual and the organization must work together to prevent these attacks. In this section, we discuss responsibilities applicable to each side.
Company Perspective:
- Educate Users and Employees on Password Hygiene
Many of the challenges with credential stuffing will be solved if users simply adopt excellent password hygiene, especially by avoiding reusing passwords or setting weak passwords.
To protect your organization’s integrity, you need to take steps to educate them about the dangers of reusing passwords, as well as implement stringent password policies that ensure that users and employees set strong passwords. Regularly guide them on how to avoid phishing emails too.
- Enable Two-Factor Authentication
2FA adds an extra layer of security and has emerged as a far more secure option compared with just using passwords.
Of course, with 2FA, there are always concerns about balancing security with usability, but user-friendly 2FA methods such as biometrics can easily accommodate user preferences. Using a password management platform such as Uniqkey can save your users 4 to 8 seconds in average login time by removing all manual hurdles through 2FA autofill. Such an automated 2FA process reduces friction in user-friendliness while keeping the system secure.
This should be a top priority if your business collects sensitive information in any shape or form from users.
- Passkeys Instead of Passwords
Passkeys are among the latest innovations in addressing the challenges of organizations with passwords.
They eliminate the reusing of compromised credentials and they provide phishing resistance – being linked to biometric verification, they cannot easily be tricked out of users. So, these provide a strengthened authentication factor, even stronger than MFA.
- Implement Risk-based Authentication (RBA)
RBA is based on zero trust and least privilege principles. It ensures that each login attempt, in real-time, is analyzed for suspicious activity, based on factors such as location, time of day, device type, and login history to access risk.
For example, if an account always logs in from location A, and there’s suddenly a login attempt from location B, the system detects the anomaly and requests additional steps to verify that the real owner of the account is authenticated.
As time passes, risk scoring is fine-tuned based on evolving threats and user behavior. This streamlines logins for trusted users and also ensures that anomalous activity doesn’t go undetected.
- Define Incident Response Plan
Cybersecurity experts strive to implement the highest necessary security standards, leaving nothing to chance, but at the same time must prepare for the worst since no security tool or method is 100% fail-proof and threats are always evolving anyway.
So, there must be a plan for when the worst happens. That is, detecting, responding to, and recovering from credential stuffing attacks. A major component of an incident response plan is assigning clear roles for response, communication, containment, and remediation, as well as other steps as the case may be.
- Leverage Artificial Intelligence
Cyber attackers never rest on their oars and many attacks are now being enhanced via AI. Those on the defense side must also leverage AI to handle attacks. Where traditional tools fail, AI algorithms can learn to identify suspicious login patterns and flag potential incidents with a high rate of reliability.
Via innovations such as continuous threat intelligence, you can adapt your defenses to emerging attack methods. But you must also remember that AI is simply a tool to augment your security efforts and it does not eliminate the need for skilled human oversight.
User Perspective
- Enable Multi-Factor Authentication (MFA)
MFA is the single most effective defense against credential stuffing. There may be some added inconvenience with being required to enter an SMS code in addition to your password when logging in to a service, but it’s an inconvenience worth enduring, especially for websites that handle your sensitive information and financial data.
- Use Strong, Unique Passwords
This is where most people get ‘lazy’. Many people still use simple password combinations and if they use a strong password, they’ll replicate the same credentials on multiple accounts.
Remembering all your passwords is a hassle, but that’s where a password manager comes in. A secure one can easily help you handle your logins without risking compromising your accounts.
- Never Share Login Credentials
Login credentials are not meant to be shared with anyone or written down. So, be extra suspicious of emails asking you to reveal your login details. This holds true if you are chatting with a customer service representative.
Most reputable organizations maintain the policy that their representatives can never request passwords from customers.
- Be Wary of Untrusted Networks
Accessing your accounts through public Wi-Fi and other untrusted networks should be avoided at all costs, especially when it comes to sensitive activities like banking or online shopping. If you must use public Wi-Fi, then get a secure VPN to encrypt your traffic. Even then, be careful of the information you share on public networks.
- Update Software Consistently
A simple step such as updating your software consistently can enhance your personal security in ways you could never imagine. Outdated software often contains vulnerabilities that attackers can easily exploit. However, with regular updates come regular security patches. Don’t ignore the notifications when they come.
No doubt, credential stuffing represents a serious threat today to enterprises and consumers. The sheer potential of credential stuffing at scale should make every CISO worried enough to draft a strategy specifically to defend against it and maintain high vigilance.
Hopefully, it must have been clear that defending against credential stuffing requires a multi-layered approach, and implementing just one kind of mechanism will never be sufficient. No single solution will eliminate it, but awareness can be raised on the nature and trajectory of these attacks so that responsible parties can take action.


