While shadow IT (or the use of software, systems, or devices without a company’s explicit approval) might make some employees’ jobs easier, the practice also has significant drawbacks that organizations need to address.
In this article, we will go through what shadow IT is, why it matters in terms of data breaches and data leaks, and all the steps your IT team can take to minimize its effects – including using shadow IT detection & monitoring tools. Lastly, since shadow IT is somewhat inevitable), we will evaluate the possibility of harnessing its potential rather than completely eliminating it.
What is Shadow IT?
Shadow IT occurs when employees or departments adopt or deploy technologies to meet their needs – but do not notify the IT team that they are doing so.
Some common examples of shadow IT include unauthorized:
- software applications
- cloud services (like Dropbox)
- communication tools (like WhatsApp or Trello)
- personal devices for work-related tasks.
For example, think of accessing a personal Dropbox account, using Skype (when the company has WebEx), or copying files from or to a thumb drive.
These are all instances of unauthorized use of digital tools that could potentially put your organization at risk if they were to be compromised.
Why Does Shadow IT Occur in Businesses?
Due to the rapid evolution of cloud technologies and Software-as-a-Service (SaaS), shadow IT has become more prevalent and complex in recent years.
In many cases, business units also began adopting new applications independently to drive digital transformation; for instance, file-sharing programs, project management tools, and cloud-based services like the ones mentioned above.
The result? Between 30% and 40% of IT spending in large enterprises is shadow IT, with companies wasting more than $135,000 a year on unnecessary SaaS licenses and tools. What’s more, a 2023 report showed that 65% of all SaaS apps are unauthorized apps (or apps that have not been approved by the IT department).
Examples of Shadow IT
As explained, Shadow IT refers to the use of IT systems, devices, software, applications, and services without explicit IT department approval. It has been widely adopted in many organizations due to its flexibility and convenience. However, while it poses certain risks, it can also provide benefits when managed appropriately.
Let’s look at some examples to understand how Shadow IT is being utilized:
Cloud Services: With the advent of cloud computing, employees are increasingly using third-party cloud services such as Google Drive, Dropbox, or OneDrive for file sharing and collaboration. These tools provide easy access to data from any location and facilitate collaboration, but they are often used without IT department oversight.
Communication Tools: Tools like Slack, WhatsApp, or Microsoft Teams are often used by employees for quick, informal communication. These platforms can improve productivity by allowing for instant communication. However, they can also pose a security risk if sensitive information is shared without proper encryption or security protocols.
Personal Devices: Employees often use their personal devices for work, known as Bring Your Own Device (BYOD). While this can improve flexibility and work-life balance, it can also create vulnerabilities if these devices are lost, stolen, or infected with malware.
Unsanctioned Software: Employees may download and install software that isn’t approved by the IT department. This could range from project management tools to graphic design software. While these tools can aid in productivity, they may also introduce compatibility issues or security vulnerabilities.
Hardware: Beyond software, Shadow IT can also extend to hardware like personal routers, storage devices, or even servers that employees may install to improve their workspace. Such devices can pose serious security risks if they aren’t properly configured or maintained.
Shadow IT Security Risks and Challenges
Shadow IT creates invisible and serious security risks for organizations because when an employee uses unauthorized tools, applications, cloud services, or devices, this increases the chance of security breaches (in fact, a study by IBM has shown 83% of respondents have suffered at least one company data breach where sensitive data was compromised).
Many of these tools also lack robust security measures, such as strong encryption or reliance on weak or default credentials.
If your organization needs to work under specific regulations and data protection laws, such as CCPA or GDPR, shadow IT can also lead to compliance violations – especially if your IT department cannot see or control the data that is being stored or shared. We know, for example, that one-third of all successful cyber attacks come from data stored in shadow IT.
Lastly, shadow IT is often difficult to integrate with existing infrastructure, something that can easily lead to compatibility issues, data silos, fragmented systems, inefficient resource use, uncontrolled costs, and redundancy.
🥇 Get the award-winning Shadow IT Monitoring Tool — for free. Uniqkey’s password and access management tool has been rated under the top 50 security products by G2 and ranked #1 by Geekflare, Comparetech, & European Business Review. Try Uniqkey for free and get the protection for your business you need.
Latest Shadow IT Statistics
Here are some recent and relevant statistics on Shadow IT:
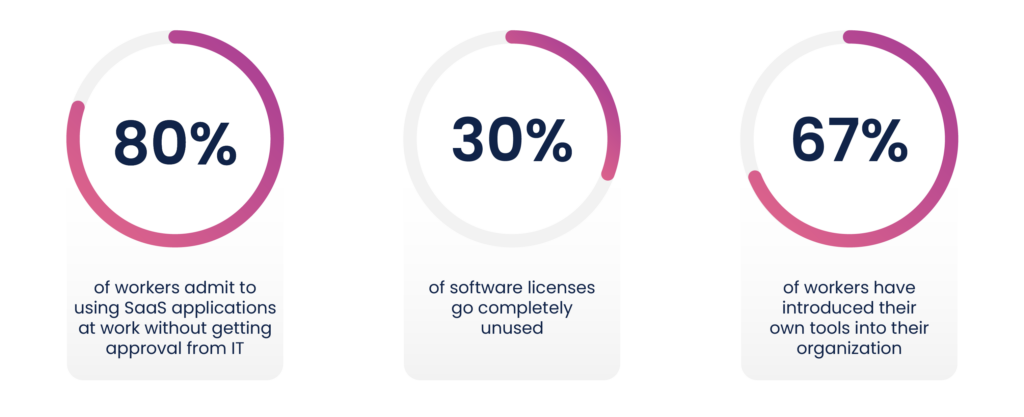
- 80% of workers admit to using SaaS applications without getting IT approval.
- Shadow IT cloud usages estimated to be 10x the size of known cloud usage.
- The average company have 975 unknown cloud services.
- Most companies have over 108 known cloud services.
- 37% of IT leaders say security policies are the biggest challenge to an effective employee digital experience.
- Shadow IT accounts for 30-40% of IT spending in large enterprises.
- 82% of IT leaders say users push back when management tried to dictate which tools should be used.
- 67% of workers have introduced their own tools into their organization.
- 1 out of 3 employees at Fortune 1000 companies use cloud services that IT hasn’t approved.
- 53% of teams refuse to only use IT-approved tools.
👀Source: 124+ Cybersecurity Stats IT Leaders Need To Know in 2023
These statistics should provide an in-depth understanding of the prevalence, risks, and challenges associated with Shadow IT.
Different Elements of Shadow IT
Shadow IT is a multifaceted concept and can be broken down into different elements based on the type of technology used, the way it’s employed, and the reason for its use. Here are some of the key elements of Shadow IT:
- Software as a Service (SaaS): SaaS applications are a common form of Shadow IT. They are easy to access and often free or available at a low cost. Examples include file-sharing applications like Dropbox, productivity tools like Google Docs, or communication platforms like Slack. Employees might use these tools for their convenience and ease of use, often without the knowledge or approval of the IT department.
- Hardware: This includes any physical devices used without the IT department’s consent, such as personal laptops, smartphones, or tablets used for work purposes. It could also include routers, servers, or storage devices set up by employees to enhance their workspace.
- Platforms as a Service (PaaS): These are platforms that allow users to develop, run, and manage applications without needing to deal with the underlying infrastructure. Examples include Microsoft Azure, Google Cloud, and AWS. They can be used for creating custom applications to fulfill specific business needs, often bypassing IT protocols.
- Infrastructure as a Service (IaaS): This involves the use of virtualized computing resources over the internet, such as virtual machines, storage, or networks. Examples include AWS, Google Cloud, and Microsoft Azure. While these services offer flexibility and scalability, their use can also lead to security vulnerabilities if not properly managed.
- Bring Your Own Device (BYOD): This refers to the practice of employees using their personal devices for work purposes. While this can increase convenience and productivity, it can also pose security risks if these devices are lost, stolen, or infected with malware.
- Personal Emails and Accounts: Using personal email accounts for work-related communication is another form of Shadow IT. While it might seem harmless, this practice can lead to data leakage, making it difficult for the organization to control information flow.
- Unapproved IT Providers: This refers to the use of IT service providers or consultants without the explicit approval or knowledge of the IT department. These providers may not follow the company’s IT policies, leading to potential security risks and compliance issues.
Each of these elements poses different challenges and risks for an organization. However, they also represent increased productivity, collaboration, and innovation opportunities. Understanding these elements can help organizations manage Shadow IT effectively, harnessing its benefits while mitigating potential risks.
How to Discover and Manage Shadow IT
The best way to prevent these issues is to identify whether your organization is using any shadow IT. Three best practices you should consider for doing so are governance policies, IT department engagement, and employee education. Let’s quickly go through each in some more detail.
- Governance policies: Always establish policies and guidelines about the usage of technology resources within your company – and make sure you communicate their consequences clearly.
- IT department engagement: Try to encourage open communication and collaboration between employees and the IT department. You can do this by fostering an environment where employees feel comfortable approaching IT with their technology needs and challenges.
- Employee education and awareness: Don’t forget to conduct regular training sessions and awareness campaigns to educate employees about the risks associated with shadow IT.
The Chief Information Officer (CIO) and IT teams play a crucial role in managing shadow IT. For one, the CIO can provide strategic leadership, defining policies, procedures, and frameworks. They can work alongside the IT team to ensure technology resources are used in a controlled and compliant way.
Shadow IT Costs and Consequences
The cost of Shadow IT can be quite significant, and it extends beyond just the financial aspect. Despite years of modernization initiatives, CISOs are still grappling with this old-school issue. Unvetted software, services, and equipment can potentially introduce a host of vulnerabilities, entry points for bad actors, and malware, thereby posing a considerable security risk.
Consider the figures from Gartner, which found that 41% of employees acquired, modified, or created technology outside of IT’s visibility in 2022, and this number is expected to climb to 75% by 2027. Meanwhile, Capterra’s 2023 shadow IT and project management survey found that 57% of small and midsize businesses have had high-impact shadow IT efforts occurring outside the purview of their IT departments.
While offering flexibility and user convenience benefits, shadow IT also comes with significant costs that organizations must be aware of. These costs can be broadly categorized into direct and indirect costs.
Direct Costs:
- Unnecessary Expenses: Without proper oversight and control, employees might subscribe to redundant services or purchase more licenses than necessary, leading to wasteful spending. For example, different teams might subscribe to similar project management tools, creating unnecessary costs.
- Increased IT Support: Shadow IT often leads to compatibility issues and increased support requests. The IT department must spend time and resources troubleshooting problems related to unapproved software or hardware.
- Security Breaches: Shadow IT can result in security vulnerabilities that cybercriminals can exploit. The cost of a data breach can be enormous, considering the financial penalties, loss of customer trust, and damage to the company’s reputation.
Indirect Costs:
- Loss of Productivity: Employees who use unapproved or unsupported tools might face compatibility issues or unexpected software failures. This can lead to a loss of productivity as employees struggle to rectify these issues instead of focusing on their core tasks.
- Compliance Risks: Many industries have strict regulations for data management and privacy. The use of Shadow IT can lead to compliance violations, resulting in hefty fines and legal issues.
- Data Loss: Shadow IT can lead to data being stored in unsecured locations, increasing the risk of data loss. The cost of recovering lost data can be high, and in some cases, the data might be irretrievable.
While the costs of Shadow IT can be significant, it’s important to remember that Shadow IT often emerges out of a need for better tools or more efficient processes. Organizations should focus on managing Shadow IT effectively instead of trying to eliminate it.
Tips for Shadow IT Protection
We’ve established that shadow IT poses some vital security and compliance challenges. So, implementing effective measures is crucial.
Here are some practical tips for protecting against Shadow IT risks:
- Create an approval and provisioning process for new software or technologies.
- Conduct regular training sessions and awareness programs to educate employees.
- Implement strict software procurement procedures and regular network audits.
- Develop comprehensive technology policies and guidelines.
- Manage shadow IT in a way that gives IT control and lets employees continue to have the freedom to adopt new tools.
- Keep your organization’s cybersecurity solutions up to date.
- Ensure that access controls are in place for critical systems, applications, and data.
Shadow IT Benefits
Although shadow IT can open the door to many security risks, it’s important to remember that it can potentially benefit your organization. The key is in harnessing its power rather than completely eliminating it.
Remember that shadow IT can enable employees to quickly adopt and utilize tools and technologies that suit their specific needs. They can, for instance, experiment with innovative tools that were not originally in your organization’s roadmap.
Different departments will have unique requirements that may not be fully addressed by centralized IT systems. Shadow IT can allow these departments to find and implement specialized services. So, how can you monitor these applications to ensure you are not sacrificing security?
💡Our blog on IT Governance Best Practices to Manage Shadow IT can help you better understand the topic.
A Simple Tool to Monitor Shadow IT
An alternative to restricting their use is implementing a shadow IT solution to detect and manage applications and their associated risks.
Uniqkey can do this and more.
The key to harnessing the power of shadow IT is to bring it into the light. As part of our business password management solution, Uniqkey offers a detailed overview of all company services, enabling your organization to:
- Know what services your employees are using; monitoring and discovering shadow IT within your organization.
- Spot potential security weak points, identifying vulnerabilities and their potential impact on your business activities.
- Save money on inactive licenses.
Implementing shadow IT tool like Uniqkey can help you adapt and address evolving technology requirements, ensuring you can evaluate all emerging applications and their compatibility with existing infrastructure. Book a free demo today and see how Uniqkey helps mid-size businesses manage shadow IT.