Password-protected accounts are vulnerable to a wide range of attacks. Passwords can be stolen in a server breach, a user can unwittingly share a password with a malicious individual in a phishing attack, or hackers can steal passwords through man-in-the-middle attacks. Add people’s propensity to use the same password for multiple accounts, and passwords start to look like a weak authentication factor. This is where two-factor authentication or 2FA comes into play.
Two-factor authentication requires the verification of something a user knows (a password) and something the user has (a device/ an application) to authenticate their identity. Once a user enables 2FA for an online service they can no longer log into it using just the user name and the password.
After the user enters the credentials into the login portal, the server will move to verify another authentication factor and grant the user access only if the second factor is verified. There are many methods of 2-factor authentication like OTP via SMS, push notifications, security questions, and hardware keys. Time-based one-time password (TOTP) is one of them.
What is a time-based one-time password or TOTP?
A time-based one-time password is a one-time password authentication method that uses time as a tool for preventing duplicity during the authentication process.
That means, not only does the user have to establish the possession of a device or application but also do that within a stipulated time. It significantly increases the challenge for hackers who might try different ways of rigging the 2FA process.
How does a TOTP work for 2FA?
The basic principle of TOTP is very straightforward. The user enters the credentials and the server asks for an additional code. The authentic user can provide the right code and is granted access.
The catch is that the right code changes every 30/60/90 seconds.
The questions are how does it work? and why is it considered a more secure form of authentication when compared to SMS or email-based 2FA?
TOTP authentication process
Time-based one-time password involves the use of an authenticator application. It’s an app that uses the number of seconds elapsed since January 1, 1970, to generate a code every 30 seconds based on a specific protocol.
Here’s a step-by-step breakdown
1. Enablement of 2FA with TOTP
- Once a user opts for TOTP-based 2FA for an online service, the server shares a secret key with the user. This can be in plain text or in the form of a QR code.
- The user shares the secret with an authenticator app like the Google authenticator stored on their mobile phone by scanning the QR or manually entering the key or opting for a more secure & convenient way like Uniqkey where the Uniqkey autofills the code. Once done, the authenticator becomes a party to the secret.
2. Logging into a service with time-based OTP
- The user provides the username and password at the login portal
- The server asks for the OTP
- The user selects the service in the authenticator and it shows the time-based password
- The user has 30 seconds the enter the TOTP to complete the authentication process and gain access to their account.
TOTP: behind the scenes
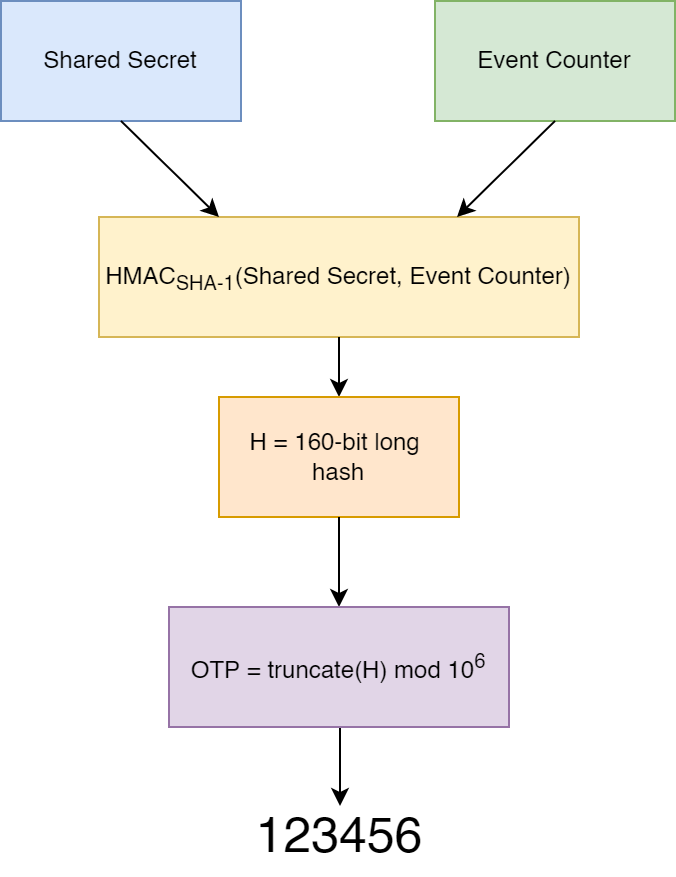
The time-based one-time password improves upon another authentication protocol called the HMAC-OTP or the hash-based message authentication code – OTP algorithm. Understanding how HMAC-OTP or HOTP works will make it easier to grasp the TOTP workflow.
HMAC is an authentication protocol that makes use of an arbitrary hash function like SHA-1. First, we need to understand what a hash function does.
Hash functions
A hash function turns a string input of arbitrary length into a string with a specific length. Hash functions have numerous applications one of which is data encryption. When users create passwords, they are usually turned into hashes using hash functions before they are stored by the server.
A hash has two key properties
- Every unique input has a unique hash and hashes for two different inputs with even the slightest dissimilarity never collide.
- The hash for a specific input will always be the same as long as the same hash function and parameters are being used.
Every time a user enters a password to log into an account, the server turns it into a hash and looks for a hash in its database that matches it. If a match is found, access is granted.
HMAC takes advantage of the key properties of hash functions to create a message authentication system.
How does an HOTP algorithm work?
The HMAC protocol uses a shared secret as an additional parameter to verify the authenticity of the user.
Let’s imagine an individual A wants to prove her authenticity to a server, B. To do that she must send a message, “I am real” to B. Now, A will enter her message as well as a secret code into an arbitrary hash function and the hash output will be sent to B.
B is already aware of the secret code as well as the message but it has to make sure that the right message is coming from the right source. So, B enters the same message along with the secret into the same hash function and then checks if the hash output matches the one shared by A. Thus, using the HMAC protocol, the server ensures that the message hasn’t been tampered with and the source is authentic.
In the case of an HMAC OTP, the secret or the authentication code keeps changing every time a new code is generated. This system ensures that one secret cannot be used twice.
HOTP has a flaw that time-based one-time password addresses
The HMAC-based one-time password algorithm uses turn or the event of code generation to create a secret code.
Now, imagine a phishing attack where the hackers take the user to a replica of a login portal to one of their online accounts.
- The user provides the first factor of authentication – username and password. The hacker steals it and feeds it into the real login portal for the same account.
- The server asks the hacker for the second factor – the secret code. The hacker is prepared with a replica of that dialogue box and shares it with the user.
- The user fetches the code from his device and types it into the fake dialogue box. The hacker takes it and feeds it into the server. Takes over the account.
TOTP uses the current time as an input (Unix time, to be specific) to determine the validity of a secret code. As opposed to the turn-based algorithm, this time-based algorithm generates a new code every 30 seconds (based on the authenticator app and the parameters set by the clients, it can be 60, 90, 120, or 240 seconds).
💡There is more to understand about each authentication method; we have provided a detailed comparison between TOTP and HOTP.
The benefits of TOTP
- By bringing the window between generating a code and logging into an account down to seconds, the time-based one-time password algorithm significantly reduces the possibility of a replay attack.
- It uses the device clock to keep track of time and doesn’t use the internet to generate the code.
- The user does not have to carry a hardware key around for this mode of authentication to work.
- The TOTP is not dependent on cellular network providers so it eliminates the possibility of a cellular hack as well as the inability to log into an account owing to lack of network coverage.
- No text messages are involved in the process
The drawbacks of TOTP
Like every other system of authentication, Time-based OTP has its flaws. Two issues can create both inconvenience and security challenges.
- The secret shared between the user and the server is vulnerable to theft. Unless the secret is stored with appropriate caution by both the client and the server, hackers can steal it and generate the OTP. It surely helps if the TOTP-based authentication system is tied to a zero-knowledge architecture.
- The system is dependent on the device used by the user to generate the OTP. If the device is stolen, it can lead to both a hack and loss of data.
Any application that is built with a security-first approach lets you opt for a TOTP-based two-factor authentication. We at Uniqkey use time-based passwords to manage access to password vaults. With good quality authenticator apps in the market and considering the overall simplicity of the process, TOTP is quite well-accepted among users and servers alike. It surely helps if the TOTP-based authentication system is tied to a zero-knowledge architecture.


