Verizon’s Data Breach Investigations Report 2023 shows that “74% of breaches involved the human element.” This human element consists of credential thefts through social engineering attacks, misuse/abuse of privileged access, and weak or repeated passwords, among other things. Weak passwords were a contributing factor to 81% of business data breaches in 2022.
Most, if not all, data breaches caused by human error can be thwarted with better credentials and access management. Applying advanced password management techniques to strengthen a company’s security posture is not very hard.
In this article…
- Focal points of effective password management for businesses
- Set strong password policies and better passwords
- Password encryption for enhanced security
- Apply 2-Factor Authentication and biometric passwords
- Apply Role-Based Access Controls (RBAC)
- Use password managers to maximum effect
- Resetting passwords and having a recovery plan
- 3 Key password management best practices
- Conclusion
Focal points of effective password management for businesses
- Strong and up-to-date password policies
- Password encryption
- 2 Factor Authentication and biometric passwords
- Applying role-based access controls
- Using password management tools to maximum effect
- Password management best practices
Set strong password policies and better passwords
A lot of businesses are still running with outdated password-related concepts. The old-world notions of password-strength focus on the following
Formula: A password needs a certain combination of numbers, special characters, and letters
Expiry: The password needs to be changed frequently
Hint: A site should show hints of the password to the user (this notion has been mostly abandoned)
Special questions: Answer some personal questions to bypass the password authentication
While creating passwords that feature numbers, letters, and special characters is still a valid idea, the focus has to shift toward the length of a password.
Studies have shown that length is the key to a strong password. You can refer to the Password Table by Hive Systems for confirmation of this notion.
A hacker can instantly crack a 6-character password consisting of numbers, uppercase letters, lowercase letters, and special characters. Increasing the password length to 8 characters will take the hacker 5 minutes to crack. Increase the password length to 11 characters while retaining the same character configuration; it will take the hacker 3 years to guess the password.
Bottomline:
Longer passwords you can remember – a phrase as random as 237Apple@zuckerberg&Mango – make impossible-to-crack passwords. The key is not to reuse passwords or even slight variations of the same password. While the expiry factor adds inconvenience (it forces you to reimagine and remember new passwords) it is necessary.
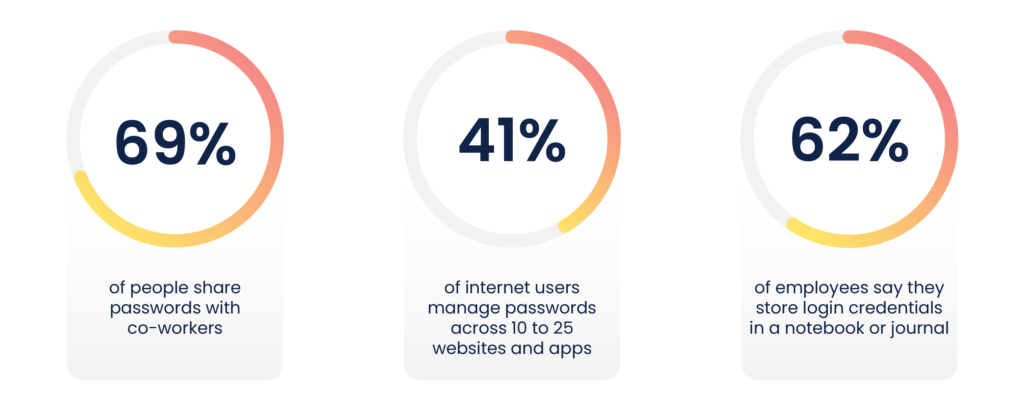
Why is there a tendency to choose weak passwords?
Considering that an average person manages 27-100 passwords (combining their professional and personal usage), it is tough to abide by the standards upheld in the above section. We tend to use easier-to-guess passwords, repeat them, and write them down on easily accessible, often online mediums exposing ourselves to security threats.
When you create a password to sign up for a service, it is stored in a directory or database. Now, if a hacker gets access to the directory and the password is in plain text, they can steal it. The strength of the password would not matter at all. That is why passwords need to be encrypted when stored and transferred from one place to another.
Password encryption for enhanced security
Password encryption is putting a text-based password through a few steps of scrambling so that even if a hacker gets access to the server or directory where the passwords are stored, they cannot use it without the decryption key. Encryption is a key password management technique all password managers use to different degrees.
There are four main types of encryption
Symmetric key: The same key is used to both encrypt and decrypt the data
Asymmetric key: In this case, there are two keys. One is used to encrypt the data, and the other is needed.
Hashed: A computer algorithm changes your password into letters and numbers. A hacker would need access to the algorithm to access the password.
Salted: In this process, a consistent or variable set of characters is added to the beginning and end of a password before it undergoes the hashing process. It adds an extra layer of security as the hacker would need access to both the hashing algorithm and the added set to access a password.
You can learn more about how password encryption works and different methods of encryption.
Encryption delays a hacker – it makes it harder for them to get hold of credentials and encourages them to quit and look elsewhere for an easier target. In a targeted attack, chances are they’ll eventually get hold of the passwords. Your account can still be saved if you have 2-factor authentication enabled.
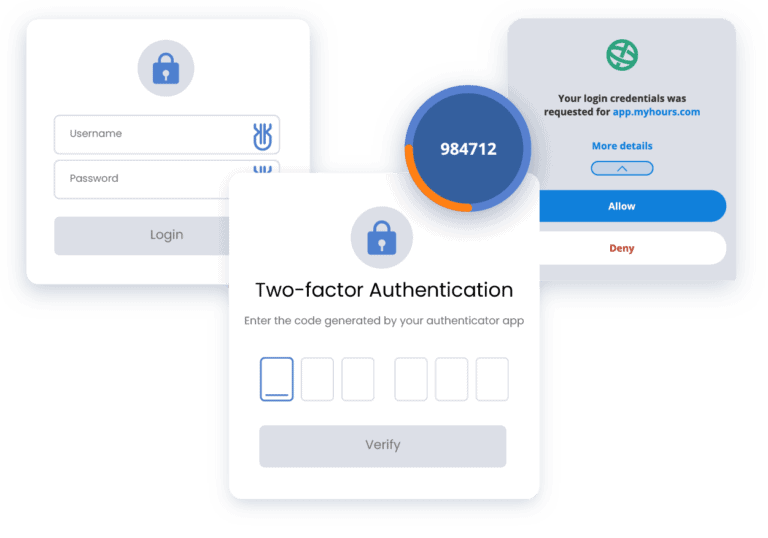
Apply 2-Factor Authentication and biometric passwords
2-factor authentication or 2FA, leaves out inherence and combines the two other authenticators to create a more secure authentication process. That means the login credentials are not enough to get inside a 2FA-enabled account. You also need to possess a device as additional proof of authenticity.
2-factor authentication has various types. It can be achieved through SMS, push notifications, time-based one-time passwords, and a physical key. Not all of the 2FA processes are created equal. Some are more secure and some are more user-friendly.
Check out this spot for a detailed, easy-to-understand look at 2FA and its different kinds.
Biometric passwords make use of the third authenticator, i.e. inherence, or something you are. Biometric information like fingerprints, retina patterns, and voice characteristics can be used to identify an individual and grant them access to certain information.
In 2022 an organization was using 130 SaaS applications on average. Businesses are forced to share sensitive data with a lot of these applications for functional purposes. Each manual login is a risky event, each attempt to reset a password manually is a risky event, and every app that sits with pending updates is a security threat. Amidst conditions like that, it is only fair that employees have access to only what they need. That’s where RBAC or role-based access controls come in.
Apply Role-Based Access Controls (RBAC)
Imagine a password vault that has credentials for tools used by the marketing team, the sales team, and the developers. If the marketing and sales teams don’t require access to the developers’ tools, they shouldn’t have access to the passwords by the principles of RBAC.
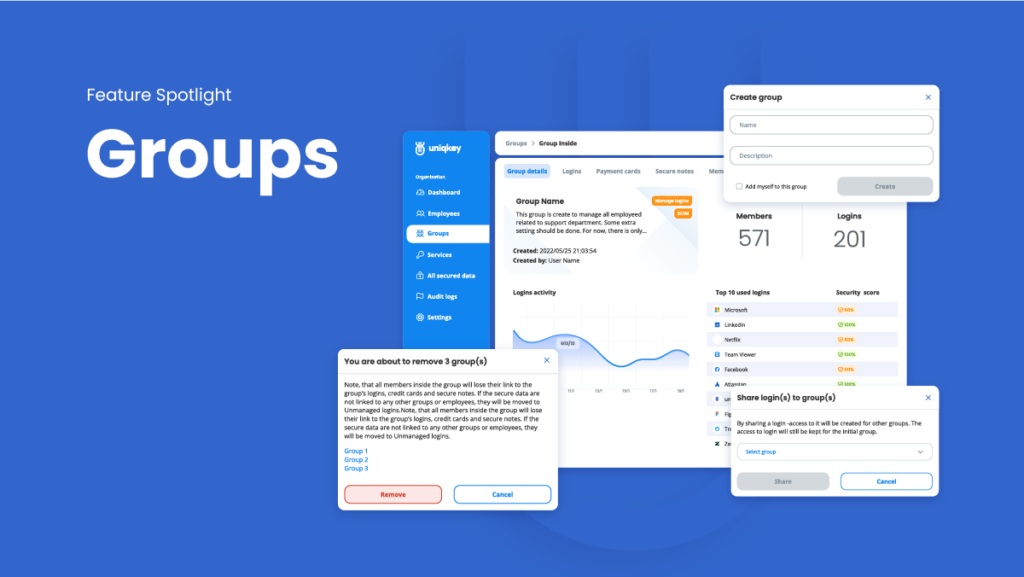
Role-based access control (password groups) proposes that access is granted based on need and revoked when the need is served. Applying RBAC is a crucial part of a wholesome password management strategy.
As you can see, a lot goes into the successful management of passwords. Doing it manually is a painful endeavour almost guaranteed to end in disaster.
- Employees tend to use weak passwords so that they’re easier to remember.
- There is widespread disdain for 2FA processes citing workflow disruption.
- Every time they enter their passwords manually, there’s a risk of phishing.
That’s where password managers come in.
None of the above techniques for secure password management sufficiently address the most pressing security issue – human error. We’re often in a hurry to access our work accounts. It’s unfair to expect that an employee trying to finish their job as fast as possible would be vigilant about phishing attempts every time they try to log into a service. A password manager is the solution.
Use password managers to maximum effect
A password manager is a vault to store all your passwords, and it is much more. It helps you tackle all password-related pain points imaginable.
Once you start using a password manager,
- You do not have to remember passwords
- The password manager worries about encryption
- The risk of sharing credentials on a phishing site is reduced manifold
- All you need to protect and remember is the master password
Here’s how to use a password management tool for maximum benefit
- Choosing a password vault with auto-login
Any good password manager will provide you with a password vault that your team can share (depending on the level of access granted to each individual).
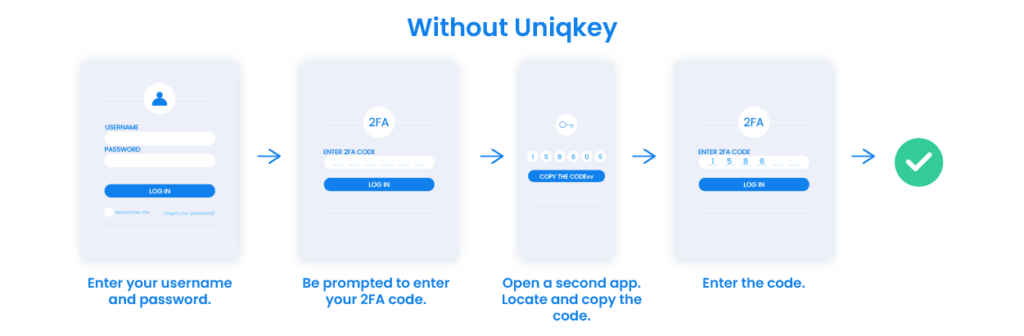
Auto logins significantly increase user inconvenience. Instead of logging into the password vault, users can simply request a login and receive it on an authenticated application – mobile or desktop.
Automatic login has two crucial benefits:
- Employees can log into work tools and apps 300% faster, bypassing the hassle of fetching and entering credentials.
- The IT team doesn’t have to burn resources to reset passwords.
Some password managers, like Uniqkey, go the extra mile and auto-fill your 2-factor authentication OTPs to reduce the time lost in the login process.
- Allot separate vaults for work and private credentials
With the culture of “bring your own device” on a song, the security of an employee’s personal systems has become very important for businesses. Using a password manager to segregate work-related and private credentials while securing both can be a masterstroke.
- Generate strong passwords
A password manager is capable of generating long and strong passwords that are virtually impossible to brute force. We’ve already discussed the importance of having strong passwords. When you can automate creating, filling, and remembering passwords, things become much easier. You can work faster, stay safer, and worry less about credential theft.
All password managers are not created equal. Some use weaker encryption, some have even been accused of selling data to third parties, while some are just unreasonably costly. It’s important to choose the right one for your specific needs.
Is it wise to trust password managers with your credentials?
Most password managers use zero-knowledge technology. That means they encrypt your passwords on your device before sending them to the server. The only way the passwords can be accessed is by using the master password known only to you. If you lose it, even the support teams of the password management tool can’t help you access your credentials.
By now, you know what to look for in a password manager.
Uniqkey checks all the boxes and stores all your data locally on your mobile device; thus, it’s hard for hackers to decrypt passwords.
Resetting passwords and having a recovery plan
Despite all the precautions, credentials can be stolen, and they can end up being on sale. There are password management tools that can alert you in such situations. The threat of credential theft makes it so important for businesses to reset their passwords frequently.
Losing your master password after storing your password with a password manager may cause you to lose all passwords behind a wall of encryption. Some password managers offer you a recovery key for such situations. Others do not. In other situations, you may require a plan for password recovery as part of your password management strategy.
3 Key password management best practices
We’ll delve into the three crucial best practices for managing passwords effectively for businesses and enterprises. These strategies, backed by industry experts, can bolster your organization’s cybersecurity, prevent unauthorized access, and maintain the integrity of your sensitive business data. Implementing these practices will ensure a robust and secure digital environment for your business operations.
1: Use password managers dedicated to business
Utilizing a business-oriented password manager streamlines operational efficiency and addresses key security protocols effectively.
By significantly reducing the scope for human error, it helps mitigate the potential business risks associated with data exposure and credential theft. This strategic move can, in turn, enhance trust among your stakeholders and reinforce your organization’s reputation for stringent security measures.
2: Lock users out of password-protected areas after multiple failed attempts
It’s important to limit the number of times an individual can make failed attempts to access a password-protected area. Some businesses add an extra layer of security by adding CAPTCHA and IP “whitelists”.
3: Passwords should be long and not common
The focus should be on the length of a password and not its complexity. It is also important that commonly used passwords are automatically rejected.
For more in-depth guidance, we’ve also compiled a ‘Password Checklist: Protect Your Business from Breaches.’ This checklist provides a structured approach to secure password management, enhancing your business’s security posture. We invite you to explore this resource for further insights and strategies.
Conclusion
When a hacker gets their hands on a set of passwords and email IDs, they’ll try all combinations everywhere to find one place where a combination clicks. Even with sophisticated password-cracking programs and brute forcing techniques, hacking through stolen passwords depends heavily on our carelessness.
Hackers will have nothing to take advantage of if we decide to apply strong password management techniques – not to use a password in two places, create long and strong passwords, and use a decent password manager.
With Uniqkey, a business-focused password manager, you can say goodbye to the hassles of managing your credentials. Experience the value and efficiency of our solution first-hand with our 14-day risk-free trial. Start your journey towards stress-free password management today.


