Lack of employee training causes up to 80% of business data breaches. Shocking, right? Many businesses falter in their cybersecurity efforts despite investing in technical tools, simply due to gaps in cultivating a robust security culture and providing inadequate employee training.
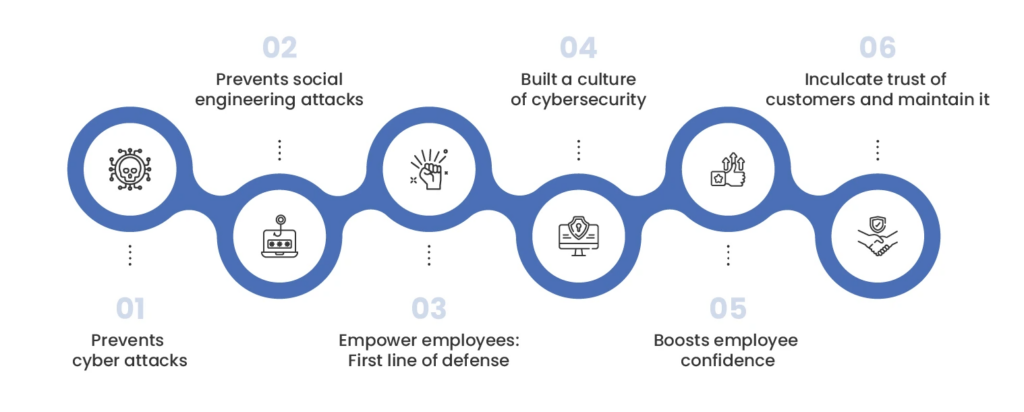
In this article, we’ll cover the various areas in which crucial attention should be paid when planning cybersecurity awareness training for employees.
Subsequently, we’ll look at how different kinds of training can be implemented for various categories of staff. Finally, we’ll go over the particular steps necessary for executing effective training.
In this article…
Topics to Consider in Cybersecurity Training for Employees

#1 Data Privacy and Security Compliance
Data privacy has been a hot topic for the past few years, especially as governments and the general public are waking up to realize how much data companies collect and store about their customers.
This has necessitated the development of strict data protection regulations like the General Data Protection Regulation (GDPR), CCPA, and others.
During cyber awareness training for employees, it’s also critical to inform employees about the latest developments in the data safety compliance space, including:
- Cross-border data transfer,
- The right to be forgotten,
- Data portability, etc.
#2 Password Security and Authentication
A good number of security breaches and ransomware attacks today involve compromised credentials, underscoring the critical importance of this area to the entire security protocols and framework.
Ensuring that these rules are followed is the main focus of the training. However, using password management software such as Uniqkey can help you enforce the policies automatically and reduce cyber risk via the following features:
- Automatic logins,
- 2FA autofill,
- Secure sharing,
- Offline storage,
- and more.
Of course, this does not remove the need for adequate training, especially on new developments within the space and, of course, on how to use the chosen password management tool for maximum results.
#3 Shadow IT and Unauthorized Software
Shadow IT is a growing problem as different types of cyber threats rise today due to various digital trends, including remote work, BYOD policies, IoT adoption, and so on. From a security perspective, you want to have an inventory of all devices and software that your employees use to carry out work-related tasks.
Here are the steps to tackle this problem:
- Examine why employees resort to shadow IT tactics. According to Statista, employees adopt shadow IT practices mainly because they feel it makes their work more efficient than using approved tools.
- Take feedback to heart and then educate employees on the security risks of shadow IT and how they affect business operations.
- During cybersecurity training for employees, expose employees to the company policy for authorizing the use of new IT systems, how employees can seek approvals to use alternatives temporarily, and IT governance in general.
#4 Email Security and Phishing
The challenge here is that the best technical defenses often fail since this is about human psychology. There is not much that can be done when an employee falls for a carefully well-crafted phishing attempt.
To avoid these, employees should be trained in the following:
- Psychology tricks that cyber attackers often employ to manipulate unsuspecting people
- How to recognize phishing attempts. Emails that come with unusual urgency to provide sensitive info or transfer a sum of money are typically red flags.
- Watching out for emails that use unusual language or have inconsistencies in communication or behavior.
- Availability of secure, verified channels for sharing sensitive info as well as how to report suspicious emails properly.
- Periodic simulated phishing exercises to demonstrate how phishing works.
- Incident Reporting and Response
Don’t forget that your employees are at the forefront of everything that takes place. They are the ones who interact with emails, handle data, share items, execute operations, and even respond to cyber threats.
So, even though they may not be security gurus, they should know what to do when an incident occurs.
Part of the aim of the training is to provide employees with skills to be vigilant observers. When they suspect that an incident has occurred, prompt reporting is crucial, and they should be equipped with knowledge of how to report it and what to do while the situation is handled.
This includes proper documentation and preserving system logs and relevant data that would help the security team in its investigation. Communication is key to enabling employees to escalate the issues they notice appropriately.
#5 Cybersecurity Hygiene and Company Policy
Finally, basic hygiene to stay safe online should not be underestimated to protect your business from cyber-attacks. Many security incidents would be avoided if you trained employees on basic principles and followed company policy on issues such as:
- Setting strong passwords,
- Avoiding public WiFi,
- Regularly updating software,
- Protecting mobile devices, and so on.
Proper training is a good avenue to introduce employees to your company’s policies, especially on issues such as BYOD and remote access for employees working from home.
Be sure to cover the scope of your policy and set principles for the acceptable use of company devices, software, and networks to protect the organization from cyber-attacks.
Cybersecurity Training for Different Types and Levels of Employees
The effectiveness of cybersecurity measures largely depends on the awareness and training provided to employees across all levels and departments. Tailoring cybersecurity training to fit the roles and responsibilities of different employee groups enhances individual understanding and fortifies the organization’s overall security posture.
Training In-House Employees
Talk about training for in-house employees often focuses exclusively on in-house employees. Despite the welcoming rising trend of remote and hybrid work, the majority of people still work on-site, and there is a lot of work that can’t be done anywhere else but on-site in health, logistics, construction, travel, and so on.
In-house employees have higher proximity to critical assets. As such, careful attention should be paid to them to ensure that they are aware of how accountable they must be to avoid any form of vulnerability that might open up the system to attackers.
Imagine an employee leaving their badge or keycard unattended at their workstation, making it easy for unauthorized individuals to access restricted areas. Or consider a scenario where an employee holds the door open for someone without verifying their identity, allowing a potential attacker to breach the premises.
These should be some of the main areas of focus during cybersecurity training for in-house staff:
- Physical security procedures are now key to overall cyber security. The aim is to protect against unauthorized access and prevent breaches through physical locations or assets.
- Secure workstation practices. Employees should be trained that items such as printers might seem harmless, for instance. Still, modern printers could pose a danger because they can connect to the internet, among other activities. And that’s only one example.
- General basics concerning file and data handling, incident reporting, email safety, and the like to ensure all-around security.
Training Remote Employees
The modern workforce is increasingly distributed as more companies allow employees to work from anywhere. This trend peaked during the COVID-19 period and the attendant lockdown. Although some major companies have ordered employees to return to the workplace, many have achieved the balance of hybrid work.
Why businesses should pay attention to cyber risks by remote and hybrid workers:
- The risk of shadow IT is higher because remote employees are more reliant on personal devices, blurring the lines between personal and professional use.
- Remote employees working from home often share devices and networks with their family members or roommates.
- Remote workers who use public workstations are exposed to the risks that come with depending on untrusted WiFi networks. One could, for instance, connect to public WiFi at a coffee shop without using a VPN, leaving their online activities and data exposed to potential eavesdropping or man-in-the-middle attacks.
- The lack of in-person IT support may make remote employees more hesitant to report suspicious activity and more likely to want to troubleshoot issues on their own.
For these reasons, it’s important to train remote employees in the following key areas to ensure that they are not inadvertently endangering operations:
- Company policies regarding the use of personal devices for work and whatever security provisions have been established to accommodate that.
- Procedures for incident reporting and response.
- Remote workers should be trained to be vigilant and equipped with information on secure channels for reporting suspicious activities as soon as possible.
- Knowledge of social engineering tactics, to ensure that they can quickly identify unusual features in email correspondences that may put things at risk.
Training Contractors and Third-Party Staff
It’s easier to manage security when you have a small team or when you are certain that only members of your team, even if large can access company software, networks, and data. However, when third-party contractors and partners are involved, you have to rethink your strategy, as well as your training approach.
You want to avoid a situation where, for instance, say your business is in e-commerce and you need a logistics service and the third-party delivery driver uses the same weak password for both their personal and work email accounts. Hackers crack the driver’s personal email and then use it to access the company email containing sensitive customer order details.
Here are some reasons why training third-party staff is so crucial to your cybersecurity posture:
- Because of the expanded attack surface by third parties, the risk of accidental and malicious data exposure is higher due to insider threats.
- No certainty that third-party staff have the same level of cyber security training for employees and accountability demanded of your organization’s staff.
- Inconsistency in security practices between the two companies can exacerbate the risks of attacks.
- Physical security is also very crucial since many contractors need to work at physical locations. Companies in supply chain, logistics, and manufacturing industries are particularly at risk.
To conduct training for third-party staff and contractors, pay attention to the following training areas:
- Be sure that they are aware of the fundamentals of online hygiene. Don’t be sure that they are sufficiently knowledgeable until you can prove it. This is key to implementing zero-trust security.
- Authentication and authorization: Contractors will have some level of privilege of entry to your systems. The scope of the privileges they get should be spelled out. The principle of least privilege is particularly important here.
- Contractors should be made aware of how their activities will be monitored and audited for security purposes. This is particularly crucial when they are working off-site.
- Like remote staff, they should be educated on reporting procedures and allowed to reach channels through which they can report incidents and suspicions.
To sum it up, ensure that contractors and third-party staff are fully aware and compliant with the contractual obligations between you and them, as well as the implications of those obligations about security.
Cybersecurity training for employees for third-party staff should be done in conjunction with their parent company for maximum results.
Training Executives
Consider the following scenario: an email lands in the CEO’s inbox, supposedly from a trusted vendor, requesting urgent approval for a large invoice. The email appears legitimate, with a familiar logo and sender name. Due to a lack of training on spotting phishing attempts, the CEO approves the invoice, unknowingly sending a significant amount of money to hackers.
Most guides for employees often focus on the rest of the company, leaving out the executives who are responsible for the day-to-day management of the company.
As mentioned, the role of executives is usually only restricted to providing ‘buy-in’, particularly in terms of resource allocation. Sure, executives need to understand cyber threats to properly prioritize and allocate resources to protect the organization’s systems and data, for at least two reasons:
- When it comes to security, executives are usually as ignorant as the rest of the workforce. The recent trend of introducing a Chief (Information) Security Officer (CSO or CISO) to the management boards of many major organizations is a huge step forward. Still, it does not resolve all the challenges.
- According to Google Cloud’s forecast for 2024, not only will CISOs become more accountable, but so will the entire C-suite and management boards. The relegation of cyber security duties to only the technical leadership is no longer acceptable.
Where executives are not as informed as they should be, then appropriate training should be conducted to ensure that they are empowered to make strategic decisions that favor the company.
After all, when it comes to access management, breaching privileged accounts, such as those belonging to executives, is the dream of every malicious actor or hacker.
Ultimately, you want executives to be able to set clear expectations concerning the future of the company and hold other employees accountable by promoting a strong cybersecurity culture. That doesn’t exempt them from following the best practices themselves, and they should be duly informed of what actions to take.
Advanced Training for IT Staff
In 2020, British Airways was fined a whopping £20 million for a data breach that affected over 400,000 customers. The breach was caused by a failure to implement proper security measures such as multi-factor authentication to protect customer data, which is a violation of data protection regulations.
All members of staff might need some basic training, but advanced training is reserved for the IT staff. Of course, IT professionals are expected to be conversant with the landscape and various protection methods available to secure company data and assets.
However, the landscape is constantly, rapidly evolving and even some techniques that worked well just a couple of years ago are now falling out of favor. IT staff need to be:
- Educated on how to keep up with the pace of change in the industry and maintain a high-security posture for the organization at all times,
- Kept conversant with developments in the compliance and regulatory space to ensure that they are not breaking any rules, especially not priority issues such as data protection.
- Trained in principles of penetration testing, ethical hacking, cryptography and secure coding, cloud security, digital forensics, threat intelligence, and so on.
This will help them to cover various bases in the quest to ensure that high standards of security are achieved to stay on top of cybersecurity.
How to Create a Cyber Security Awareness Training Program
1. Conduct Risk Assessment
- Identify your assets. These include data (consumer info, financial records, intellectual property), hardware, software, networks, and so on that are used within the organization.
- Rank your assets according to their criticality and sensitivity, considering the impact a data breach would have.
- Identify the weaknesses in your security posture by consulting with experts and monitoring industry trends.
2. Define Goals and Objectives
- Define the specific goals and objectives you want to achieve.
- Identify your target audience. This will ensure that your goals are geared towards the right category of staff.
- Consider industry-specific regulations and standards in setting cybersecurity training objectives.
3. Gain Leadership Buy-in
- Approach the board to secure their commitment. Highlight the costs of inaction, which could include economic losses, operational disruption, and brand reputation damage.
- Demonstrate ROI on cost savings through the reduced risk of breaches and improved productivity among staff.
- Encourage the leadership to participate or create separate, specialized training for them
4. Design Engaging Training Modules
- Use a variety of formats videos, simulations, quizzes, role-playing scenarios, and the like. Don’t rely solely on lectures.
- Employ real-world case studies to show how minor mistakes can lead to major breaches.
- Ensure that complex topics are broken down into bite-sized modules.
- Be realistic about content delivery. Focus on what’s most relevant and prioritize activities that employees can go on to implement.
5. Monitor and Evaluate Effectiveness
- Based on the goals you have previously set, establish KPIs to measure the effectiveness of the training.
- Measure the KPIs before and after the training to track the rate of change properly.
- Assess completion rates on training modules to determine how engaging the content is and whether the program is effective or not.
6. Implement Continuous Training
- Stay up to date on the constant evolution of the threat landscape. A principle taught today might be rendered obsolete in the next few months.
- Create refresher learning modules to reinforce understanding and establish a culture of cybersecurity consciousness.
- Integrate key elements of the training into the onboarding process for new hires to ensure that they are equipped with all they need from the get-go.
Top Cybersecurity Training Programs for Teams
CIRA Cybersecurity Awareness Training for Small Teams
CIRA’s cybersecurity awareness offering contains various online courses for small teams. It also features automated phishing simulations sent once a month, a personalized cyber risk score for each user, an admin dashboard to assess training completion, and so on.
Employees are required to take remedial training courses depending on their cyber risk level, as well as annual refresher classes. There is also a full solution for organizations with more than 50 employees and IT teams.
Infosec Institute Cybersecurity Training
Infosec’s cybersecurity training is tailored to different roles within the company, with over 2,000 resources available. Its training approach also features live boot camps as well as self-paced learning.
For technical teams, certifications are available to scale their skills. In addition, leaders can track and measure the impact of training efforts through regular assessments.
MIT Sloan School of Management Cybersecurity Leadership for Non-Technical Executives
This is a live in-person and intensive two-day leadership training holding at MIT during Fall 2024.
It will cover topics around digital business and IT, organizations & leadership, strategy and innovation. This represents a great opportunity for business leaders to gain from real-time interaction and enhance their security capacity for their teams. Participants will be issued a certificate of completion afterward.
Security Blue Team Corporate Team Training
The Security Blue team offers corporate discounts on various training programs and certifications, including courses on threat intelligence, incident response, security fundamentals, phishing analysis, and so on.
Three or more employees from the same organization represent a team and can access corporate features such as team leader dashboards to track training progress, as well as discounted access to the gamified security lab, Blue Team Labs Online, which offers downloadable challenges.
Free and Paid Online Courses
Introduction to Cybersecurity Fundamentals | Coursera
- Title: Introduction to Cybersecurity Fundamentals
- Provider: Kevin Cardwell (Coursera Instructor Network)
- Platform: Coursera
- Duration: 2 hours
- Level: Beginner
- Price: Free
- Topics Covered: cybersecurity concepts, the psychology of cyber attacks, risk mitigation, passwords and authentication, email spoofing, data encryption, documentation and reporting
The Complete Cyber Security Awareness Training for Employees | Udemy
- Title: The Complete Cyber Security Awareness Training for Employees
- Provider: SIA Global Security
- Platform: Udemy
- Duration: 2.5 hours
- Level: All level
- Price: $12
- Topics Covered: social engineering, cyber threat detection, phishing attacks, malware protection, password protection, authentication, VPN, data encryption, cloud security, etc.
Intro to Cyber Security – Online Cyber Security Course – FutureLearn
- Title: Introduction to Cyber Security
- Provider: The Open University
- Platform: FutureLearn
- Duration: 8 weeks (3 hours weekly)
- Level: Introductory
- Price: $39.99 monthly
- Topics Covered: threat landscape, authentication, malware, networking and communications, cryptography, network security, security risks, etc.
Introduction to Cybersecurity | Codecademy
- Title: Introduction to Cybersecurity
- Provider: Codecademy
- Platform: Codecademy
- Duration: 3 hours
- Level: Beginner
- Price: Free
- Topics Covered: cybersecurity standards; cyber threats; cryptography, authentication & authorization; network security basics, securing personal devices, etc.
Google Cybersecurity Certificate – YouTube
- Title: Google Cybersecurity Certificate
- Provider: Google Career Certificates
- Platform: YouTube
- Duration: > 13 hours
- Level: Beginner
- Price: Free
- Topics Covered: cybersecurity risks and threats, networks and network security, basics of computing security, network threats and vulnerabilities, incident detection and response, etc.
Cyber Security Training for Beginners | Edureka – YouTube
- Title: Cyber Security Training for Beginners
- Provider: edureka!
- Platform: YouTube
- Duration: > 100 hours
- Level: Beginner
- Price: Free
- Topics Covered: cybersecurity threats, types of cyber attacks, NIST cybersecurity framework, cryptography, penetration testing, ethical hacking, password security, etc.
Free Online Cyber Security Course with Certificate | Great Learning
- Title: Introduction to Cyber Security
- Provider: Great Learning
- Platform: Great Learning
- Duration: 2.5 hours
- Level: Beginner
- Price: Free
- Topics Covered: cybersecurity key concepts, ransomware, cryptography, security system design, authentication & authorization, etc.
⚠️Disclaimer: This article is for informational purposes only and does not constitute an endorsement of any courses or programs mentioned herein. We are not affiliated with these courses or programs. We advise you to conduct your own research before enrolling in any course.
Prepare Your Employees
The people at an organization are an integral part of cyber security, and employees should be carried along on all matters to ensure that security is properly implemented. In this day and age, cyber security is no longer an add-on for a business; it is about the life of the organization itself.
Therefore, if you imagine a secure future for your organization, choose to invest in your people today by empowering them to maintain a high level of security consciousness in all things.


