Both 2FA (Two-Factor Authentication) and MFA (Multi-Factor Authentication) are security measures commonly used to provide additional protection to digital accounts and systems. While similar in function, though, these two terms are not the same.
In this article, we will clarify the distinction between 2FA and MFA, go through each authentication method in detail, and explore a few use cases so you can understand why they matter to individuals and organizations.
Understanding Authentication
Authentication refers to the process of verifying the identity of a person or entity that is trying to access a digital system, service, or resource. In other words, this technology is designed to ensure the actor claiming to be a specific user is indeed who they say they are. This is particularly important in today’s world because 81% of security breaches are still caused by weak or stolen passwords!
Authentication is critical to securing digital systems because it can help systems verify someone’s identity before they can access sensitive information. Consequently, it can prevent malicious actors, hackers, or intruders from impersonating legitimate users and gaining unauthorized entry. On top of enhancing cybersecurity, authentication also contributes to accountability within digital systems because it can track and monitor user activities, ensuring that actions can be attributed to specific individuals.
There are three main types of authentication factors:
- Something You Know (Knowledge Factor): This type of authentication factor relies on information that only the expected user should know. For example, passwords, PINs (Personal Identification Numbers), or answers to security questions.
- Something You Have (Possession Factor): Possession factors involve physical objects or devices that users possess to authenticate their identity. Common examples include smart cards, security tokens, or mobile devices used for Two-Factor Authentication (2FA).
- Something You Are (Inherence Factor): Inherence factors authenticate users based on their unique biological or behavioural characteristics. Biometric authentication relies on physical traits such as fingerprints, facial recognition, iris or retina patterns, voice recognition, or even DNA.
Comparing 2FA and MFA
Selecting the appropriate combination of authentication factors depends on the system’s sensitivity, user experience considerations, and the level of security required. So, let’s look at the main differences between 2FA vs MFA in some more detail.
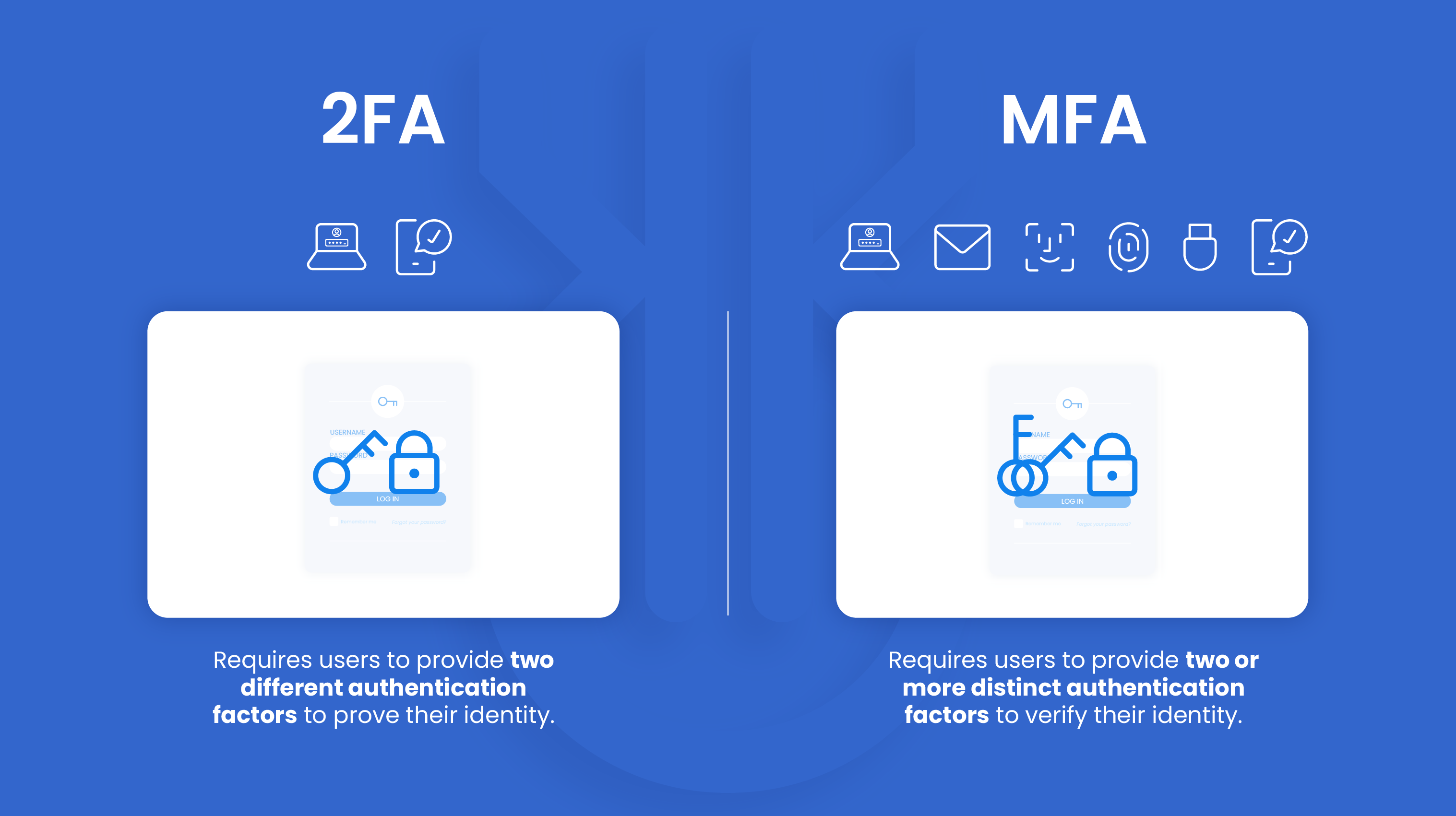
What is Two-Factor Authentication (2FA)?
2FA, or Two-Factor Authentication, is a type of verification that requires users to provide two different authentication factors to prove their identity. Typically, these include a password or PIN and a smartphone or hardware token.
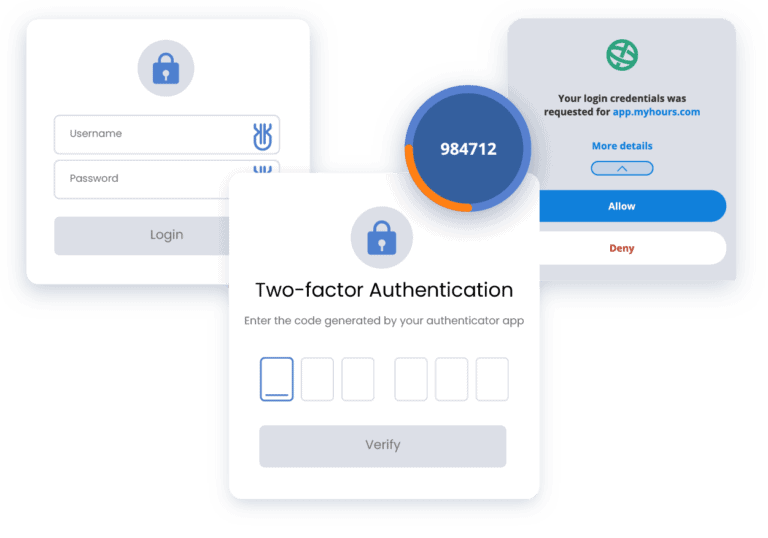
Let’s see an example of 2FA. Suppose you want to log in to your online banking account. With 2FA enabled, the process would look like this:
- First, you will be required to enter something you know, such as a username or password.
- After entering your credentials, the system will ask you for a second authentication factor; for instance, a mobile device app that generates a unique, time-based code.
Once you have successfully entered both factors, the system verifies their validity and grants you access to your online banking account.
This technology offers many advantages. For one, 2FA adds an extra layer of defense that goes beyond passwords, making it more difficult for unauthorized individuals to gain access to sensitive information. Even if your password credentials do get compromised, the additional factor will reduce the chance of a breach.
However, 2FA has its limitations, too. Mainly, you will need multiple devices or channels (such as a smartphone or security key generator). If you lose or damage your device, you might have trouble accessing your account. 2FA is also susceptible to phishing attacks and other forms of social engineering, where attackers attempt to trick individuals into revealing their codes.
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication (or MFA) requires users to provide two or more distinct authentication factors to verify their identity before accessing a digital system or service. Thus, it adds multiple layers of protection, making it more difficult for unauthorized individuals to gain access to sensitive information or systems.
We mentioned the three factors authentication uses above (something you know, something you have, and something you are). By combining these factors, MFA strengthens security because it requires attackers to possess more than just a single piece of information or device to gain access.
MFA is commonly implemented in various systems and services, such as online banking, email accounts, cloud platforms, and social media.
For example, email service providers also commonly offer MFA to safeguard users’ email accounts. After entering their username and password (knowledge factor), users may be prompted to provide a second authentication factor, such as a verification code sent to a mobile device via SMS or one generated via an app.
These additional factors (which have, in fact, grown to include advanced methods like location-based authentication or behavioural analytics) provide further security measures and flexibility in choosing the most appropriate authentication methods for different scenarios and against different attack vectors. However, implementing Multi-Factor Authentication can be complex and requires several steps, especially if you have a large organization. Some users might also find the process difficult to learn or cumbersome.
The Difference Between 2FA and MFA
Having various authentication factors (as opposed to single-factor authentication, such as a simple password) adds an extra layer of security, making it more difficult for unauthorized individuals to gain access. However, 2FA only involves exactly two authentication factors. MFA, on the other hand, uses many. So, 2FA can be considered a subset of MFA.
Both 2FA and MFA enhance security by reducing the reliance on passwords alone and adding extra verification measures to protect against security threats.
Organizations will typically choose between 2FA and MFA based on their security requirements, user experience considerations, and the level of protection needed for their digital assets:
- Security requirements: MFA provides an extra layer of protection compared to 2FA, making it suitable for high-security environments.
- User experience: 2FA typically involves two steps during the login process, while MFA may involve additional steps or requirements.
- Cost and implementation complexity: MFA may require additional hardware, software, or infrastructure investments compared to 2FA.
- Compliance and regulatory requirements: Certain sectors, such as finance, healthcare, or government, may have specific guidelines regarding authentication methods.
- Risk profile: Higher-risk scenarios may warrant using MFA to provide stronger defense against sophisticated threats and reduce the risk of successful unauthorized access attempts.
- Scalability and flexibility: Evaluate the compatibility of the authentication solution with different platforms, devices, and user environments.
Why Are 2FA and MFA Important?
Overall, authentication is crucial for securing digital systems by verifying user identities, preventing unauthorized access, protecting data, ensuring accountability, and meeting regulatory requirements.
In today’s threat landscape, Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) have become increasingly significant in safeguarding digital systems and protecting sensitive information.
By implementing robust authentication mechanisms, your organization will be able to strengthen its overall security posture and mitigate the risks associated with unauthorized access and data breaches.
How to Choose the Correct Authentication Method for Your Company
You should carefully evaluate each authentication factor’s strengths, weaknesses, usability, and potential risks to implement a robust and balanced authentication mechanism.
Ultimately, the choice between 2FA and MFA depends on your company or application’s specific requirements, risk tolerance, user experience considerations, and available resources.
A thorough assessment of these factors will help determine the most appropriate authentication approach to balance security, usability, and operational efficiency. For instance:
- Assess the level of security required for the specific application or organization, evaluate the sensitive data or systems being protected, and determine if additional factors beyond 2FA are necessary to meet the security needs.
- Consider the impact on user experience when implementing authentication measures and evaluate the user base, their technical proficiency, and the potential inconvenience of additional authentication factors.
- Assess the cost and complexity of implementing and maintaining the chosen authentication method. Consider the resources, budget, and technical capabilities available to implement and support the chosen authentication approach.
- Take into account industry-specific regulations and compliance requirements and ensure the chosen approach aligns with applicable standards and regulations to maintain compliance.
- Evaluate the organisation’s or application’s risk profile considering the potential threats, attack vectors, and the likelihood of targeted attacks.
- Keep the scalability and flexibility of the chosen authentication method in mind. For example: Will it accommodate the growth of the user base or changing business needs?
When Should You Use 2FA or MFA?
2FA involves using two different factors to authenticate a user’s identity. When you want to enhance the security of your online accounts, such as email, social media, or financial platforms, 2FA is a practical choice. If you’re looking for a relatively simple and accessible authentication solution without the need for additional hardware or a complex setup, 2FA is a suitable option.
MFA goes beyond 2FA by adding additional factors for authentication. In situations where the protection of sensitive data is paramount, such as accessing corporate networks, confidential databases, or highly regulated systems, MFA provides an elevated level of security. Organizations in sectors like healthcare, finance, or government may also have specific compliance obligations that necessitate the implementation of MFA as a security measure.
In short, 2FA strikes a balance between security and user convenience, while MFA adds an additional level of confidence and protection.
The Future of Authentication
2FA and MFA are essential in today’s threat landscape to mitigate password-related vulnerabilities, prevent account takeovers, and meet compliance requirements. However, authentication methods are constantly evolving to address emerging threats and improve user convenience.
Two notable trends are behavioural biometrics and risk-based authentication.
Behavioural biometrics is an authentication method that analyzes unique patterns of user behavior to verify their identity. It leverages characteristics such as keystroke dynamics, mouse movement, typing rhythm, and touchscreen gestures to create a user profile – something particularly difficult to replicate accurately.
Risk-based authentication, on the other hand, considers contextual information and risk factors associated with each authentication attempt. For example, it analyzes factors such as location, time of access, device information, IP address reputation, and user behavior to assess the level of risk.
These emerging trends in authentication aim to enhance security while improving user experience. Ultimately, the goal is to move away from static and one-size-fits-all approaches, introducing intelligent and context-aware authentication mechanisms to enhance security and provide a more seamless experience.
Are you looking for a simple password management solution for businesses?
Uniqkey automates the two-factor authentication process and offers biometric authentication to reclaim IT control and reduce cyber risk.