Time-based and HMAC-based OTPs help us securely log into different online services. We depend on them to verify payment information, establish our identity, and secure our password-protected accounts with two-factor and multi-factor authentication systems. This post will examine the one-time password authentication systems, their pros and cons, different methods of OTP authentication, and everything in between.
The origins of one-time passwords
Just as the name suggests, a one-time password is a password that is valid for only one time (or for only a certain amount of time). The concept of OTP dates back to 1882 when Frank Miller conceptualized the one-time pad system for secure telegraphy. Later, in 1919, Gilbert Vernam patented the first OTP system based on teleprinter technology. But that’s all the stuff of history.
OTP, as we know it today, was first proposed in a paper called “Password Authentication with Unusable Passwords” by Leslie Lamport in 1981. Lamport developed the OTP-based authentication system based on a cryptographic hash function that generated a sequence of one-time passwords.
The role of one-time passwords in two-factor authentication or 2FA
Two-factor authentication adds a layer of security to password-protected online accounts. Entering your username and password is not enough for logging into a 2FA-enabled account. The server verifies a second factor – the possession of a particular device, hardware key, or software application – to authenticate the identity of the genuine user. 2FA nullifies the effect of credential theft, credential stuffing attacks, and most forms of phishing. OTP plays a pivotal part in 2FA.
The most common way of verifying the second factor in 2FA is through an OTP. For instance, if I try to make a payment through my credit card on an online platform, filling in my credit card number and other related details is not enough. The server will send me a one-time password to verify that I am the possessor of the mobile number registered to the credit card account in question.
OTP is an essential component of secure logins and it can be used in many different forms. The following section will examine different types of OTPs based on the medium.
Classification of OTP based on the OTP delivery medium
OTPs can be delivered through different mediums. The most popular delivery mediums used to be SMS and email. Now, authenticator apps and push notifications are responsible for a large chunk of OTP deliveries. Nevertheless, SMS OTP is still at the top.
SMS-based & email-based OTP
It works by sending a unique, randomly generated code to your phone via SMS after you enter your username and password on a website or app. You then have to input this code within a limited timeframe to successfully log in. Email-based OTP has a similar functionality.
86.29% of the world’s population uses a mobile phone and hence, has access to text messages. That makes it the most convenient and widely accessible delivery medium for one time passwords. It works as a simple authentication method.
The risk associated with SMS-based OTP
- SIM swapping: Hackers can trick your mobile carrier into transferring your phone number to a new SIM card they control. Thus, they can intercept any OTP that is sent to you. If they gain access to your login credentials or one of your devices where you are logged in, they can easily hijack your account.
- Man-in-the-middle attacks: Text messages may lack transfer layer security and mobile networks can have security vulnerabilities. Sophisticated attackers can intercept SMS messages in transit through such vulnerabilities.
- Malware and spyware: Malicious software on your phone can steal OTPs directly from your device before you even see them.
SMS-based OTPs are also reliant on network coverage, hence lack of cellular connectivity can put you in a tough spot.
Push notifications
Push notifications are messages sent directly to your device (desktop or mobile) by apps or websites, even when they’re not open. They typically appear on the lock screen or in a notification bar.

How does a push notification work in relation to authentication?
- A user initiates login or transaction on a website or app.
- The app sends a push notification to the user’s registered device.
- A notification contains essential details like login attempts, device information, and a “Deny” or “Approve” option.
- The user approves the request with a single tap within the notification.
- The app generates a unique OTP automatically and sends it to the server for verification.
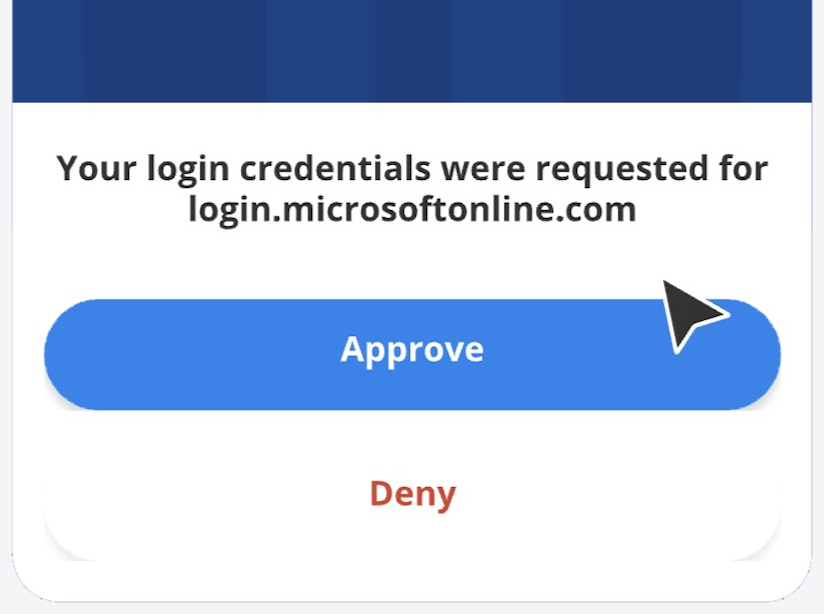
Once the OTP is verified by the server, access is granted to the user. Push notification follows an application-specific delivery and it doesn’t use the mobile network carrier, hence, it is safer and more convenient than SMS-based OTP authentication.
The risk associated with push notification-based authentication
While push notifications offer a safer alternative to text messages, they have some security concerns. Firstly, suppose a user ends up entering their credentials into a duplicate site. In that case, the malicious actors can relay the credentials to the legitimate site and have the authentication server send a push notification to the user. Once the user approves the login, the hackers can gain access to the account.
Similarly, if a server is hacked, attackers can use push notifications to trick users into downloading malware or redirect them to malicious sites.
Hardware key-based OTP authentication
Using a hardware key for two-factor authentication is a very secure method. Here is how it works:
- The user links the hardware key to their account on an online service or website
- The user initiates login by entering username and password
- The server prompts to insert a hardware key, typically into a USB port.
- Hardware key generates an OTP (typically HOTPs) and shows it on its screen
- The user manually enters the code
- The server verifies the code and grants the user access
Hardware key-based authentication is more secure than the other methods covered so far, but there are two issues. One, it is completely reliant on the hardware key which is susceptible to getting lost or stolen. Two, once generated, the OTP stays valid until it is sent to the server, so, a hardware key can be used for a replay attack.
OTP authentication through authenticator apps
This is a method of 2-factor authentication that uses a mobile application to generate one-time passwords (typically TOTPs). Here is how it works:
- The user installs an authenticator app.
- The user opts for authenticator-based OTP while setting up 2FA with the service provider.
- The service provider gives a QR code and a key for setting up the authenticator. The user can use either to link the authenticator to the account.
- The user initiates login by entering credentials
- The authenticator app generates a time-based OTP and the user enters it into the server manually
- The server verifies the OTP and grants access.
The OTPs generated by the authenticator app keep changing every few seconds eliminating the possibility of a replay attack and making phishing extremely hard. The user must be careful not to lose the secret (QR code or key) shared between the service provider and the authenticator. If you lose the authenticator and the secret, you may lose access to your account forever.
Algorithms underlying OTP authentication methods: TOTP and HOTP
So far we have discussed one-time password delivery methods. This section will discuss the process of generating OTPs with a focus on HOTP and TOTP.
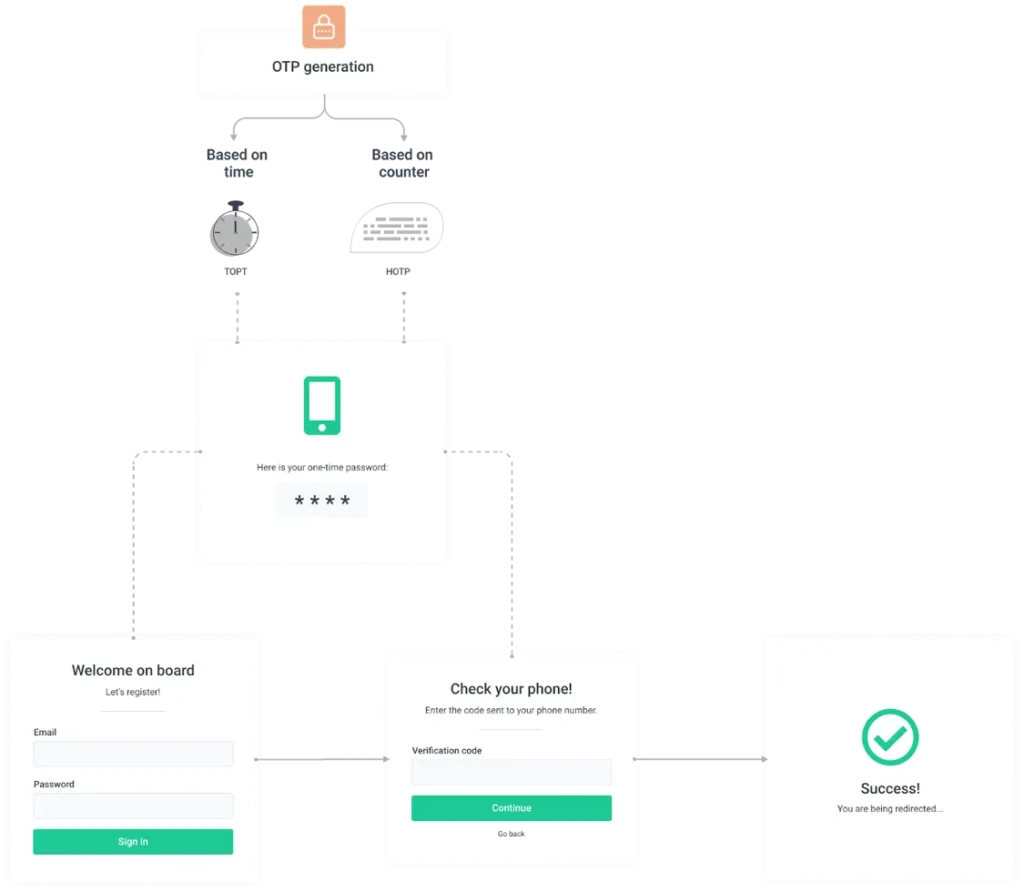
The one-time nature of OTPs is achieved by applying a moving factor to a secret. This moving factor is determined by mathematical algorithms and it is what segregates a one-time password from a static password.
HOTP or HMAC-based one-time password
HMAC stands for Hash-based message authentication code. This system generates OTPs by sending a secret and a moving factor through a hash function. In the case of HOTPs, the moving factor is a counter that increments with each attempt to generate a password.
Therefore, the moving factor changes with every attempt and so does the OTP. One HOTP is valid until the next one is generated or until it is verified once by the server. HOTPs are commonly used in hardware-key-based authentication.
TOTP or time-based one-time password
The time-based one-time password is an improvement on the HMAC-based OTP system. Much like the HOTP, the TOTP is generated by hashing a combination of a secret shared by the user and the server and a moving factor. In this case, time is the moving factor.
It is based on the current Unix time (number of seconds elapsed since January 1, 1970). The time value is calculated by dividing the current time by the time step (time step is the number of seconds for which an OTP is valid – it could be 30s, 60s, 90s, or 240s). This time value is used as the moving factor in the creation of the TOTP.
TOTP is commonly used in authenticator-based OTP authentication. It is considered to be one of the safest and most convenient forms of multi-factor authentication since
- The short window of validity makes phishing very hard
- It is not reliant on the internet or mobile network connectivity for synchronization
- It doesn’t involve additional hardware like a key fob.
We have done a detailed comparison between TOTP and HOTP that will help you understand them better.
The future of authentication
While one-time passwords enhance security, they don’t eliminate the risk of human error, a major factor in data breaches. The evolution of password-based authentication hinges on minimizing this human element.
Uniqkey, with its cutting-edge password and access management solutions, leads this change. Its zero-knowledge architecture authenticates identity seamlessly, while auto-filling 2FA details to shield users from phishing attacks. Experience enhanced security with Uniqkey—start your free trial today.


