Single sign-on (SSO) has become essential to the modern digital workplace. Since more employees are utilising business resources remotely and working from personal devices, ensuring secure and seamless authentication across all applications is crucial.
The key aim of the Single sign-on is effortless continuity as users effortlessly move between apps, along with centralized control for IT. Now users can shift securely yet seamlessly in the background, thanks to united monitoring protocols. With mindful design, organizations can overcome the integral challenges of deploying reliable and robust systems that feel invisible yet provide enhanced protection. The result is a unified customer experience that allows accessing resources without worrying about the hassle of managing credentials.
In this comprehensive guide on Single sign-on, we will cover everything you need to know about SSO including What is SSO, how it works, different types of SSO, and why organizations are adopting it as a part of their identity and access management strategy.
In this article…
What is Single sign-on?
Single sign-on (SSO) refers to a system that allows a user to authenticate with a single ID and password and access multiple applications once access is granted. The goal of SSO is to remove the need for users to remember several logins and simplify the login procedure.
With SSO, the authentication process is handled by an identity provider (IdP). The IdP authenticates the user’s credentials and gives them a token granting access to all the connected applications. The user only needs to log in once to the IdP to access their authorized apps and websites.
Take a look at the video below for a clear understanding of what is SSO Manager.
The SSO process works like this:
- A user attempts to access an application that is connected to the SSO system.
- They are redirected to the SSO identity provider and asked to log in with their username/password or other credentials.
- The IdP service authenticates the user’s credentials against its user directory.
- Once authenticated, the IdP issues a security token with the user’s details and permissions.
- Back to the initial application, the user is transferred along with the SSO security token.
- The application grants the user access based on the claims in the token.
- The user can now access other connected applications without needing to log in again.
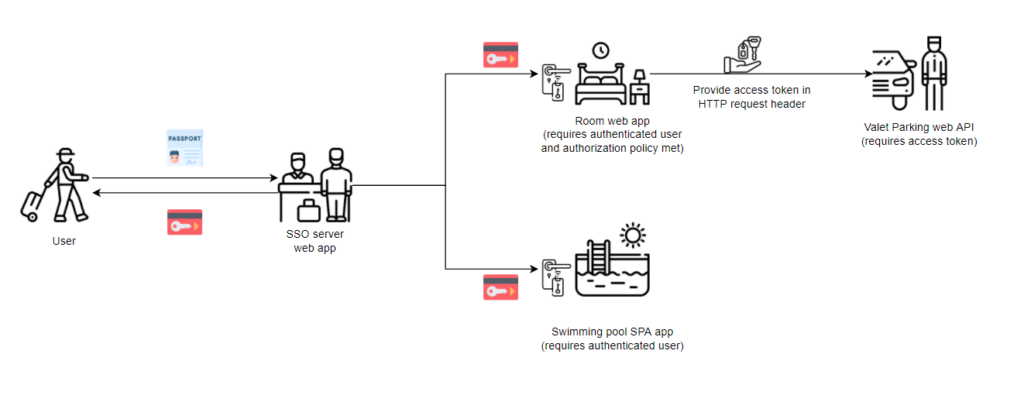
The security token allows the user to access all permitted applications and acts as proof that they have already been authenticated. This avoids the need to log in separately for each app.
Key benefits of SSO include:
- Convenience – fewer passwords to remember
- Security – credentials are exchanged securely
- Productivity – less time spent re-entering credentials
- Compliance – centralized authentication audit trail
- Accessibility – consistent login experience across all devices
Implementing SSO requires careful planning and configuration across the IT environment. Key components needed for SSO include identity providers, federation standards, and access management tools.
We’ll explore common SSO protocols and best practices later in this article. For now let’s understand what are the key elements required for SSO System.
Key elements of an SSO system
While specific SSO implementations differ, some core components comprise a typical SSO architecture:
Identity Provider (IdP) – The IdP is the central authorization server that authenticates user credentials and issues access tokens. Major examples include Active Directory Federation Services, Azure AD, Okta, and PingIdentity.
Service Providers (SPs) – The service providers are the applications and systems users access via SSO. They rely on the identity provider to validate users.
User Directory – The user directory contains user profiles, credentials, access rights, and other attributes the IdP uses to authenticate and authorize.
Single Sign-On Server – The SSO server manages the user’s session and exchange of information between the IdP and SPs to enable seamless SSO across applications.
Access Gateway – The access gateway proxies authentication requests and responses between the IdP and SPs. It acts as a single access point.
Client Software – Client software like a browser plugin may be used to automate SSO and pass credentials.
Now that you have checked out the important parts of SSO systems, we’ll take a look at the different types of SSO protocols designed for various single sign-on requirements.
Types of single sign-On protocols
There are several standard protocols used to enable single sign-on across web applications and services:
SAML (Security assertion markup language)
SAML (Security Assertion Markup Language) is an XML-based protocol used by SSO services to exchange between identity providers and service providers, authentication and authorisation information.
With SAML, an IdP can pass user identity claims to a service provider via a digitally signed SAML assertion. This eliminates the need for users to authenticate again. SAML is one of the most widely used protocols for web SSO.
WS-Federation
WS-Federation defines standards for federated identity management between web services and applications. It uses SOAP messaging to authenticate users and issue security tokens. WS-Federation is built on WS-Trust and WS-Security protocols. It competes with SAML but is less commonly used for SSO.
OAuth and OpenID connect
Access delegation uses the OAuth 2.0 standard and single sign-on focused on authorization rather than authentication. It enables users to authorize access to application services without exposing user credentials.
The identity layer on top of OpenID Connect is developed using OAuth 2.0 providing SSO functionality. It adds login, profile, and discovery capabilities to the authorization protocol. Major identity providers like Google, Facebook, and Microsoft support OpenID Connect.
Shibboleth
Shibboleth is a standards-based, open-source federated identity solution developed for educational organizations. It uses SAML-based SSO and integrates with LDAP directories. Shibboleth also provides extended privacy controls for user attributes.
FIDO
FIDO (Fast Identity Online) is an emerging set of specifications for passwordless authentication supported by the FIDO Alliance. It aims to develop interoperable SSO standards using public key cryptography rather than passwords. FIDO2 introduces WebAuthn for browser-based SSO.
Enterprise SSO
Many enterprise identity management suites like CA Single Sign-on, Oracle Access Manager, and IBM Security Access Manager provide proprietary SSO capabilities within corporate environments. They may support standard protocols like SAML along with added administration features.
Active directory federation services
Microsoft’s Active Directory Federation Services (ADFS) enables SSO by allowing Active Directory identities to authenticate to partner organizations using federation protocols. This provides SSO to cloud services like Office 365 within the Windows ecosystem.
Choosing the right SSO protocol depends on the applications, identity providers, and use cases involved. SAML is the most widely supported standard while OpenID Connect is simple and popular for consumer-based SSO.
With the array of SSO protocols covered, we’ll shift focus to real-world SSO best practices that can optimize single sign-on deployments regardless of the specific protocol adopted.
Single sign-on best practices
Implementing a secure, scalable single sign-on system requires following certain SSO best practices and design principles:
Use federation standards
Standard protocols like SAML, OpenID Connect, and WS-Federation ensure interoperability between identity and service providers. This avoids vendor lock-in and simplifies integration.
Separate authentication from authorization
The SSO server should only authenticate users and provide the authorization credentials. The applications are responsible for making fine-grained access control decisions.
Follow the principle of least privilege
Users should only be granted the required permissions needed to accomplish their tasks. This reduces exposure if credentials are compromised.
Encrypt all traffic
SSL/TLS encryption must be enforced for all SSO communication channels to protect from man-in-the-middle attacks. Along with that security tokens should also be digitally signed.
Support SSO across all devices
A mobile SSO strategy is key for supporting bring-your-own-devices (BYOD). Utilize mobile-friendly standards like OpenID Connect.
Plan for redundancy and high availability
Build redundancy into the SSO infrastructure to prevent the identity provider from becoming a single point of failure.
Audit logs and security monitoring
Closely monitor activity logs to detect attacks and unauthorized access attempts. Logs should consolidate sign-on activity across all applications.
Include user provisioning and de-provisioning
Automate creating and deleting new user accounts from directories to ensure access is properly revoked when users leave the organization.
Conduct training and awareness
Educate end-users on proper SSO protocols and usage as part of ongoing security awareness training.
Regularly test and update the SSO system
Conduct penetration tests, update software regularly, and test failover capabilities to identify and address weaknesses proactively.
Following these guidelines will help maximize the security and reliability of your SSO environment. The specifics will vary depending on the scale, systems, and risk profile of your organization.
Is SSO the preferred choice for identity management?
Let’s explore the key factors that make SSO the go-to solution for businesses looking to streamline their identity management process. By looking at the main reasons behind these preferences, you’ll be able to understand the compiling benefits offered that make SSO the preferred choice of the organization’s Identity management.
Improved user experience
By streamlining authentication down to just a single login ID and password, users gain a much-improved experience accessing multiple applications and systems. As there are fewer credentials to remember, users are relieved from the hassle of remembering passwords.
Enhanced security
The core goal of SSO is centralized authentication and access management which in return leads to enhanced security. Combining
Increased productivity
One of the key benefits of SSO is streamlined access, which saves users time by avoiding repetitive logins. This leads to productivity gain which in turn leads to faster task completion, more engaged employees, and last but not least increased business output as authentication mechanisms don’t constrain the workflow.
Reduced helpdesk tickets
With the use of SSO in the organization, there will be a reduced number of requests for password reset. This will lead to substantially reduced helpdesk tickets. Managing fewer credentials means there is a smaller number of lockouts and access issues. Overall, this reduces the overhead cost of IT support.
Simplified cloud adaption
SSO deployed in organizations centralizes and controls access and makes cloud hosting & remote work seamless. Once committed, IT can easily migrate to another SaaS application and maximize remote user provisioning while maintaining control.
Compliance of standards
SSO helps meet compliance requirements by providing centralized access methods, uniform systems, and audit data collection. SSO can simplify compliance through flexible security controls, granular reporting, and standards support.
CIAM support
SSO can help efficiently control CIAM systems for managing customer and partner access. SSO provides a simple external authentication workflow required for IAM beyond administrators.
Flexible BYOD policies
SSO allows an enterprise to gain secure access from individual devices by centrally managing and providing access. This provides the IT functionality required for easy fetch-your-device configuration on managed and unmanaged devices.
Authentication insight: SSO vs other technologies
Up until now, you understood the need for authentication and authorization and how SSO works to make it hassle-free for everyone. It is important to keep in mind that SSO is one way to do it. There are other ways as well. Let’s break down these methods starting with SAML.
SAML vs SSO: Understanding the primary use cases
SAML and SSO are closely related technologies often used together to provide web single sign-on capabilities. However, they have some distinct differences:
SAML is an XML-based standard protocol between identity providers and service providers, authentication and authorisation information.
SSO refers more broadly to systems and software that provide single sign-on capabilities across multiple applications and systems. SSO is the end goal while SAML is one of the main technologies used to implement SSO.
Some key points about their relationship:
- SAML is the most widely used protocol for SSO implementations, especially for web browser SSO.
- SAML relies on XML for standardized security assertions between identity and service providers in an SSO environment.
- SSO software utilizes SAML to transfer user authentication data, enabling fast and secure single sign-on.
- SAML integrates with SSO identity providers like Shibboleth, Okta, Microsoft ADFS, and Ping Identity.
- SAML-based SSO provides web single sign-on as well as authentication for web services APIs.
- SAML can be used for both Internet-facing SSO and within-network applications.
- SAML provides user authentication for SaaS apps, securing cloud-based SSO.
- OpenID Connect is a popular modern alternative to SAML used in consumer SSO scenarios.
In summary, SAML is the core standard that makes browser-based SSO possible when using a centralized identity provider. SSO software utilizes SAML identity assertions to provide users with that seamless, single login experience. SAML remains the most mature, robust protocol choice for secure web SSO at scale.
With SAML and OIDC use cases clarified, we examine when single sign-on may not suffice and password managers become preferable for managing authentication depending on the situation.
SSO vs password manager: What to prefer and why?
With the growing number of online accounts and services employees must access, single sign-on (SSO) and password manager tools. As both are valuable technologies for managing login credentials. Which solution is preferable depends on the specific use case.
Benefits of an SSO system:
- Enables single login access to web apps and cloud services
- Built-in security using standards like SAML and OAuth
- Better suits access within a corporate network
- Centralized control over application access and permissions
- Automated provisioning/de-provisioning of accounts
- Seamless access across devices with mobile SSO
Benefits of a password manager:
- Access to both business and personal account credentials
- Access from any device and location, more flexible
- Can generate strong, random passwords for better security
- Users can self-manage passwords independently
- Available as consumer apps with useful features like password sharing
For employees accessing software as a service (SaaS) apps and internal web portals within an organization, an SSO platform is usually the best fit. The IT department can manage connected applications and authentication through one centralized interface.
For more secure web access to a variety of consumer applications, a password manager tool such as Uniqkey, may be more suitable and convenient for end users. Employees can install it on their own devices while still keeping corporate credentials separate.
Password managers provide an encrypted digital wallet for all account credentials that integrates across different devices for users who have to juggle both work and personal logins. This expands on SSO’s capabilities for the enterprise.

Finally, we delineate how SSO and 2FA differ in purpose while serving complementary roles that strengthen identity and access security.
🏆If you wish to learn more, we offer a detailed eBook that uncovers hidden risks in SSO and presents effective strategies to fill security gaps inherent in SSO systems.
SSO vs 2FA: Understanding the Main Difference
Single sign-on (SSO) and two-factor authentication (2FA) are two popular security technologies that are frequently used together yet serve quite different purposes.
SSO systems focus on securely streamlining authentication across multiple applications using federated identity standards like SAML and OpenID Connect. This allows users to log in once using a single set of credentials to access many connected systems and web services.
Two-factor authentication offers an extra layer of security on top of standard login passwords. Users of 2FA must verify their identity using something they know (like a password) plus something they have (like a smartphone or security token). This protects against password theft or guessing.
The main differences between SSO and 2FA include:
- SSO simplifies login processes while 2FA complicates them by design to improve security.
- SSO alone does not strengthen actual user authentication, whereas 2FA hardens it significantly.
- SSO handles federating identities across applications; 2FA is app-specific and adds within-app security.
- SSO provides convenience and productivity gains; 2FA provides enhanced defence against account takeovers and fraud.
- This makes SSO and 2FA complementary rather than competing technologies for identity management:
- SSO streamlines login workflows across apps using a single unified authentication framework.
- 2FA bolsters the underlying authentication and account security within that framework.
- Combining SSO convenience with 2FA protection offers users the best of both worlds.
For optimal security, organizations should implement both SSO systems for access management as well as 2FA controls on user accounts accessed via SSO. Together they encompass the concepts of authentication, authorization and accounting (AAA) in a modern identity framework.
With SSO and 2FA clarified, we move on to contrast how SSO and Active Directory fulfil distinct authentication and access needs in enterprise environments.
SSO vs Active Directory: Understanding the Use Cases for Both
Active Directory (AD) and Single Sign-On (SSO) play related but distinct roles when it comes to enterprise identity management:
Active Directory is Microsoft’s directory service for managing users, groups, credentials, policies, and access within Windows environments. It is the core identity store for corporate Windows domains.
SSO refers to systems that allow Using a single piece of login information, users can access different applications.
This provides seamless authentication across web apps, cloud services, and more.
Some key differences and use cases:
- AD is primarily intended for managing identities and access within internal corporate networks and Windows desktops/servers.
- SSO is focused on providing single sign-on capabilities for cloud services, SaaS apps, and non-Windows environments.
- AD handles granular resource permissions for file shares, printers, network resources, etc.
- SSO federates broad identity credentials and attributes for web access.
- AD depends on Kerberos and NTLM protocols. SSO uses standards like SAML, OpenID Connect, and OAuth.
- AD stores on-premises identities. SSO integrates both cloud and internal identities.
- AD sets fine-grained local machine policies. SSO centralizes access policies across apps.
- AD provides the backend directory for Microsoft SSO tools like ADFS.
AD generally handles authentication, authorization and identity lifecycle management within corporate networks. SSO extends these capabilities to cloud services with federated single sign-on and connectivity.
Together they provide comprehensive identity and access management across users, devices, and resources throughout the modern digital workplace. AD acts as the source of truth for identities while SSO federates access.
We shift focus to distinguish SCIM and SSO in terms of their disjoint capabilities for managing identities versus access.
SCIM vs SSO: Everything you need to know as an IT team
SCIM and SSO are two key standards for managing identities in the cloud: SCIM (System for Cross-domain Identity Management) is an API standard that allows easy automation of user provisioning and identity lifecycle management across cloud applications and services.
SSO (Single Sign-On) enables users to log in once and utilize that information to access various applications fast, simple access using federated identity protocols like SAML and OpenID Connect.
Understanding their distinct roles helps IT teams build a complete cloud identity solution:
- SCIM streamlines user onboarding/offboarding by automatically updating cloud app accounts and credentials based on a central user directory.
- SSO provides convenient ongoing access to cloud apps via a single login after initial provisioning.
- SCIM focuses on automating identity provisioning tasks like account creation/deletion, profile updates, and group assignments.
- SSO focuses on access control – authenticating users and federating their credentials across apps.
- SCIM allows connecting on-premises directories like Active Directory to cloud apps for automatic provisioning.
- SSO allows single identity flow across both on-premises and cloud environments.
- SCIM integration is app-specific based on the provider’s implementation.
- SSO systems work across multiple apps using federated standards.
- SCIM helps streamline the challenges of hybrid identity management.
- SSO helps unify and simplify access control for hybrid deployments.
Together, SCIM’s automation and SSO’s seamless access provide the essential pillars of a modern, centralized identity framework across cloud and on-premises systems.
Finally, we survey the landscape of prominent SSO platforms and get a short overview of each.
Leading enterprise single sign-on platforms
For organizations investing in an SSO system, there are a variety of enterprise identity and access management platforms to consider:
Microsoft Azure AD – Azure AD provides SaaS app SSO along with enterprise SSO capabilities leveraging integrations with AD DS. It offers robust access management and reporting features.
Okta Identity Cloud – Okta is a market-leading cloud identity platform tailored for SSO across today’s heterogeneous IT ecosystems.
Ping Identity – Ping offers robust cloud and enterprise SSO with standard support and modular authentication capabilities.
RSA SecurID Access – RSA delivers reliable enterprise SSO, contextual authentication, and secure remote access.
ForgeRock Identity Platform – ForgeRock focuses on CIAM use cases and also supports workforce SSO needs.
IBM Security Verify – Part of IBM’s broader security portfolio, verify provides SSO, MFA, and identity governance.
Duo Security – Duo offers trusted access and SSO for organizations concerned about breaches and data loss.
There are also offerings from CA Technologies, Sailpoint, Radiant Logic, and more. The ideal solution depends on specific requirements, environment, and in-house resources.
In the conclusion
Single sign-on offers today’s businesses significant advantages in terms of security, productivity and convenience. By simplifying applications using federated identity standards, SSO eliminates the frustration of managing endless static logins. Employees like simple authentication processes that put the focus on the business rather than the credentials. IT teams now have visibility and control over access policies and events.
SSO will only increase in importance and value as remote and mobile workers grow. Organizations that implement robust and scalable SSO policies are positioning themselves for the future of identity management.
Even complex hybrid environments can benefit from integrated approaches with proper planning and integration.
Finally, it is worth mentioning that SSO requires ongoing governance and maintenance. However, the enhanced user experience and the continuous improvement in operational efficiencies make it a worthwhile investment.
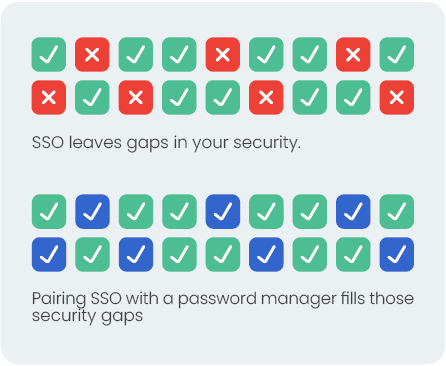
Ideally, organizations should consider implementing Single Sign-On (SSO) for internal applications and obtaining a license for an organizational password manager for other scenarios. Collectively, these tools offer a comprehensive identity management solution, as password managers can address various limitations inherent in SSO systems.