Developed by Delano, the concept of one-time secrets encompasses various terms such as ‘self-destructing messages‘ and ‘single-use links‘, all of which refer to the idea of secret messages that can be opened and viewed only once. This method is a secure way to share confidential information.
Here is how a one-time secret works
Step 1: Encrypting the secret
The sender encrypts the secret message using a secure algorithm.
Step 2: Link generation
The encrypted message is embedded within a unique URL. This forms a one-time link. Once the link is opened and viewed, the URL loses validity.
Step 3: Sharing the link and the password
The sender shares the single-use link and the password needed to decrypt the secret message with the intended recipient
Step 4: Opening the Link
The recipient clicks the link and is prompted to provide the decryption key (the password sent by the sender). The recipient’s screen shows the secret message upon entering the correct password. Once the recipient closes the message, it cannot be reopened.
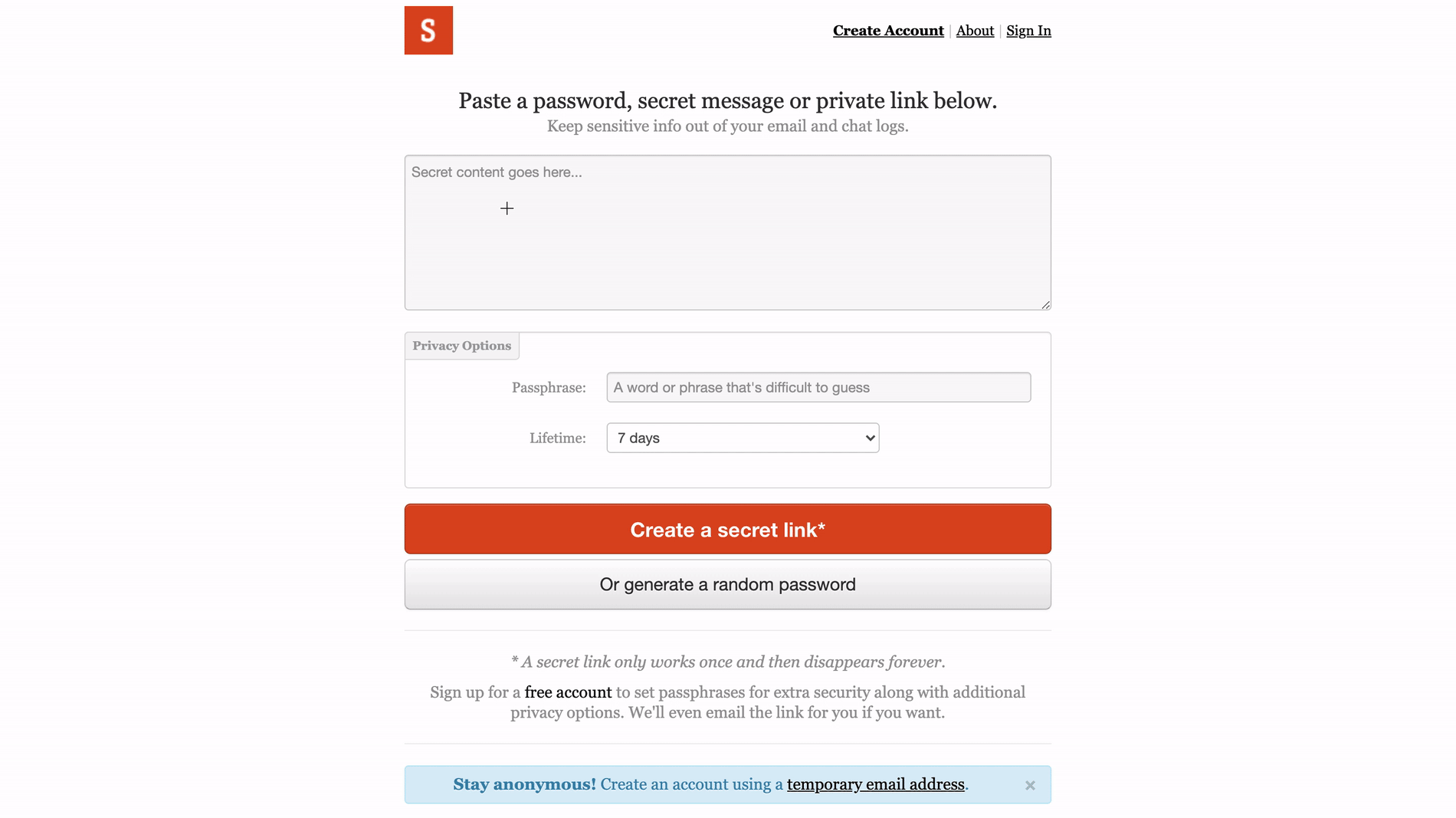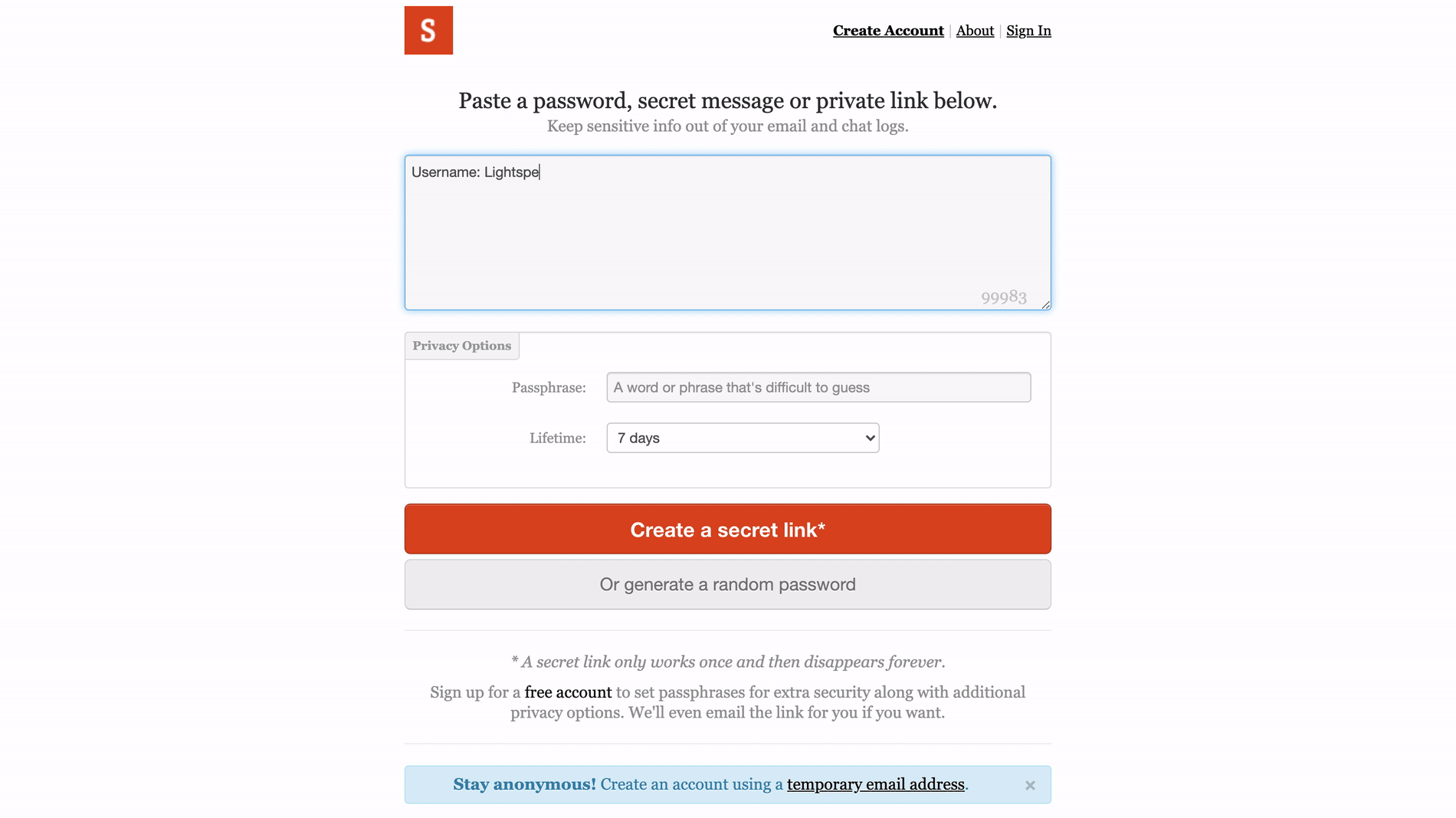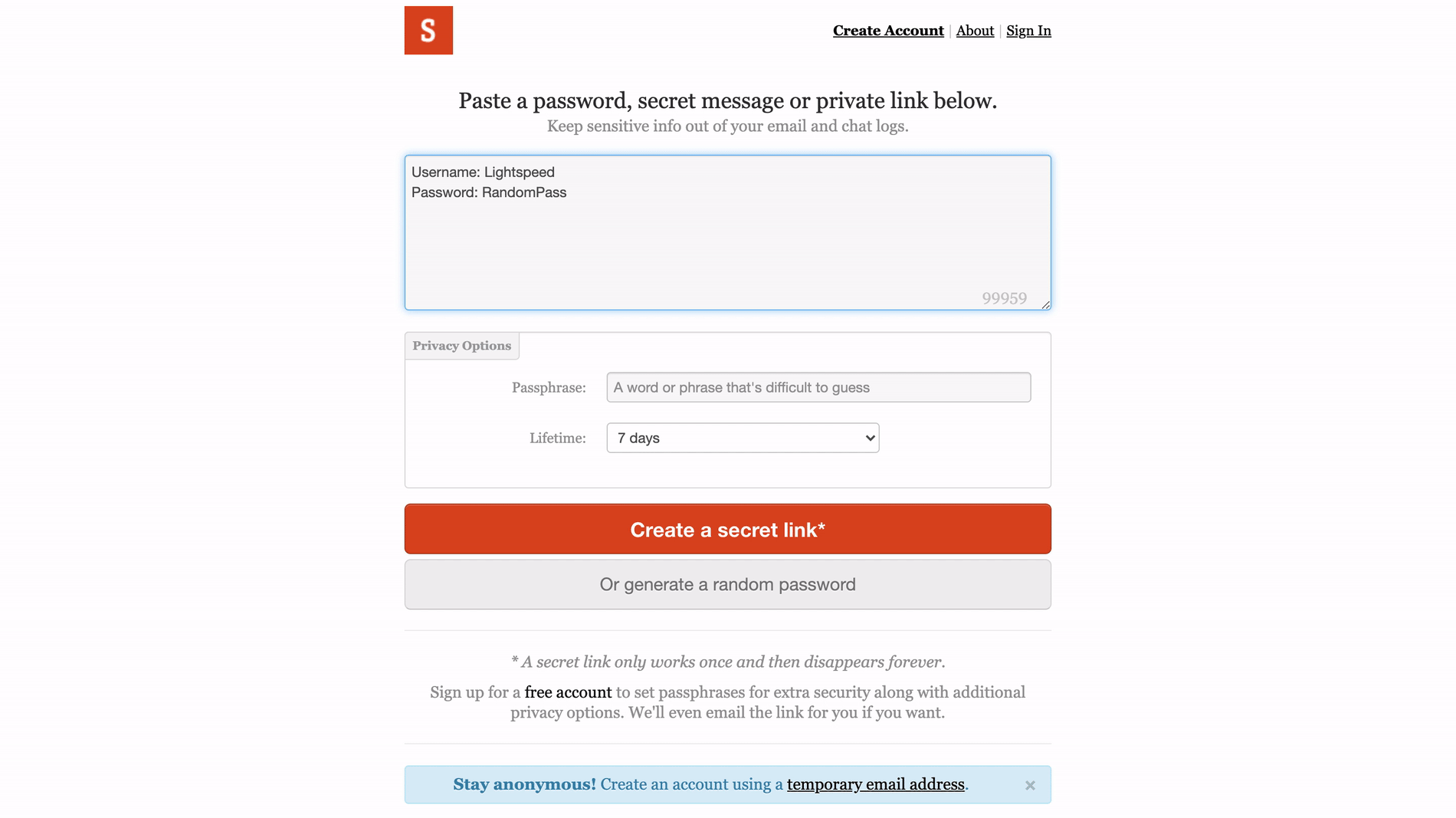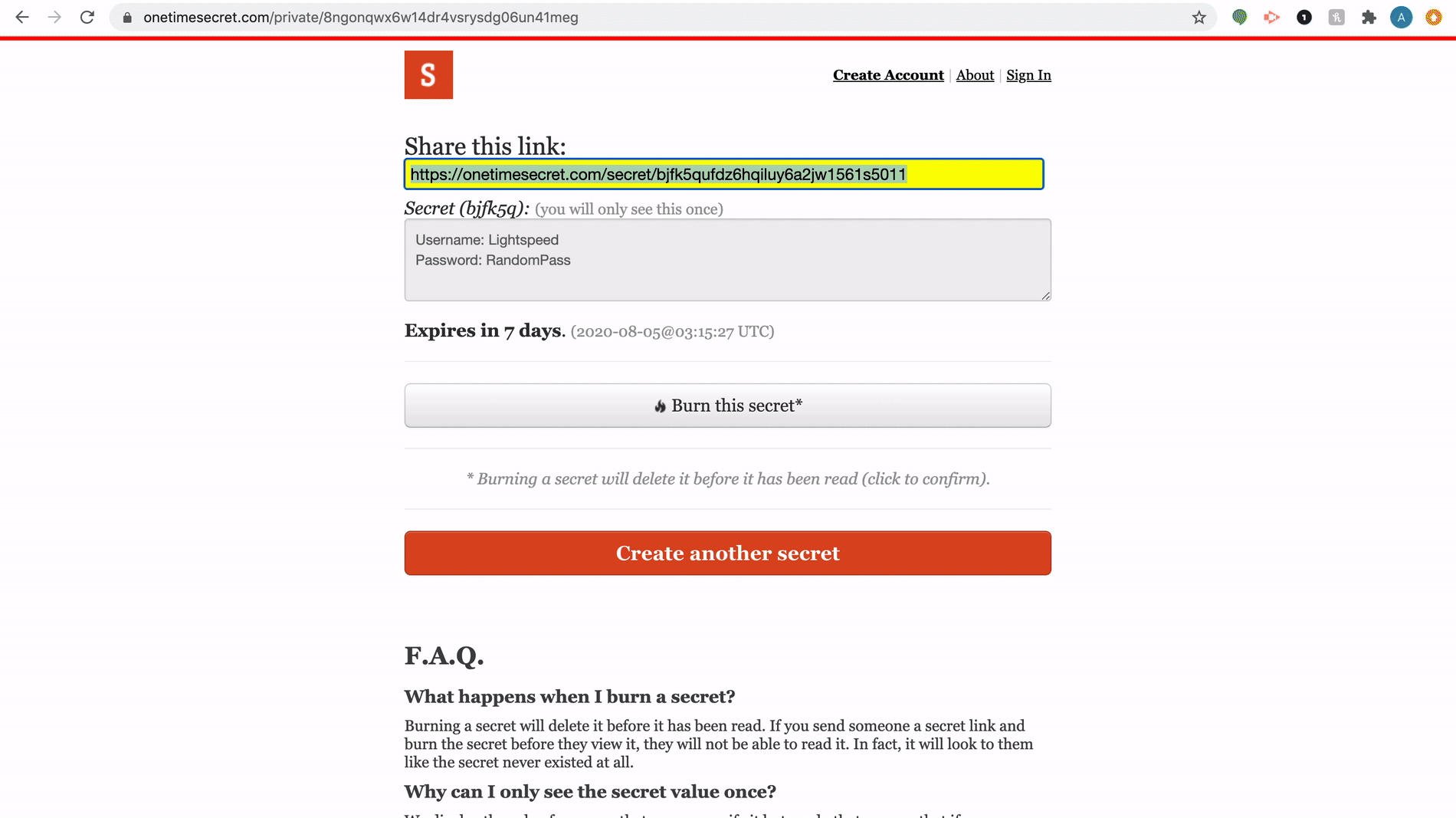
🛈 Once the secret is viewed or timed out, the link becomes erroneous and shows, “Unknown secret. It either never existed or has already been viewed.”
Use of a one-time secret for sharing sensitive information
Several online service providers allow you to send sensitive information and offer one-time secret-sharing services. The concept can be traced back to the 1940s and was used by the US military in the 1950s. It was popularized in the commercial sector by a company called One-time Secret. The code was open source and has been adopted by many organizations.
Security features of one time secrets
- The secret is encrypted and password protected, hence it is immune to interceptions and man-in-the-middle attacks.
- The password-protected secret ensures the message isn’t tampered with in transit.
- The sender can set an autodestruct timer for the secret. Thus, even if the message is not opened, it will be destroyed after a certain period.
People have used this method to share credentials with third-party contractors, send passwords to team members, and share API keys and sensitive code. When compared to sharing passwords and sensitive information over text messages or email in plaintext, one-time secret presents a secure method of secret-sharing.
Is a one-time secret secure?
A one-time link has certain security benefits compared to sharing secrets in plaintext via email and messages. At least, your one-time secret message is encrypted. However, that does not make it the most secure option for sharing sensitive information – not nearly.
Security risks associated with a one-time secret
Secret links and self-destructive messages may ensure the integrity of the secret, but they do not offer access control. Once you have shared the link and the password to open the message, you cannot control how the secret is stored, who else sees it, and how it is used.
Your secret may not be stored securely
The whole point of using a single-use link is defeated if the recipients of the secret copy it and store it in unsecured mediums. It often occurs that passwords shared via one-time secret are stored in plaintext in online accounts, or written down on paper.
You cannot enforce access control with a one-time secret
While you can determine when a secret message is deleted, you cannot control how long the recipient keeps or uses the secret. For instance, if you share the credentials for an online account with a freelancer, they might have access to it even after finishing their work with you.
The decryption key for the encrypted secret is often shared in plain text
If someone is using one-time links to share sensitive information, that user presumably doesn’t have access to a better way of sharing the decryption key or the password with the recipient. So, unless the user delivers the password in person, they are in all likelihood sharing it through an unsecured medium. It is as good as sharing the sensitive information itself in plain text.
Moreover, documents and images shared through a self-destructive link can be traced through stored metadata, thus it defeats the purpose.
Alternative Tools to Create One-Time Secret Links
When it comes to securely sharing sensitive information, One-Time Secret Links offer a safe and efficient solution. While many tools are available for creating these self-destructing links, not all provide the same level of security and ease of use. Let’s look at some popular tools that make these disappearing links:
- Privnote: Privnote is free and easy to use. It lets you send encrypted messages that delete themselves after being read. It’s perfect for sharing secrets without leaving any trace.
- Burn Note: With Burn Note, you can set a timer on your secret message. Once the timer runs out or the message is opened, it vanishes. It’s like your message has a built-in self-destruct button!
- 1ty.me: This simple tool creates a secure, one-use link for your message. After someone reads it, the link stops working. It’s a straightforward way to share private information.
- SafeNote: SafeNote keeps your sensitive info secure with encrypted, self-deleting notes. Once someone reads your note, it’s permanently deleted. You can trust that your secret stays secret.
- Sendinc: While Sendinc focuses on secure emails, it also offers one-time links for encrypted messages. It makes sure only the person you want can unlock and read your information.
- ZeroBin: ZeroBin is an open-source tool that lets you share secret messages. It has end-to-end encryption (which means it’s super secure), and your message is destroyed after being viewed.
Password managers present a better way of sending sensitive information securely
The secure password-sharing feature provided by password management tools such as Uniqkey is more efficient and safe than one-time secrets. Additionally, it enhances the capabilities of one-time secrets by offering secure TOTP (Time-based One-Time Passwords).
Here’s why using a business password manager is a better choice for sharing secret information:
💡Instead of sharing the credentials in plaintext, you can share time-bound access to a specific service with colleagues.
This has two benefits.
- Your credentials aren’t copied and stored by anyone else
- You can control both the time and the extent of access offered
Password managers let you monitor the people who access your services
You stay aware if your credentials are being used in an unusual manner or by an unauthorized person
The sharing process is simple and fast
Sharing a one-time secret involves multiple steps – it’s time-consuming and tedious. A password manager makes secret-sharing extremely easy.
It’s safe to say that password managers make an excellent medium to share a secret apart from the much-needed capabilities of storing passwords securely, suggesting safe passwords, and filling in data. Once you get an enterprise-grade password manager, you can quit worrying about the safety of one-time secrets.


