The NIS2 Directive was proposed by the European Commission in December 2020 to create a common level of cybersecurity across the union. NIS2 stands for Directive on Measures for Network and Information Security. In tandem with the Cyber Resilience Act, the NIS2 directive is poised to shape the future of cybersecurity in Europe.
This post will talk about the impact of the NIS2 directive on various sectors, discuss how businesses can prepare for the changes, and most importantly, it will help business users wrap their heads around the topic with minimal effort.
Table of contents
What is the NIS2 Directive?
The NIS2 Directive (Directive (EU) 2022/2555) is a European Union legislative act that aims to establish a high common level of cybersecurity for entities operating in the European Union.
It primarily targets essential services like energy, transport, water supply, digital infrastructure, public administration, finance, etc. along with other important sectors like food, postal services, and digital service providers. Its goal is to ensure the implementation of robust risk management measures for network and information systems. And it mandates the immediate reporting of security incidents.
EU member states have until October 2024 to translate NIS2 into national law. In effect, companies that the NIS2 covers have until the same time to build compliance through the continuous enhancement of their cybersecurity capabilities.
💡To learn more about cyber regulations in Europe, we’ve provided a detailed list here.
The Timeline of the NIS2 Directive
| Time | Event |
| December 2020 | NIS2 is proposed by the European Commission |
| November 2021 | European Parliament adopts its negotiating position |
| December 2021 – February 2022 | Trilogue negotiations between Parliament, Council, and Commission commence |
| February 2022 | Political agreement is reached |
| May 2022 | European Parliament votes to adopt NIS2 |
| November 2022 | NIS2 is officially published in the EU Official Journal |
| January 2023 | NIS2 Directive comes into effect |
| October 2024 | Deadline for EU member states to transpose NIS2 into national law |
NIS2 Directive: Key Requirements in Short
- Risk Management
- Implement strong incident management plans.
- Secure your supply chain.
- Enhance network security measures.
- Implement stricter access controls.
- Encrypt sensitive data.
- Corporate Accountability:
- Management oversees and approves cybersecurity plans.
- Management receives cybersecurity training.
- Potential penalties (liability, bans) for management in case of breaches.
- Reporting Obligations:
- Mandatory reporting of major cyber incidents impacting services.
- Strict timelines for notification (e.g., 24-hour “early warning”).
- Business Continuity:
- Develop a plan for service restoration after cyber incidents.
- Establish emergency procedures for response.
- Create a crisis response team.
NIS2 minimum requirement breakdown
This NIS2 site has broken down 10 minimum requirements for businesses to comply with the new NIS directive.
1. Risk assessment policies
Organizations must establish clear and comprehensive risk assessment policies. This includes identifying vulnerabilities in their systems, monitoring potential attack surfaces, and conducting regular security audits.
2. Evaluation of security measures
Businesses need to have procedures in place to regularly evaluate the effectiveness of their existing security measures. This allows for continuous improvement and adaptation to evolving threats.
3. Encryption & Cryptography Standards
The NIS2 Directive mandates the use of encryption wherever relevant. This will impact the security of data in transit and at rest across and within organizations.
4. Incident Response Plan
A clear and documented plan of action is critical for successful computer security incident response. According to NIS2, this plan should outline procedures for detection, containment, eradication, and recovery in the event of a cyberattack.
5. Secure System Procurement & Development
Organizations must have policies for secure procurement, development, and operation of information systems. This includes procedures for identifying and reporting vulnerabilities in acquired systems.
6. Cybersecurity Training & Hygiene
The observation of security best practices can thwart a lot of tragedies. Hence, organizations should establish protocols for basic computer hygiene and train all employees to abide by best practices.
7. Data Access Controls
The principle of least privilege combined with strict access control measures must be employed. Companies should maintain an inventory of all relevant assets and monitor how they are accessed and handled. identity management tools like Uniqkey can make a great difference in this regard.
8. Business Continuity Planning
Up-to-date backups and a plan to regain control of critical IT systems during and after security incidents are key to business continuity planning. Having this plan in place is essential for NIS2 compliance.
9. Multi-factor Authentication
Organizations should leverage multi-factor authentication and other advanced solutions (continuous authentication, voice/video/text encryption) where appropriate to strengthen access control and communication security.
10. Supply Chain Security Management
The NIS2 Directive emphasizes the importance of securing the supply chain. A holistic view of overall supply chain security risk is required.
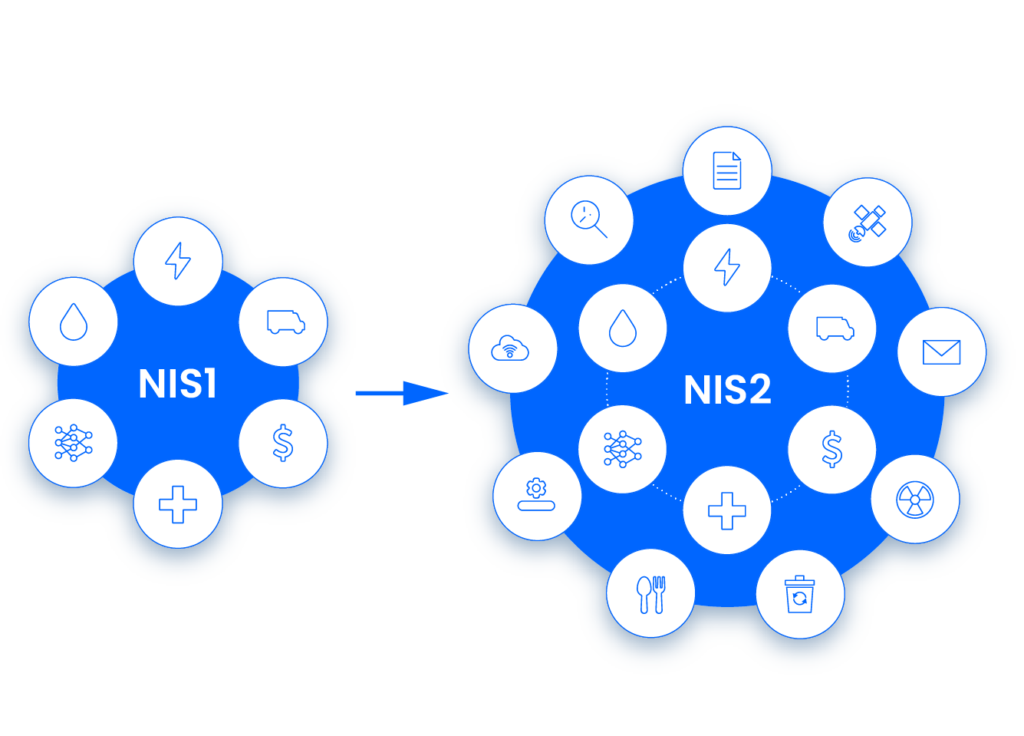
Comparing NIS2 and NIS1
| Feature | NIS1 (2016) | NIS2 (2022) |
| Goal | Basic level of cybersecurity for essential services | A high common level of cybersecurity for essential and important entities |
| Scope | Limited to operators of essential services in specific sectors (energy, transport, etc.) | Expands to include additional sectors (waste, postal services, etc.) and important entities (e.g., online marketplaces) |
| Security Requirements | Less stringent, focused on risk management principles | More prescriptive, outlining specific baseline measures (encryption, incident response plans) |
| Incident Reporting | Less specific reporting obligations | Stricter reporting requirements, mandating reporting of significant incidents within 24 hours |
| Enforcement | Weaker enforcement mechanisms | Stronger enforcement with the potential for significant fines for non-compliance |
Sectors in the EU covered by the new NIS directive
Sectors covered by NIS2 are divided into two categories.
- Category one: Essential entities
- Category two: Important entities
Essential entities include Energy, health, transport finance, water supply, digital infrastructure, space, and public administration.
Important entities include digital providers, postal services, waste management, food, manufacturing, chemicals, and research.
Both the essential and important entities are critical to the survival of the European economy and companies in both categories are liable to comply with the directive. The essential entities, however, have received a higher criticality rating.
Essential Entities under the NIS2 Directive Across the Union
| Sector | Annual Economic Impact | Workforce (Millions) | Key Security Risks |
| Energy | €250 Billion | 1.6 | Supply Chain Risks, Interconnected Systems, Aging Technology, Advanced Persistent Threats, ICS Vulnerabilities |
| Health | €1073 Billion | 14.3 | Lack of Standardization, Aging Technology, Sensitive Information, Insufficient Resources, Interconnected Systems, Lack of Employee Training |
| Transport | 5% GDP | 10 | Ransomware Attacks, Threats to Safety Systems, Limited Investment in Security, Connected Devices |
| Finance | €197 Trillion Payments | 2 | Phishing, Website Spoofing, Ransomware Attacks, DDoS, Social Engineering, Supply Chain Attacks |
| Water Supply | Unspecified | 1.5 | Legacy Systems, Third-Party Risks, Limited Resources, Physical Threats, Insider Threats |
| Digital Infrastructure (Data Centers) | €85.4 Billion | Unspecified | Ransomware Attacks, Third-Party Challenges, Physical Security, Lack of Personnel, Compliance Issues |
| Public Administration | 22.1% GDP | Unspecified | Ransomware Attacks, Phishing Attacks, State-Sponsored Attacks, Lack of Awareness, Large & Complex Systems, Limited Resources |
| Space | Unspecified | Unspecified | Sophisticated Cyberattacks, Supply Chain Risks, Human Error |
The potential impact of the NIS2 on cybersecurity in the EU
The European Commission has envisioned the new NIS directive as a way to enhance the overall security health of verticals across Europe. While its true impact will be witnessed by the world over the next few years, we can discuss the vision itself. Here, we’ll analyze the potential impact of the directive on the digital infrastructure sector.
The data centres, CDNs, and other digital infrastructure providers will see some significant changes in security management owing to the directive.
- Physical Security Upgrades: There will be stricter requirements for physical access control, potentially involving security cameras and stricter monitoring.
- Enhanced Incident Response: There will be more emphasis on robust plans for cyberattacks, including clear roles, communication protocols, and procedures for evidence collection.
- Increased Oversight: We can expect increased vigilance by competent authorities to ensure that security standards are met.
- Market Boost for Security Solutions: The demand for innovative cybersecurity solutions will go up with companies striving to meet the new common cybersecurity level. This fosters competition and innovation in the digital infrastructure sector.
The impact is likely to be similar across verticals with obvious variations. Together with the CRA which doubles down on the security of all products with digital elements, the NIS2 is sure to impart lasting stability to the industries of Europe.
Tips for companies preparing for NIS2 compliance
- Create comprehensive policies for access management, risk assessment, and incident response
- Build an incident response team and train them to handle security breaches through drills
- Mandate the use of password managers by employees, and aim for centralised access control and monitoring with platforms like Uniqkey (helps cover 6 out 10 NIS2 measures)
- Partner with regular vulnerability assessment providers
- Integrate security testing into the development and supply chain pipelines
ℹ️ We’ve built the complete website to provide in-depth information on NIS2, helping businesses understand its requirements, achieve compliance, and avoid fines.


